Understanding External Attack Surface Management: How It Works and Why It’s More Critical Than Ever
Key Takeaways
- External attack surface management (EASM) is a cybersecurity approach that focuses on identifying and managing external-facing assets to prevent breaches.
- If your organization isn’t managing its external attack surfaces, you could be vulnerable to attacks, reputational damage, financial losses, etc.
- EASM involves multiple key stages (discovery, assessment, prioritization, reporting and remediation) and falls under the wider practice of exposure management.
Attack surfaces can expand without your organization even realizing it. And, lacking visibility into your external-facing assets and the vulnerabilities they may contain can lead to significant security risks.
External attack surface management (EASM) is a cybersecurity approach designed to safeguard your external assets and strengthen your organization's overall security posture. It does this by providing full visibility into these assets (and associated vulnerabilities) that could be exploited by threat actors.
In this article, we’ll walk you through how EASM works, the risks involved with overlooking your external attack surfaces, the benefits as well as where EASM sits in the broader practice of exposure management.
How external attack surface management works
EASM is the practice of identifying and managing your external-facing assets (e.g., websites, APIs, etc.) to prevent security breaches. Additionally, the process includes identifying attack surface gaps that can expose your organization to cybersecurity risks.
EASM helps fight unwanted expansion of your attack surface through visibility, enabling your organization to stay up to date on your potential vulnerabilities. Leveraging EASM provides the following benefits:
- Additional source of discovery and asset visibility.
- Curbs cloud sprawl and shadow IT.
- Reduces AI-powered phishing tactics.
- Analyzes and prioritizes exposures.
- Detects data leakage.
- Reduces phishing and social engineering attacks.
- Adheres to regulatory compliance requirements.
- Extend your vendor risk management by providing external risk perspective of third-party vendors.
EASM involves multiple key stages, including Discovery, Assessment, Prioritization, Reporting and Remediation.
Discovery
As mentioned above, EASM involves monitoring your external attack surface to identify those assets to both catalog them and uncover vulnerabilities that could lead to a hacker infiltrating your organization.
It doesn’t involve an invasive scan. Rather, it involves a passive crawl of your external attack surface, and all you need is a URL to start the process. EASM solutions, for example, use public data in combination with security intelligence. The assets that make up your external attack surface include:
- Web servers.
- DNS servers.
- IoT devices.
- Network edge devices.
- Application servers.
- Certificates.
- Cloud-based tools.
- Shadow IT.
Learn more: How to Identify Your Organization’s Attack Surface
Assessment
Thorough and continuous assessment is essential to understand your organization's risk landscape and effectively prioritize remediation efforts. At this stage, your organization evaluates whether the assets identified during the discovery process are in use and if they are harboring vulnerabilities. EASM solutions do this by identifying publicly disclosed security weaknesses, outdated software versions and more.
By examining these assets for vulnerabilities and other potential security risks, you gain crucial insights into your security posture.
Prioritization
Once vulnerabilities are identified, the next step is to determine which ones to address first based on their risk to your organization. Since it’s often impractical to remediate every vulnerability, risk scoring methods help you assess the urgency and impact of each exposure. This allows your security teams to focus on the most critical issues, streamlining the remediation process and ensuring that resources are allocated effectively.
Reporting and remediation
The next stage in EASM is to report on these risks and begin remediation. EASM solutions enable you to generate comprehensive reports that offer an overview of your external attack surface, along with detailed breakdowns of critical vulnerabilities. These reports are invaluable for communicating the nature and urgency of potential threats, helping stakeholders understand the importance of prompt remediation and informing decisions.
