揭示互联网暴露资产存在的高风险漏洞并予以及时修复,从而有效防止数据泄露、罚款和停机。
基于风险的漏洞管理
优先处理对您构成最大风险的漏洞。
揭示互联网暴露资产存在的高风险漏洞并予以及时修复,从而有效防止数据泄露、罚款和停机。
洞见每个互联网暴露资产以及整个组织攻击面上存在的相关风险漏洞。 无代理监控可发现传统检测工具无法识别、以及安全团队通常不会监控的资产——例如被忽视的 QA 环境和被遗忘的营销网站。
此外,Ivanti Neurons for EASM 通过持续监控,确保近乎实时地掌握资产动态,使您能在现有资产暴露或新资产部署时立即知晓并采取相应措施。

利用有关外部攻击面风险漏洞情况的实用情报来确定在何处开展修复工作。
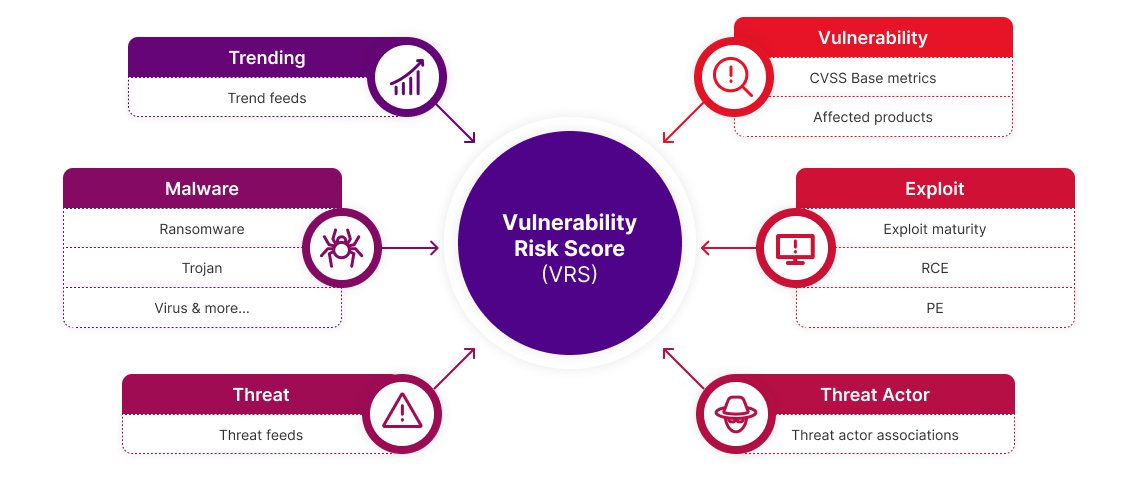
情报包括 Ivanti Neurons for EASM 发现的每个 CVE 的漏洞风险评分 (VRS)。 VRS 使安全团队能够量化漏洞带来的风险并了解其威胁背景,从而制定明智的决策。

满足高级别安全领域利益相关者的报告要求,并通过 PDF 报告帮助对潜在收购、合作伙伴和供应商进行尽职调查。 这些可导出的报告全面梳理和盘点与组织外部攻击面相关的风险漏洞。

利用 Ivanti Neurons 的强大功能来弥补 Ivanti Neurons for EASM 所发现的重大攻击面缺口。将 Ivanti Neurons for EASM 与以下产品结合使用,从而能够最快速地应对那些影响对外暴露资产的问题:

Ivanti Neurons for EASM 为每个识别的漏洞分配一个漏洞风险评分 (VRS),该评分通过汇总反映漏洞在特定环境中影响程度的一系列属性来加以确定。
Ivanti 提供一系列其他基于风险的解决方案。
有问题? 联系我们的团队。
Ivanti Neurons for External Attack Surface Management (EASM) 是一款基于云的应用,利用无代理监控发现所有互联网暴露资产,包括传统发现工具难以检测的资产。它可提供可操作的暴露与风险情报,帮助优先处理最高风险的暴露面。
Ivanti Neurons for EASM 主要功能:
Ivanti Neurons for EASM 的价格根据您组织的资产数量而定。如需报价,请**联系销售团队**。
Ivanti Neurons for EASM 可发现所有互联网暴露资产(包括安全团队通常未监控的),查找相关漏洞,并自动优先排序促使快速修复。