How do you compare?
Bridging the Divide
2026 State of Cybersecurity Report
The “preparedness gap” between threats and defenses is widening. What does the research say about how to reverse the trend?
2026 State of Cybersecurity Report
The “preparedness gap” between threats and defenses is widening. What does the research say about how to reverse the trend?
Share article
Cyberattacks are accelerating in number and sophistication. Organizational defenses are struggling to keep pace.
In short, companies are falling further behind in terms of how well prepared they are to defend against increasingly sophisticated threats.
This “preparedness gap” — which represents the shortfall in organizational readiness to defend against a broad spectrum of cyberthreats — widened by an average of 10 points compared to 12 months ago. Across the industry, security professionals identified ransomware and phishing as the top perceived threats, with 63% and 60% respectively rating these attack types as “high” or “critical” risks.
What's more, despite guidance from organizations like the FBI to not pay if an organization is hit by ransomware, 54% of all organizations surveyed said they believed their company would or probably would pay if hit by a ransomware attack today.
For example, the perceived risk of ransomware is up 8 points in one year, while compromised credential attacks have risen by 7 points.
These findings align with broader industry research, which shows cyberattacks are on the rise. A study from the World Economic Forum found that nearly three in four organizations reported a rise in cybersecurity risks in 2025 compared to 12 months prior. That report shows that critical infrastructure and social services (e.g., water, energy, healthcare, biosecurity) are increasingly targeted. The World Economic Forum research also found that supply chains are a critical area of vulnerability: 54% of large organizations identified supply chain complexity and third-party risk as the greatest barriers to resilience.
Each year, Ivanti calculates the preparedness gap by comparing industry-wide threat levels for various attack types with the readiness of organizations to defend against those threats. The preparedness gap research highlights where threat levels outpace existing security measures.
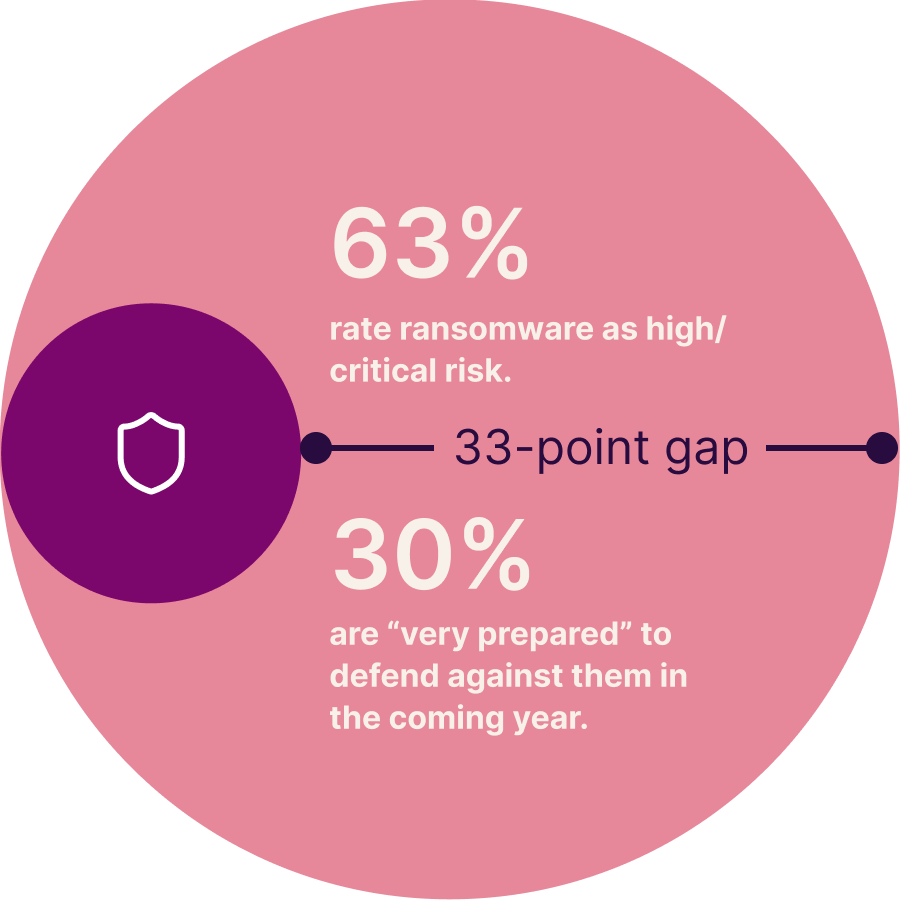
For example, 63% say ransomware attacks will be a high or critical threat in 2026, while just 30% are “very prepared” to defend against them in the coming year — a 33-point preparedness gap. Last year, the ransomware gap was 29 points. This widening divide between threat level and preparedness is true for each of the 10 threats we track, with most year-over-year changes in the double-digits.
In other words, cyberthreats are evolving and intensifying faster than organizations can adapt their defenses.
Click column headers to sort. The gap represents the difference between threat level and preparedness.

