Risk Appetite, CRQ and Exposure Management: Closing the Loop on Cyber Risk
Key Takeaways
- Cyber risk quantification, risk appetite and exposure management can work together to create a closed economic and operational feedback loop for business leaders.
- Cyber risk quantification enables executives to compare cyber investments to any other capital decision.
- A risk appetite statement explicitly codifies risk capacity, tolerance and hard limits to align decision-making across all departments.
- Exposure management adapts continuously to the organization’s defined risk appetite by combining attack surface management, risk-based vulnerability management, and validation and remediation.
Executives today operate in a constant state of pressure. Regulatory demands grow faster than budgets, customers expect proof of resilience and every system outage becomes a business event. When each function manages risk in isolation, leaders spend more time reacting than advancing strategy.
The real issue is coherence. Most organizations still rely on partial instruments: dashboards filled with red and amber, but no clarity on which risks matter or what an outage would actually cost. Anyone updating risks once a year in a spreadsheet is flying the enterprise through fog without instruments. Cyber risk quantification (CRQ) brings those instruments in the form of credible metrics, realistic scenarios and ROI-based priorities.
But measurement alone isn’t enough. Risk appetite defines how much uncertainty an organization is willing to accept; exposure management operationalizes that boundary. When CRQ, risk appetite and exposure management operate together, risk becomes a controllable variable — a closed loop that ties monitoring to strategy and action.
The result is a system that reduces noise, sharpens priorities and enables leaders to balance security, profitability and innovation. And while measurement by itself is insufficient, it is the crucial first step for IT leaders.
Why measurement is the first act of leadership
You cannot manage what you cannot measure. A single “critical” label might conceal a $50,000 nuisance or a $5.4 million disaster. Without quantification, leadership decisions rely on instinct dressed up as process.
Measurement is the first act of control. When risk is expressed in financial terms (e.g., probability of loss, potential impact, return on mitigation) security becomes a business function rather than a technical debate. It re-enters the language of value, cost and return. Investors and boards increasingly judge resilience as an indicator of governance maturity. Quantified risk doesn’t just support better posture — it stabilizes valuation and reinforces confidence in executive judgment.
Cyber risk quantification (CRQ): Turning guesswork into dollars
Cyber risk quantification provides the translation layer that business leaders need. It models what a specific threat could cost in dollars, how likely it is to occur and which factors amplify or reduce exposure. Inputs include internal metrics (e.g., production revenue per hour, contractual penalties, data-handling costs) augmented by actuarial models, such as those from Munich Re.
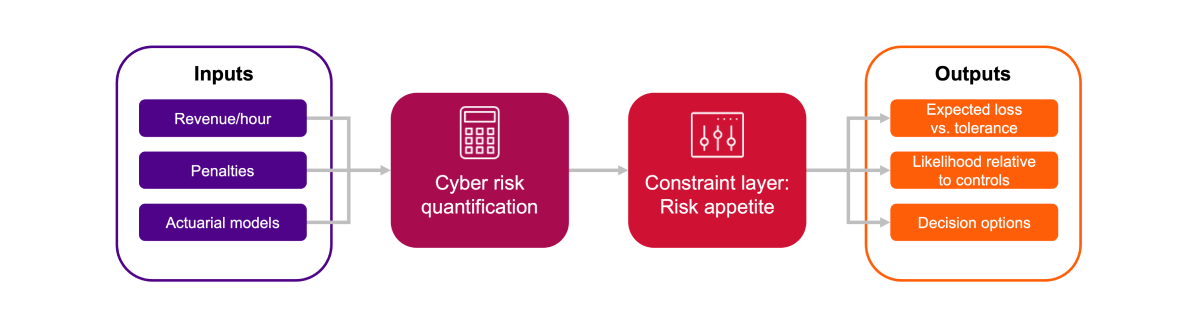
CRQ reframes risk through three primary business impact categories. Each category has its own drivers and timeline, and ignoring those distinctions leads to flawed prioritization.
- Business interruption: When systems fail, the cost clock starts running as production outages, penalties and lost revenues accumulate by the hour.
- Data breach: Where damage unfolds in waves and cleanup, fines, legal action and the erosion of customer trust linger for years.
- Financial theft and fraud: Compromised accounts, tampered transfers or false payment orders that inflict immediate losses.
