Why You Should Be Paranoid About Data Center Security and How to Prepare for the Inevitable
As Ivanti prepares to infiltrate booth #2839 at VMworld 2018 in Las Vegas, August 26–30, I find myself reflecting on urban legends.
Yes, you read that right. And, no, VMworld isn’t an urban legend. It’s as real as the extra poundage I bring back with me from Vegas through fine dining and quality outlet malls.
Just bear with me here. My brain is a labyrinth.
I’m thinking about security and virtual environments—and paranoia. And, yes, urban legends. Specifically, the fact that I’ve given up on being THAT person who always points out when stories my friends share on social media are in fact not real events to be concerned about at all but urban legends. Nobody seems to care when you tell them that—they’ll tell you it’s good to be cautious—but they should care. They should for the very reason I’m thinking about urban legends now—because focusing on threats that aren’t real takes away from your ability to focus on the ones that are.
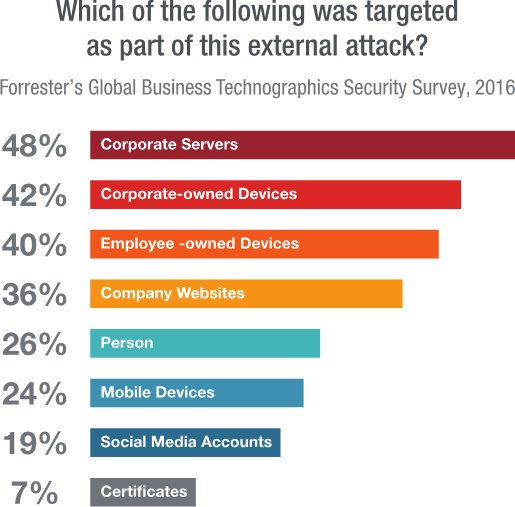
So, where are the real threats today? As you prepare for your foray into VMworld, that’s something worth thinking about. And I have an answer for you: They’re in the data center. For its 2016 Global Business Technographics Security Survey, Forrester surveyed 192 network security decision-makers whose firms had an external security breach in the past 12 months (1,000+ employees). The results showed definitively that it’s the clients and servers in your network that need to be your primary focus—not the perimeter of your IT environment. And at the very top of that list? Corporate servers. Those are the primary vectors for an attack.
Nothing has changed in 2018, either, according to one of the most respected annual reports in the security industry: the Verizon Data Breach Investigations Report (DBIR). The Verizon RISK team found that database servers top the list of corporate assets involved in breaches.
The data center is the lifeblood of the organization and also where a great deal of personal and corporate data is stored. Security practices must include solid server security controls to help keep servers hardened, data secure and available, and the business’s reputation intact.
Here’s just one example why. In the recent past, Kaspersky Lab researchers, working with a European ISP, discovered trading forum xDedic was providing access to more than 70,000 hacked servers in 173 countries—for as little as $6 apiece. Buyers could use the servers to launch denial-of-service attacks or blast out spam and malware. They could steal stored credit and debit card numbers, confidential email correspondence, or other valuable information. Or they could use the systems as jumping-off points to compromise other systems on that network. Because these weren’t just any servers. They were Remote Desktop Protocol servers, which administrators use to connect to and administer Windows systems on a local network. An attacker with access can connect to other systems, including web servers—often with administrator-level privileges.
In today’s world, where hackers can get their hands on pre-written exploit code with a snap of a finger and no longer need to be an expert in cyber crime to attack an organization, those organizations need an effective means to protect their data centers when they can’t afford the expertise of a Red Team or SecOps Team. And when they plain don’t want to exhaust their IT resources on data center security projects when there are core business initiatives to rally around.
So, Where Do You Go From Here?
Let’s go to the source: your users. Together, endpoints and your employees are the weakest links in your organization. For example, in 2017 the Verizon RISK team concluded that phishing—a message typically sent through email and meant to get the recipient to click on a malicious attachment or link—is used in more than 90 percent of security incidents and breaches. Similarly, in 2018 they found email continues to be the most common vector for breaches—walking away with a staggering 96 percent of the blame.
Here’s a quick overview of a three-pronged phishing attack:
- The user receives a phishing email with a malicious attachment or a link pointing to a malicious website.