High/Critical Threat
Very Prepared
2026 Gap
Year-Over-Year

High/Critical Threat
Very Prepared
2026 Gap
Year-Over-Year

High/Critical Threat
Very Prepared
2026 Gap
Year-Over-Year

High/Critical Threat
Very Prepared
2026 Gap
Year-Over-Year

High/Critical Threat
Very Prepared
2026 Gap
Year-Over-Year

High/Critical Threat
Very Prepared
2026 Gap
Year-Over-Year

High/Critical Threat
Very Prepared
2026 Gap
Year-Over-Year

High/Critical Threat
Very Prepared
2026 Gap
Year-Over-Year

High/Critical Threatpoints
Very Prepared

2026 Gap
Year-Over-Year
Attackers are integrating AI into the entire attack lifecycle, making attacks faster, more scalable and more evasive. For example, AI tools enable adversaries to automate phishing campaigns, generate convincing deepfake video and audio content and exploit vulnerabilities with unprecedented speed.
Mike Riemer, SVP of Network Security Group and Field CISO at Ivanti, highlighted the seriousness of the issue to VentureBeat: “Threat actors are reverse engineering patches, and the speed at which they're doing it has been enhanced greatly by AI. They're able to reverse engineer a patch within 72 hours. So if I release a patch and a customer doesn't patch within 72 hours of that release, they're open to exploit."
How do you compare?
Great! Only 30% of security professionals say their CEOs could “definitely” spot a deepfake if targeted.
Most common response: 49% of security professionals say their CEOs could “probably” spot a deepfake if targeted.
18% of security professionals say their CEOs could “probably not” spot a deepfake if targeted.
3% of security professionals say their CEOs could “definitely not” spot a deepfake if targeted.
Reset
30% of security professionals say their CEOs could “definitely” spot a deepfake if targeted.
Additionally, in recent years, cyberattacks by nation-state actors have become more common and sophisticated due to AI’s amplifying effect. A recent study found 80% of cybersecurity leaders fear they could be a target of a nation-state cyberattack within the next 12 months.
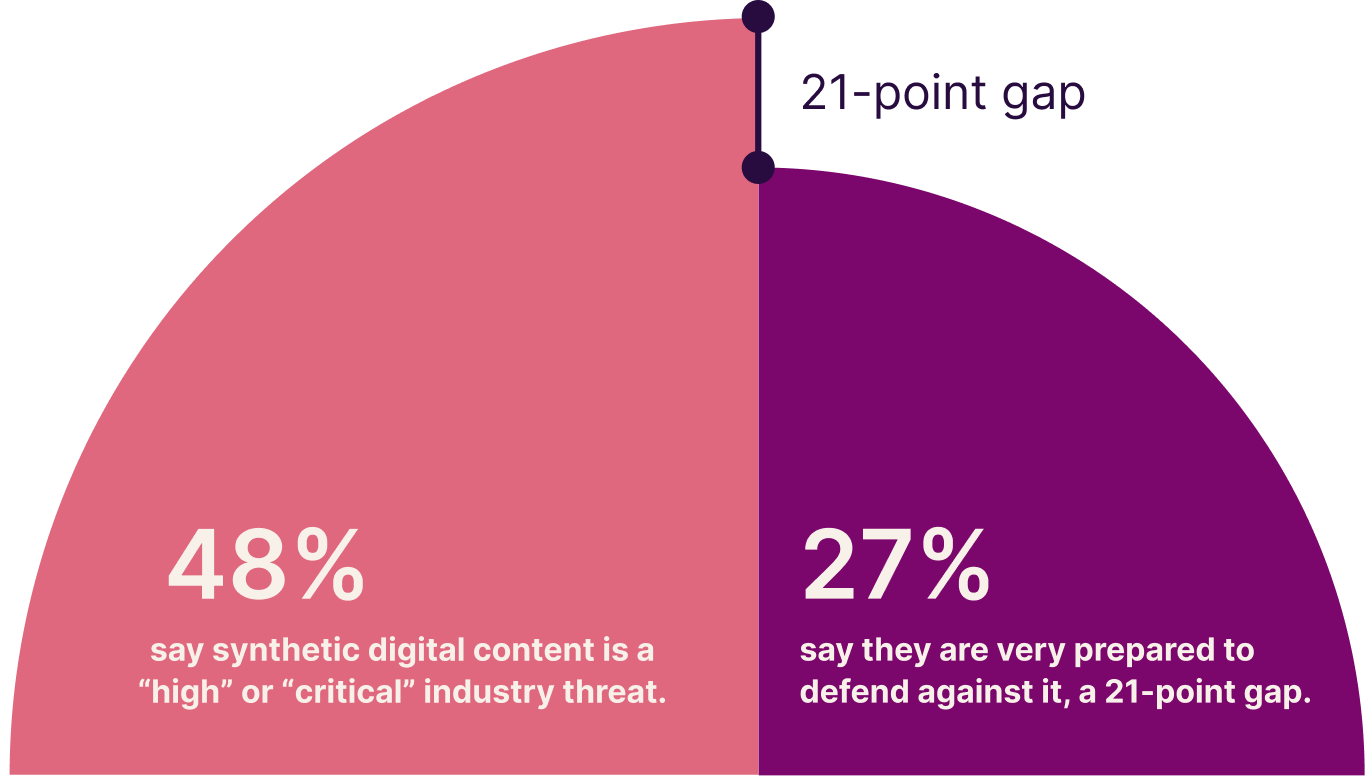
For AI-driven attack types like malicious synthetic digital content and data tampering, our research shows a sizable gap between industry threat level and organizational preparedness. For example, 48% say synthetic digital content is a “high” or “critical” industry threat, but just 27% say they are very prepared to defend against it, a 21-point gap.
