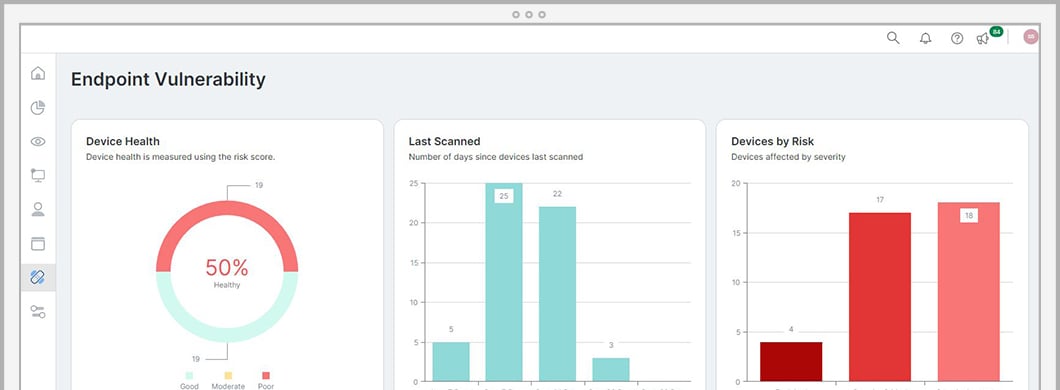
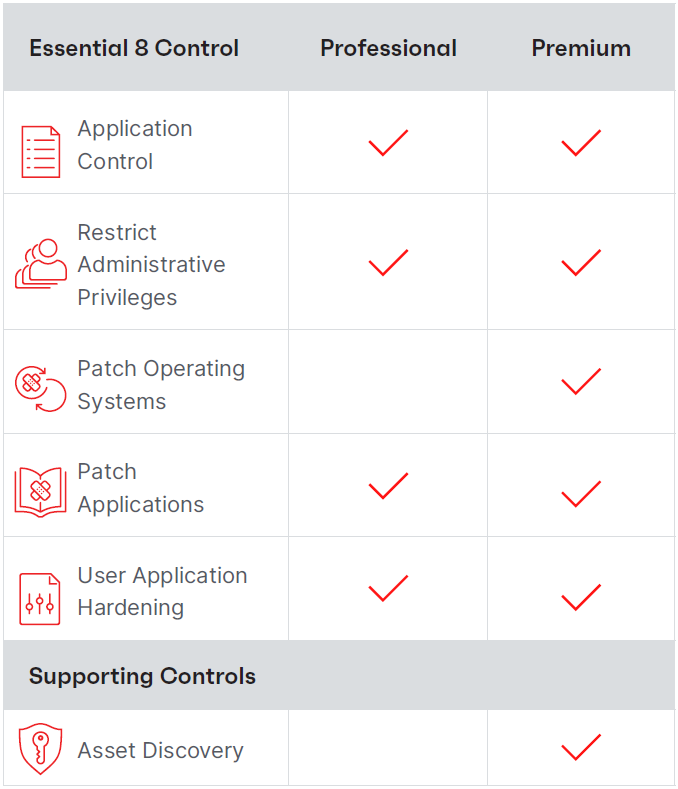
The ACSC Essential Eight is a list of eight essential mitigation strategies for businesses and organisations to protect themselves against cyber threats. The Australian Signals Directorate (ASD), in agreement with the Australian Cyber Security Centre (ACSC) developed the Essential 8 strategies to improve cyber resilience, protect systems and resources against compromise, and keep data secure.

Whitepaper
The ACSC Essential 8: What It Is, Why It Matters, How We Help