CRQ also reverses the usual IT tunnel vision. Rather than starting with vulnerabilities, it begins at the business-model level. It asks: what would this cost us and which processes would cause the greatest financial impact if they failed?
The analysis uses company-specific data, such as hourly production revenue and contract penalties, cross-referenced with Munich Re’s actuarial models. The result: credible, actionable numbers. Executives can compare cyber investments to any other capital decision. Instead of "patch all vulnerabilities," the question becomes: which action reduces the most financial risk per dollar spent?
That shift marks the moment cybersecurity joins the CFO’s balance sheet. And, when CISOs talk in dollars instead of acronyms, cybersecurity becomes a language of enterprise value rather than fear management.
Risk appetite: Setting the boundary of ambition
Quantification alone is instrumentation — not leadership. Leadership requires defining how much risk your organization is willing to accept in pursuit of its goals. That definition (i.e., your organization’s risk appetite) is the hinge between measurement and management.
Every company balances ambition against exposure. A high-growth startup accepts volatility for potential upside while a regulated utility prizes stability over experimentation. Risk appetite transforms those instincts into policy, linking goals to thresholds, such as maximum loss, acceptable downtime and tolerance for reputational impact.
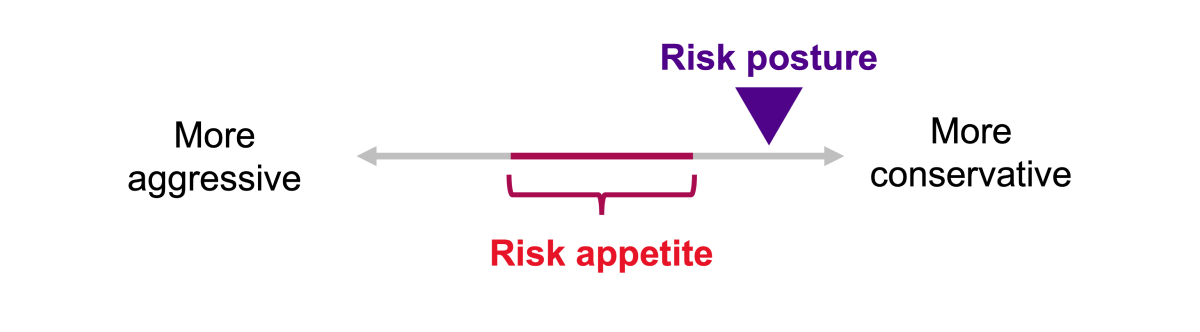
Defining risk appetite is both a quantitative and moral exercise. It signals not only how much loss a company is willing to bear but what kind of company it intends to be. Metrics like maximum loss and ROI coexist with softer judgments about values, reputation and ethics.
When a risk appetite statement (RAS) codifies those boundaries (distinguishing between risk capacity, tolerance and hard limits), leaders gain a common language for decision-making. For example, many organizations distinguish high appetite for innovation, moderate appetite for operations, minimal for security and low for compliance. Each organization must make these tradeoffs explicit.
A clear RAS ensures alignment. Without it, departments drift; marketing pushes for speed while legal demands caution. Well-defined risk appetite balances that friction. It also supports trust — investors and regulators can see that risk governance is intentional, transparent and measurable. Key risk indicators then track performance against these thresholds, providing early warning before conditions deteriorate.
Exposure management: Where visibility meets control
Until it meets daily operations, risk appetite is theoretical. Exposure management operationalizes that boundary by unifying three disciplines: attack surface management (ASM), risk-based vulnerability management (RBVM) and validation and remediation. This aligns with Gartner’s Continuous Threat Exposure Management (CTEM) model of scope, discover, prioritize, validate and mobilize.
- Attack surface management (ASM): Provides visibility into every asset that could be attacked, including shadow IT.
- Risk-based vulnerability management (RBVM): Contextualizes vulnerabilities by exploitability and business impact.
- Validation and remediation: Confirms which threats are truly exploitable and whether fixes are effective.