Ivanti’s research also points to a serious risk from deepfake attacks: 77% of organizations have encountered these types of attacks — most often as personalized phishing emails enhanced with deepfake content (51% have experienced AI-fueled deepfake phishing). Phishing attacks aimed at executives are especially dangerous, and just 30% of security professionals say their CEOs could “definitely” spot a deepfake if targeted. Research from Deloitte shows deepfake attacks will cost US financial services companies $40 billion by 2027, a staggering number for a single industry.
$40 billion
Deepfake attacks will cost US financial services companies $40 billion by 2027, a staggering number for a single industry.
— as well as a high level of buy-in for the cybersecurity mandate among organizational leaders.
For example:
Security pros say their companies are increasing investments across a wide range of tactics and use cases. The most common areas of increasing investment are cloud security (68%) and data security (67%). And a significant number of companies (60%) are investing in gen AI for security use cases — though the figure is lower than we would expect given the amount of press it’s received.
As the AI arms race intensifies, a key question remains:
AI is empowering defenders to adapt rapidly and outpace threats, driving new levels of resilience and confidence in cybersecurity teams.
Despite evidence of heightened threats from bad actors using AI, security professionals report relatively high levels of optimism about using AI to protect their organizations.
Security pros are 2.4x more likely to believe defenders use AI just as effectively or more effectively than threat actors (versus believing that threat actors use AI more effectively). And they largely believe this trend will continue. Additionally, the vast majority of security professionals (92%) say automation is effective at reducing their team’s mean time to respond.
Though security pros remain confident, it’s clear that adversaries, armed with AI, are accelerating their operations, making them faster, more adaptive and more difficult to defend against. And with purpose-built generative AI, attackers can orchestrate vishing (i.e., voice phishing) and identity-based intrusions at unprecedented volume and precision. A study by the Harvard Kennedy School found that phishing emails generated by large language models had a click-through rate of 54% — far higher than the 12% observed for likely human-written messages.
