Patching within 14 days – Insight, Prioritization and Management
In recent months the number of phishing emails has increased by 30,000%. Most of the time, those phishing attacks make use of exploits within systems. Very often a patch is already available for these exploits. In an average of 22 days after a patch is released, cybercriminals create an exploit that takes advantage of the vulnerabilities that the patch solves. This means it is important to patch as soon as possible, preferably around 14 days after the release of a patch. That way you have a few days left in case you hit problems when deploying the patch. But how do you get insight of your patch status and SLA compliancy and perhaps more importantly, how do you make sure that your systems are actually patched within that timeframe??
SLA time-to-patch
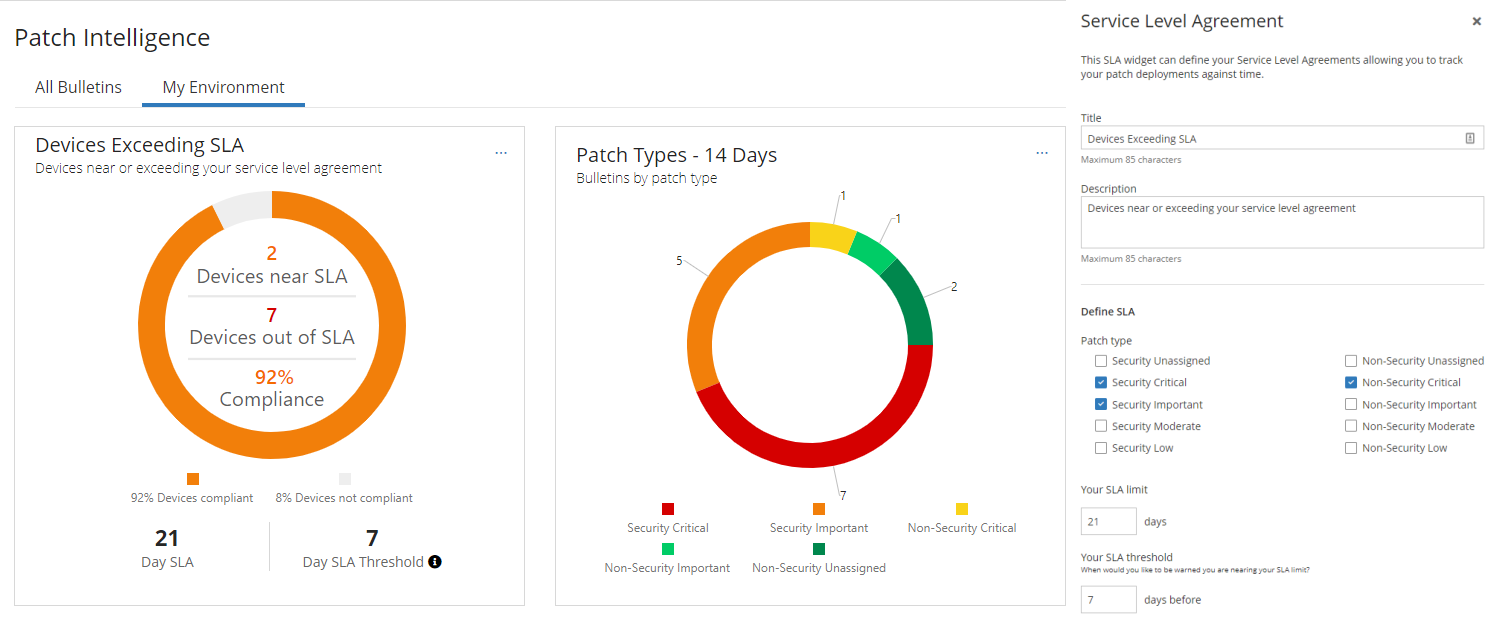
In June, the Cybersecurity Image Netherlands 2020 was released. It states that less than half of vulnerabilities are patched at companies within 90 days. This means that you as a company, are vulnerable to a problem for more than 2 months. A problem that could easily have been patched already. The first thing is to understand whether you get that 21-day SLA and which systems are in danger of falling outside this window. Ivanti Neurons for Patch Intelligence connects to Ivanti’s patch solutions to give you this insight. The first thing you see after going to Ivanti Neurons for Patch Intelligence is the status of your environment, how many machines are compliant and how many are on the edge to exceed the SLA. The SLA can be set to patch type, such as critical or important security patches or critical non-security patches. In the example below, the SLA is set to 21 days and warns when systems only have 7 days or less left. This way you get a warning 14 days after the release of a patch that you need to implement in your environment.
Patch Change Ticket priorization
There are a view stages within Continuous Vulnerability Management where Ivanti Patch Intelligence provides the necessary insights.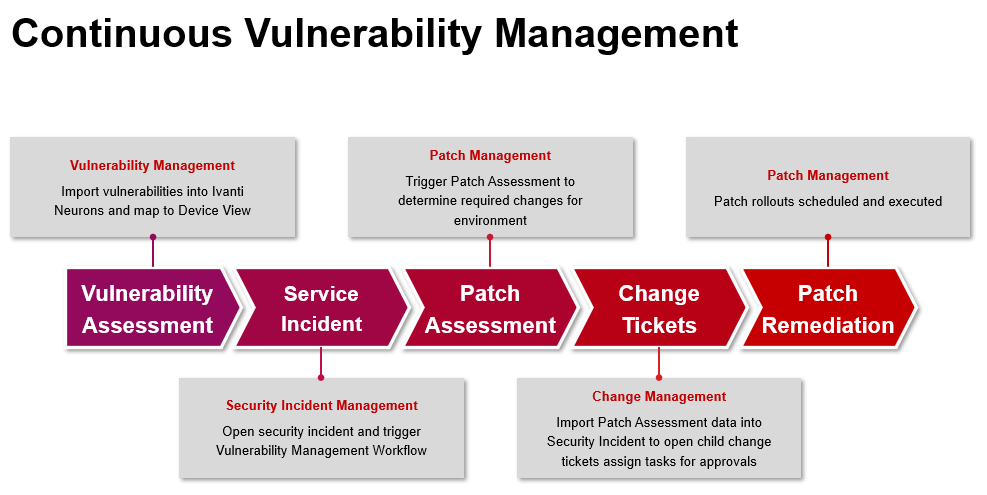
After the Patch Assessments by one of Ivanti’s patch solutions, the outcome is uploaded to Ivanti Neurons for Patch Intelligence, so you get an overview of all the patchesmissing in your environment. With this data, Change Requests can be made in your Service Management solution. When using Ivanti Security Controls and Ivanti Automation, it is possible to have Change Requests automatically created directly from the Patch Assessment step.