- That user clicks and downloads malware, which targets known software vulnerabilities attackers can use to look for secrets and internal information, steal credentials to multiple applications, and/or encrypt files for ransom, for example.
- The attackers can also use stolen credentials for further attacks: for example, to log into third-party websites like banking or retail sites.
How can security and IT pros protect their organizations from the perils of nefarious attacks likes these that are designed to have a critical impact? Focus on what actually matters—strategically. Direct your scarce resources to actions with an immediate and high-value payoff, and then focus on additional risks unique to your business.
Cyber watchdogs like the Center for Internet Security (CIS) agree, and are contributing their knowledge and expertise to identify, validate, promote, and sustain the adoption of cybersecurity's best practices. Derived from practices forged from actual experiences at the NSA, the CIS Controls both support and reflect many of the other leading sources of cybersecurity guidance.
So, what’s at the top of the list?
Inventory and Control of Hardware and Software
First, you need to actively manage (inventory, track, and correct) all hardware and software, so that only authorized devices are given access and only authorized software is installed and can execute.
Patch Management
Your security practices must also include server patch management to patch the vulnerabilities attackers are looking to exploit. And when most reported vulnerabilities come from third-party apps, you need a strategy that extends beyond the server OS.
Booth #2839 at VMworld is the perfect place to find out how you can make patch management easier. We’ve got the goods: consistent, automated, cost-effective patching for data centers.
- Powerful discovery capabilities
Don't fear the unknown or fall victim to it. Find physical and virtual systems, scan for missing patches, and deploy them.
- Comprehensive patch management
Time and budget concerns lead many to ignore the virtual data center environment—taking on a great deal of risk. Focusing solely on physical servers leaves the business exposed and in danger of failing an audit. Other organizations juggle separate tools to patch physical and virtual servers—taking on the extra time and resources and increased risk of human error that such an approach entails.
We can help you automate patching for the OS, third-party apps (including the most vulnerable software titles), physical and virtual servers, and systems that aren't always connected. Keep even offline virtual images in a constant state of readiness to be deployed. Because you don’t want to go through the two-step process of creating a VM and having to patch it. If offline templates are kept current all the time, you can deploy rapidly without having to worry about whether the VM’s up to date.
- Real-time dashboard reporting
We also simplify compliance and cut through the mass of information across your environment to the critical insights that matter—helping you make smarter, faster security decisions with ease. Turn reporting into a checkbox, with data on demand and the ability to easily create new dashboards and reports to get the right kinds of data into the hands of executives, directors, and line-of-business (LOB) and application owners.
Application Control
But, what about the apps you can’t patch—because you’re running legacy systems, for example, or you have concerns that patching will break something in your environment? It’s time for another layer of security in the data center. You need to block unauthorized apps—and protect against zero days while awaiting a patch for those unheralded nasties that can blindside organizations. Ivanti Application Control allows authorized access to server applications, services, and components, without making IT manage extensive lists manually and without constraining users. Additionally, IT can check file metadata – including vendor, certificate, publisher, version, and more – to ensure applications, components, and scripts are original and are preventing modified or spoofed applications from executing.
Come see us at booth #2839 to learn more about the ways we simplify application and systems control.
Privilege Management
Don’t forget the admin privileges. Remember, attackers can use stolen credentials and that user’s admin rights to spread further into your network. As such, privileged accounts are prime targets for exploitation. Providing full admin rights on a server creates multiple risks, like the ability to start or stop services and install or remove software in error. By removing full admin rights from users and providing them with elevated privileges for just the tasks they need for their job, you can simplify endpoint security, reduce support calls, and lower TCO. Or you can take that full administrator and strip away the things they should not have access to. Take PowerShell away, or access to specific capabilities. Limit administrative privilege to specific consoles, applications, services, and commands, reducing the risk of admins introducing malware, halting essential services, or affecting performance of mission-critical services.
What About the Desktops?
I’d like to close with a shout out to endpoint security on the desktop side.
The Verizon 2018 DBIR makes it clear that attacks across your server and workstation environment are on the rise—and could be responsible for as many as half of all enterprise data breaches. Don’t overlook security at this level. We certainly don’t. While I’m calling attention to risks in the data center here, feel free to take a quick look under the desktop hood with us at booth #2839 and talk about the dangers lurking there and the ways in which our solutions are tailored to mitigate cyber threats in that space.