Security teams need to speed up their adoption of AI tools and techniques to help them keep up with threats that are getting smarter and harder to stop.
Current uptake rates of AI/automation for cybersecurity applications remain modest. More than half (53%) of security teams use it for cloud security policy enforcement, but other important functions are used less often. Fewer than half use it for incident response workflows (44%), threat intelligence correlation (43%) and vulnerability response and remediation (42%).
Yet significant barriers to deploying AI effectively remain, including cost and regulatory challenges. But data quality issues rank among organizations’ biggest challenges, and our research shows these problems are only getting worse. Currently, 46% of organizations identify poor data quality as a barrier — up 9 points from last year.
While many organizations focus on deploying AI within security operations, they also face a broader challenge: how to harness AI safely and effectively at scale across the enterprise. As AI becomes embedded across business processes — from IT to finance to supply chain — companies need a cohesive strategy that moves from defense to governance, accountability and trust. A cohesive strategy begins with having a documented strategy for addressing AI vulnerabilities and risks, a practice that 78% of organizations now follow. Using comprehensive guardrails to guide the deployment and operation of AI systems and agents is also important, and just 55% do this today.
Raising the bar for AI literacy throughout the workforce, ensuring that every employee is equipped to understand and uphold responsible AI practices, is equally critical. When asked to give employees at their companies a grade for AI literacy, security professionals rated them a B (84% grade). But differences by industry are stark: Only the tech industry scored above 85%, while healthcare — a highly targeted industry for ransomware — scored a C+ (79%) for AI literacy.
Technology
B
85.6% grade
Healthcare
C+
79.4% grade
Manufacturing
B
84.8% grade
Retail
B
84.8% grade
Telecom
B-
83.1% grade
Financial Services
B-
82.8% grade