To assess Change Requests regarding patches, it is important that you and the CAB (Change Advisory Board) gain insight on how reliable a patch is – both in deployment and how they operate after installation. With that data you can select which patch process applies to the Change Request and whether a patch needs an additional test cycle or first needs to be rolled out to a pilot group. Ivanti Neurons receives anonymous information from Ivanti Neurons customers and other sources about how often a patch installation fails and whether a patch causes problems in the operation of applications. This data is used by Ivanti Neurons for Patch Intelligence to give insight in reliability of a patch and help you understand expected deployment issues. You will also receive tips on how to prevent or work around some issues. This information is collected through Ivanti customers, Microsoft and forums.
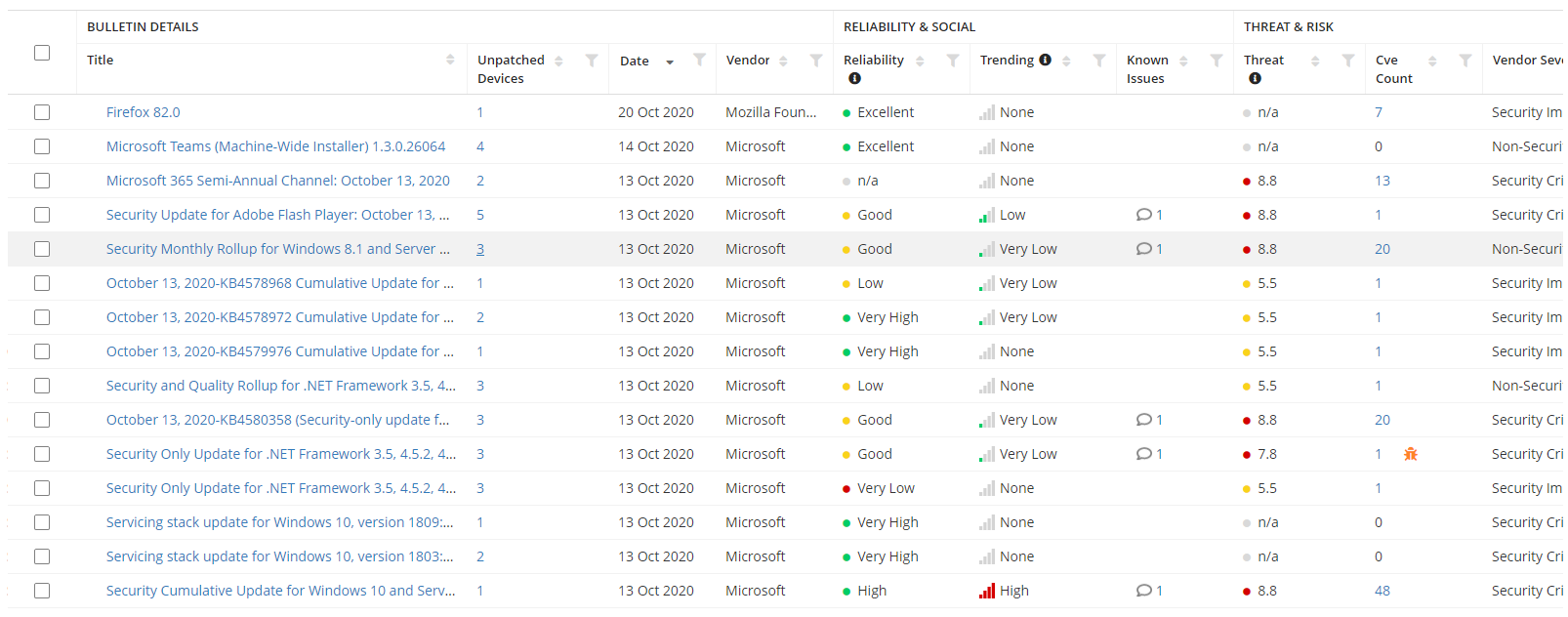
To determine the priority of a Patch Change Request, you need to understand the importance of the problem that the patch is solving. Ivanti Neuron's for Patch Intelligence indicates a threat score, the CVSS score, that runs from 0 to 10. The higher the number, the more important it becomes to install the patch as quickly as possible. In addition, Ivanti Neurons for Patch Intelligence indicates whether a problem solved by a patch, is already used in cyberattacks. Together with a trend analysis of social media, this data can be used to determine priority of patches and which systems need to be patched first. After all, a high threat score, the fact that a problem is already used in attacks and that it is widely discussed on social media, gives a huge chance that the exploit will also be used to attack your systems and the patch should be immediately rolled out over your environment.
More information can be found at Ivanti Neurons for Patch Intelligence | Ivanti or make an appointment for a demo through your account manager.