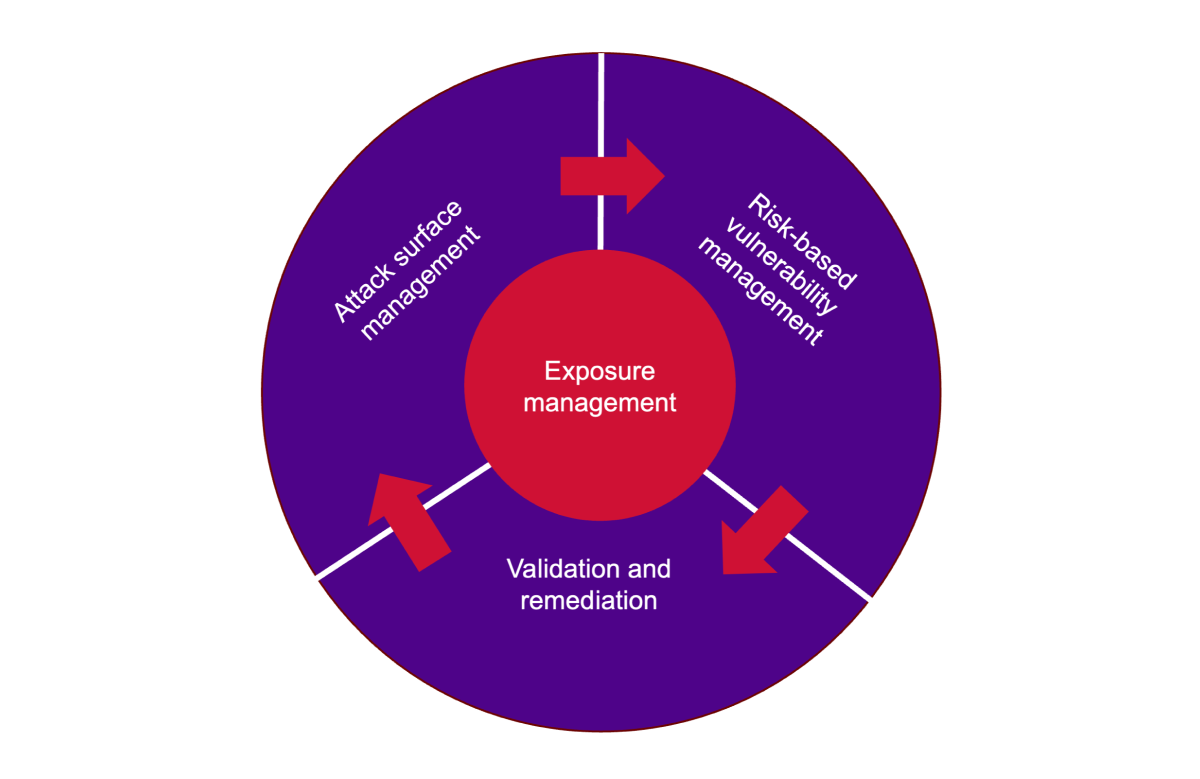
In practice, exposure management is a living feedback loop between visibility and governance. Data aggregation breaks down silos by correlating vulnerabilities with asset value, while validation ensures theoretical models match reality. Remediation closes the loop automatically (through integrated ITSM workflows).
An online retailer, for example, may choose to tolerate higher risk on Black Friday to maximize revenue, but does so with heightened visibility and rapid mitigation. Security thus becomes dynamic equilibrium rather than reactive crisis management.
Where traditional vulnerability management is reactive and incomplete, modern exposure management spans assets, endpoints, applications and clouds, adapting continuously to the organization’s defined risk appetite. Automation, escalation and real-time reporting ensure that leadership always knows where your organization stands, what an outage would cost and which actions deliver the greatest reduction in financial exposure.
The closed loop: Turning cyber risk into a controllable system
When cyber risk quantification, risk appetite and exposure management operate together, risk becomes a controllable variable — a closed economic and operational feedback loop.
CRQ shows how much financial damage a vulnerability could cause. Risk appetite defines how much of that risk the organization is willing to accept. Exposure management ensures that the company’s attack surface aligns precisely with this threshold. Together, these three form a system of measurement, direction and control.
- Without CRQ, the foundation is missing.
- Without risk appetite, there is no strategy.
- Without exposure management, there is no enforcement.