Agentic AIs are autonomous AI systems capable of making real-time decisions and taking action independently. They can detect, investigate and respond to threats without the need for constant human oversight. Eighty percent of security pros say they understand the term, and 87% say adopting agentic AI is a priority for their security teams.
Though companies are committed to figuring out how to use it, not all trust agentic AI to make decisions without some degree of human oversight. Most (77%) express some level of comfort with deploying agentic systems and allowing them to take actions without human review.
77% of cybersecurity professionals express some level of comfort with deploying agentic systems and allowing them to take actions without human review.
Organizations have more risk data at their fingertips than ever before. Now they must transform that information into real-time, high-stakes decisions that reduce exposure and strengthen resilience.
Organizations face a constant flood of cybersecurity risks, making it difficult to know where to focus resources and how to prioritize response efforts. Exposure management brings clarity to complex decisions, offering a nuanced approach for weighing operational priorities, resource allocation and cybersecurity risk reduction. Instead of treating all vulnerabilities as equal threats, organizations use an exposure-management methodology to understand which exposures truly matter to their business — and which actions will most effectively strengthen their risk posture in line with the organization’s risk appetite.
More than half (57%) of security pros say their leaders understand exposure management.
↑ 8 points in 1 year
At this time, 64% of organizations invest in exposure management.
+29% plan to do so in the next 12 months.
Test your knowledge
Correct! Only 27% rate their risk exposure assessment as “excellent,” despite 64% saying they are investing in exposure management. This gap reveals the challenge of turning investment into effective capability.
Incorrect! Actually, 27% rate their risk exposure assessment as “excellent,” despite 64% saying they are investing in exposure management. This gap reveals the challenge of turning investment into effective capability.
Reset
Yet the data shows there’s still plenty of room for growth and improvement. Just 27% say their ability to assess risk exposure is “excellent.” And security pros struggle with a lack of available data (47%) and a lack of time (46%) when trying to correctly assess risk.
Adding to the challenge, many security pros feel security leaders don't effectively communicate risk exposure to their company’s broader leadership; 59% say they are only moderately effective at best. The problem may in part be explained by the "curse of knowledge."
The research also highlights an ongoing divide between IT and security teams:
This divide is especially consequential for exposure management, which requires a close partnership between security and IT professionals. Security teams identify risks and design mitigation plans, but IT is responsible for implementing those changes. Effective exposure management demands balancing security needs with potential operational disruptions, underscoring the need for strong collaboration between security and IT leadership.
1 in 3
organizations struggle to prioritize risk remediation in key areas like patch management, a critical exposure-management practice.
Effective exposure management relies on strong frameworks, which clarify risk appetite and guide consistent action across teams.
 The Good News
The Good NewsEncouragingly, 81% of organizations report having an existing, documented framework for defining risk appetite, and 79% say they quantify cybersecurity risk to support enterprise decision-making — both positive steps.
 The Execution Gap
The Execution GapYet these good practices often face execution gaps: Fewer than half (45%) say their framework is closely followed in day-to-day operations, and one in three struggles to prioritize risk remediation in key areas like patch management, a critical exposure-management practice.
Measurement discipline is essential for operationalizing exposure management, but most organizations still lack a unified approach to tracking the metrics that matter most.
While KPIs are intended to connect vulnerability management efforts to business risk, our research shows that the landscape remains fragmented — and most commonly used measures fail to reflect risk context. Only half of companies (51%) use a cybersecurity exposure score or other risk-based index, while many still rely on process metrics such as mean time to remediate (47%) or percentage of exposures remediated (41%). These latter metrics — focused on speed and coverage — can look positive in isolation but reveal little about whether remediation efforts actually improve risk posture.
Whether or not a true cybersecurity talent gap exists may be debated, but there’s no disputing the growing strain on workforce well-being.
Recent studies seem to contradict one another on this point. The ISC2 2024 Cybersecurity Workforce Study estimates a global shortage of about 4.8 million cybersecurity professionals, yet many out-of-work professionals have pushed back on figures like these, saying the talent gap is overstated, or at least oversimplified. (ISC2 also explains that its “workforce gap” figure does not represent job openings. Instead, it reflects the difference between how many professional organizations say they need to manage cybersecurity risk effectively and how many cybersecurity professionals they currently employ, which is more like a staffing gap.)
Whether a skills gap or staffing gap, how is the number so large while many security professionals remain out of work? Part of the answer lies in constrained budgets:
Another explanation is a growing skills mismatch — with employers struggling to find candidates whose expertise aligns with the fast-changing requirements of cloud, automation and AI‑driven security operations.
43%
Among security pros Ivanti surveyed, 43% report high levels of stress due to their jobs
Ivanti's research uncovered similar nuances in the job market. It shows that just one in four organizations say they are currently experiencing a critical shortage of necessary IT talent and skills; the largest share (58%) instead claims the shortage is “moderate but manageable.”

