Mobile device management vs Modern device management
The truth is, MDM and MDM are as close as twins. The meaning of the acronym has changed, and with good reason.
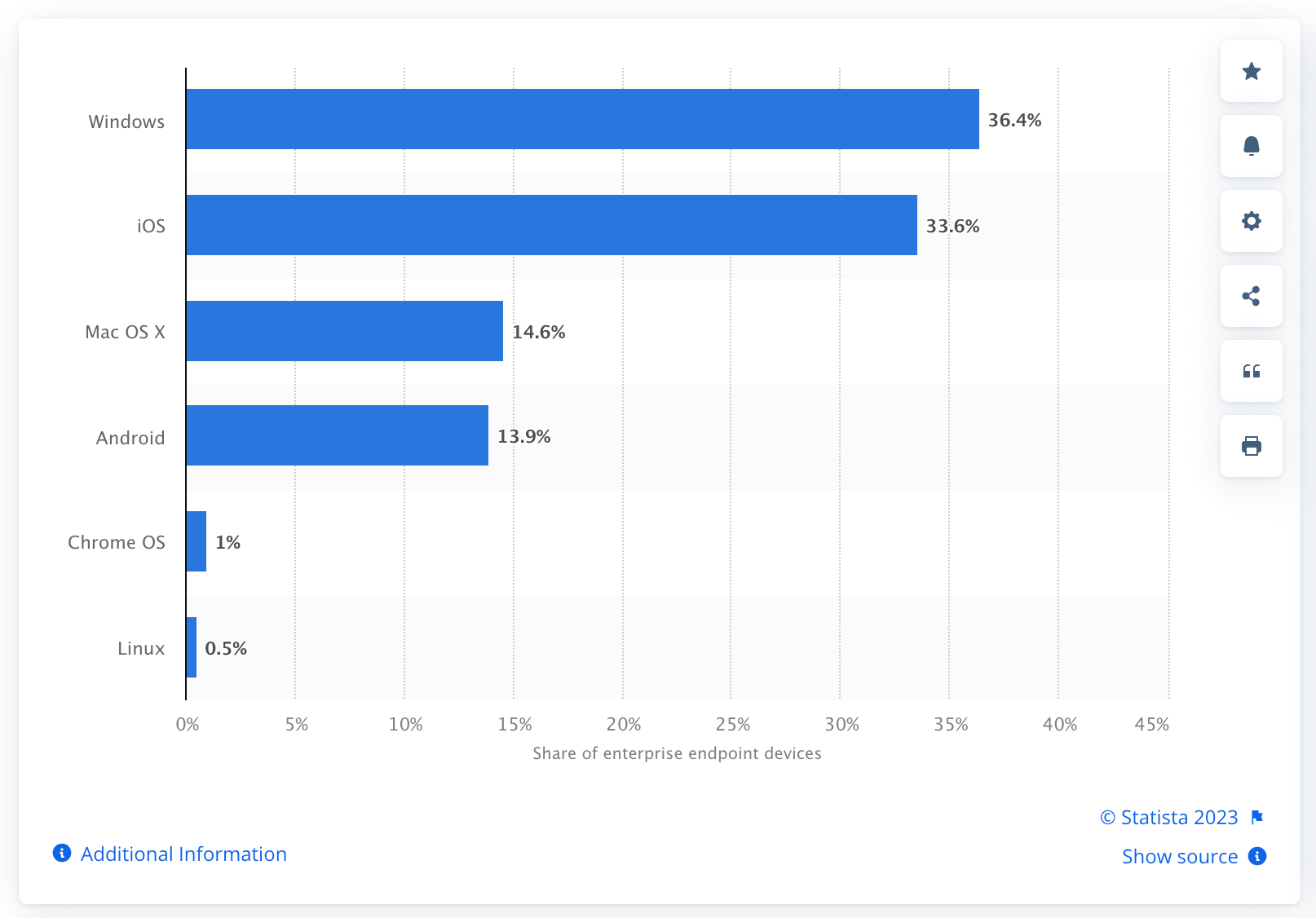
Remember the architecture Apple launched upon the IT world with the introduction of iOS? It was developed with education organizations in mind, but Apple plainly intended to jump into the enterprise market that had been ruled by historical players like Microsoft.
As part of this strategy, the iOS model has been gradually extended to macOS devices like desktops and laptops, and the device management API has been evolving on each version. Apple has increasingly moved macOS toward becoming a mobile-like managed OS with embedded security and managed native APIs.
The result of this (and similar moves by other providers, as we’ll see below) has been a nomenclature shift: what had been called “mobile device management” was now being applied within a network ecosystem where MDM tools were managing other (often remote) endpoints that weren’t mobile.
So today, devices like laptops and desktops — including those that are part of “bring your own device” (BYOD) scenarios — are enrolled in what we call “modern device management” systems that apply to all endpoints, not just mobile devices.