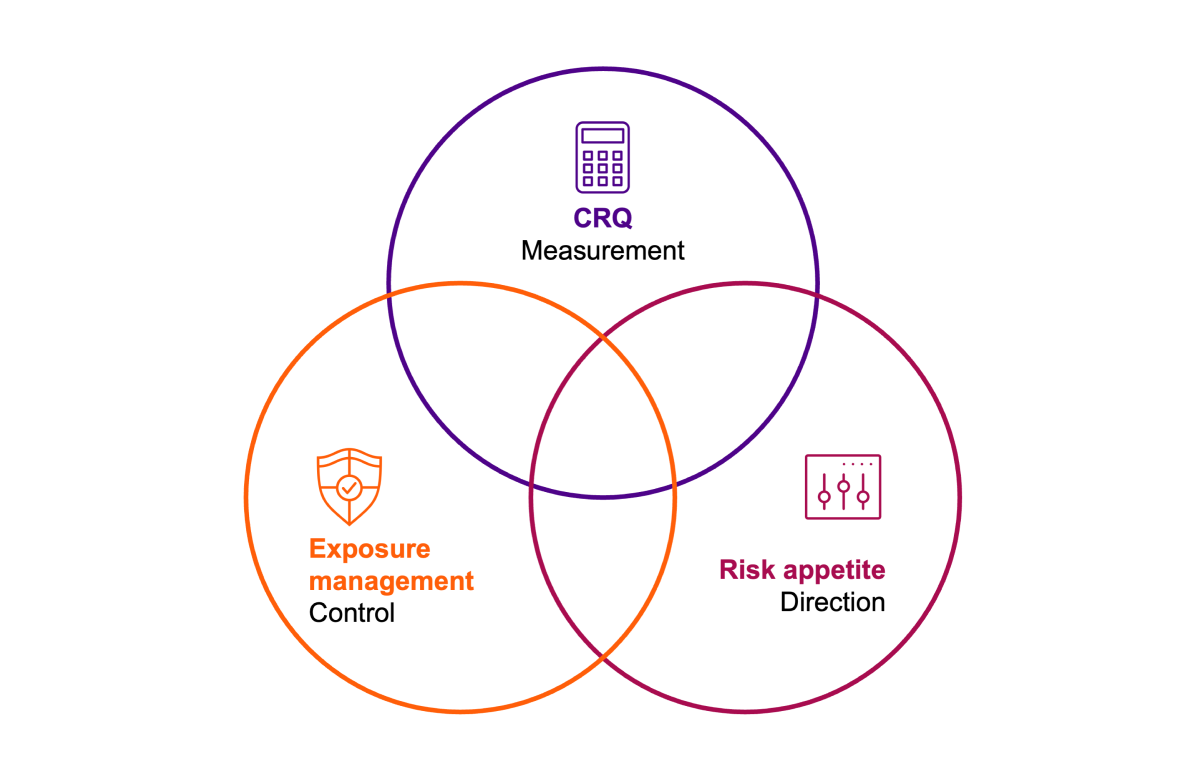
This closed loop converts cybersecurity from a compliance obligation into a performance discipline. It gives executives the same levers they use everywhere else (metrics, thresholds and continuous feedback). Imagine board meetings where risk variance is discussed with the same fluency as margin variance, where resilience becomes a competitive KPI.
For years, cybersecurity was the department of “no,” blocking ideas to prevent incidents. Quantification and exposure management transform it into the department of “how.” Leadership can now take calculated risks, prove the ROI of resilience and communicate in a language investors and regulators share: impact, probability and value at risk.
Measured risk becomes managed value — and leadership finally regains forward momentum. Cybersecurity, once a brake on innovation, becomes the steering system for strategic confidence — the new language of foresight. Anything less is gambling and, in the end, only the attacker wins.
FAQs
What is cyber risk quantification (CRQ) and why does it matter?
CRQ translates cybersecurity risk into financial terms, showing potential loss, probability and ROI for mitigation. This lets executives compare cyber investments to other capital decisions, prioritize effectively and communicate risk in business language rather than technical jargon.
How does a risk appetite statement improve cybersecurity strategy?
A risk appetite statement defines how much risk an organization is willing to accept to achieve its goals. It sets clear thresholds for loss, downtime and reputational impact, aligning all departments under a common framework.
What is exposure management and how is it different from vulnerability management?
Exposure management goes beyond patching vulnerabilities. It combines attack surface management, risk-based vulnerability management and validation to continuously align your security posture with your defined risk appetite. Unlike traditional vulnerability management, it prioritizes based on business impact and exploitability.
How do CRQ, risk appetite and exposure management work together?
Together, these three form a closed loop: CRQ measures financial risk, risk appetite sets acceptable limits and exposure management enforces those limits operationally.