The effect of this professional stress takes a real, personal toll on the lives of those working in security roles. Among security pros Ivanti surveyed, 43% report high levels of stress due to their jobs, and 79% say stress takes a toll on their physical and mental health.
More specifically:
Despite the hardships, most (61%) would not consider changing their career paths due to stress/burnout. This could be due to job hugging, a phenomenon noted in IT Brew where people cling to their current role even if they aren’t fully happy in that position.
See how you compare : Drag and drop to rank the barriers in order of importance. Put the biggest barrier at #1.
42% of security teams ranked "Lack of skilled talent" as the #1 barrier to cybersecurity excellence. The promise of AI in cybersecurity is to help, but here again, skills and talent shortfalls make adoption extremely difficult.
Lack of skilled talent is the number one barrier to cybersecurity excellence, according to survey respondents.
The use of AI in cybersecurity promises to help, but here again, skills and talent shortfalls make adoption extremely difficult. A study by TechTarget found that within the cybersecurity talent pool, skills related to “emerging technologies” represent the biggest, most pressing shortfall. Meaning: Even for those organizations that want to adopt AI to help ease a talent gap, their existing talent gap prevents them (or slows them) from doing so — a self-reinforcing problem.
A 2025 World Economic Forum study found that only 14% of organizations have the skilled talent needed to meet their cybersecurity objectives, highlighting just how urgent the upskilling and hybrid-skills gap has become as AI adoption accelerates.
Ivanti’s research and third-party studies indicate demand is surging for “hybrid skills” and roles. This includes, for example, AI security analysts, machine learning engineers with a security focus and AI governance professionals. Fifty-nine percent of security pros surveyed say there will be an increasing demand for hybrid skills over the next 3-5 years due to impacts from AI adoption/use.
Specialists who understand both AI systems and security implications
Engineers who can build and secure machine learning pipelines
Experts in AI policy, compliance and risk management
Find out how organizations with advanced cybersecurity maturity leverage AI, invest in exposure management and earn leadership support.
We asked companies to rate their overall cybersecurity maturity levels (see explanation below), and we then used those ratings to understand what more mature organizations do differently. Security pros were able to rate their organization’s security maturity from basic (Level 1) to best-in-class (Level 4).
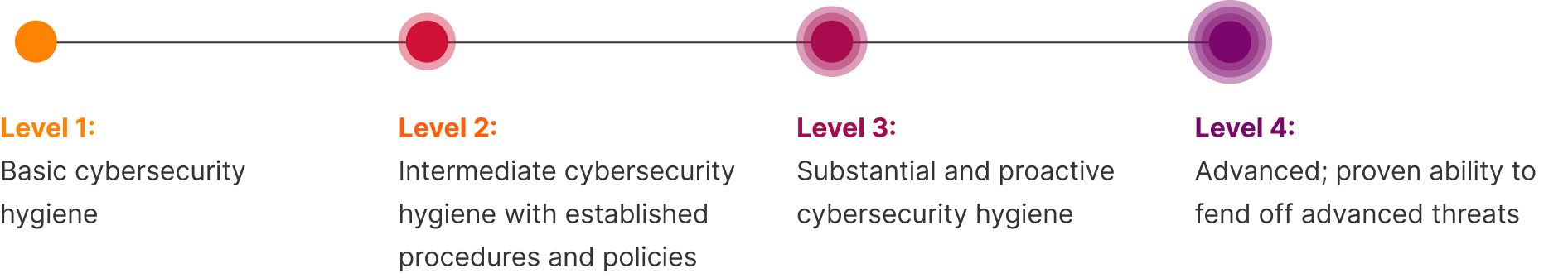
Using this model, we can understand what the most advanced organizations do differently to secure their organizations compared to less mature organizations.
(Note that the following section does not discuss Level 1 organizations because few survey respondents rated their organizations within that category.)
The sum of all these best practices: Advanced organizations are simply more confident about their security preparedness and more resilient in the face of adversity. Sixty-nine percent of Level 4 organizations say their incident response plans would definitely work as intended in the face of a breach, and 77% say they’re very confident their team could prevent or stop a damaging security incident.
Ivanti surveyed 1,215 cybersecurity professionals in July and August 2025. Our goal: to understand today’s most pressing cybersecurity threats as well as emerging trends, opportunities and business strategies.
As part of the study, we developed a cybersecurity maturity model. (See more details in section five.) Collecting information through self-reporting has limitations, as people may be biased when evaluating their own efforts; however, we believe the findings based on this maturity model provide useful signals to the cybersecurity field. We ask that readers keep these limitations in mind.
This study was administered by Ravn Research, and panelists were recruited by MSI Advanced Customer Insights. Survey results are unweighted. Further details by country are available by request.
What's inside: - All charts and graphs - Editable slides with key takeaways