The risks involved with not monitoring your external attack surface
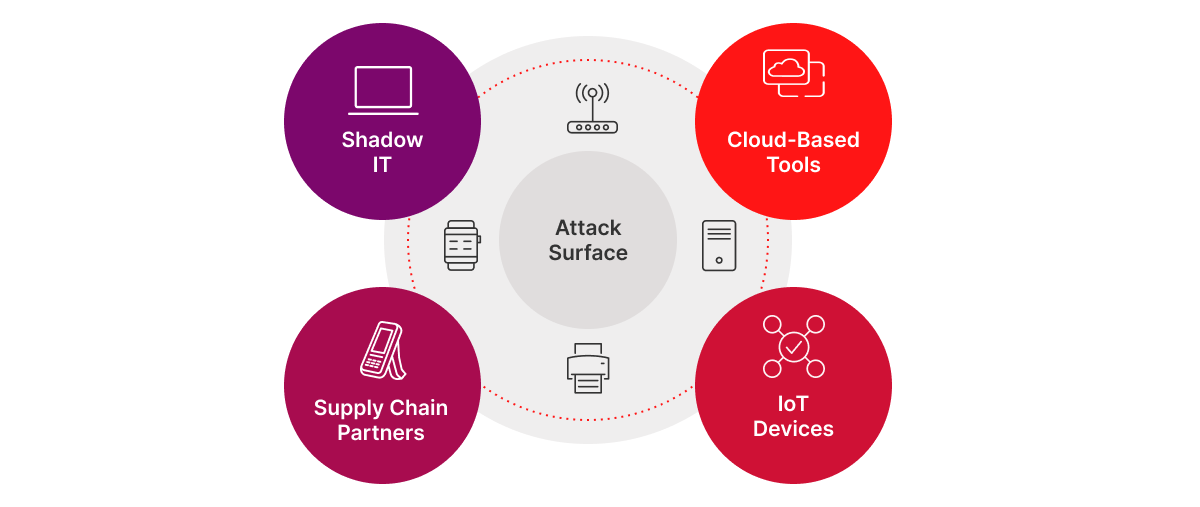
If your organization does not have full knowledge of the external attack surface, you risk having unknown or unmonitored assets or misconfigurations that open you up to attack, resulting in reputational damage, financial loses and more.
The lack of visibility into shadow IT, misconfigured or forgotten services allows for easy entry points for attackers. According to Computer Weekly, identity and access management company Okta was exposed to multiple security breaches due to shadow IT.
Furthermore, these assets are visible to anyone on the internet. It doesn’t require any special skills for someone to obtain this information about your external attack surface, meaning it is straightforward for a threat actor to gain access to your organization if you don’t enact proper measurements.
Now that you have an overview of external attack surface management, it’s important to understand that it’s just one part of your larger attack surface, which is where exposure management comes into play.
How EASM plays into exposure management
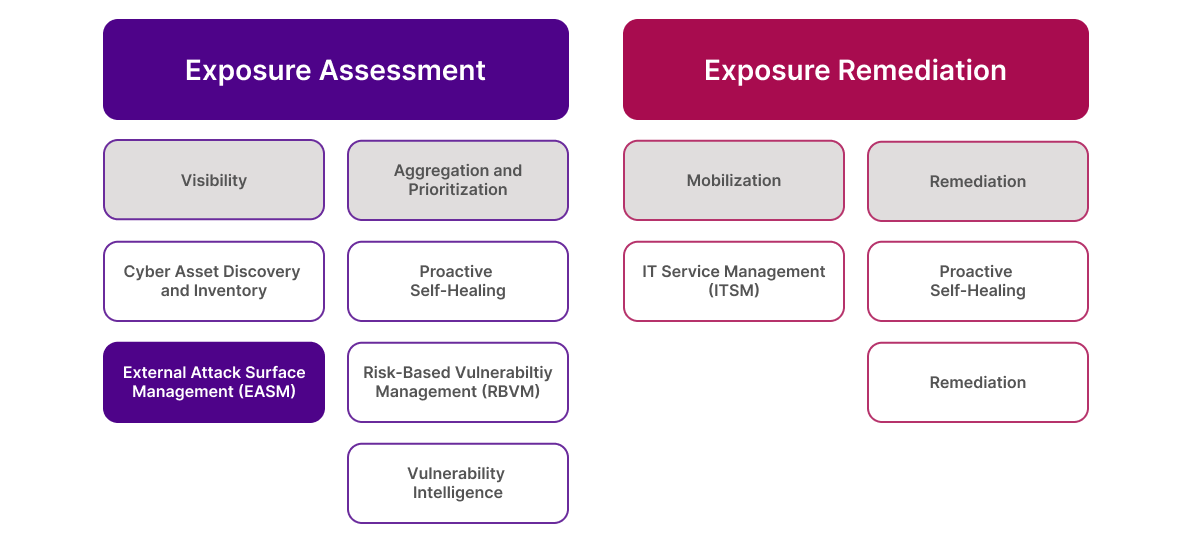
Exposure management focuses on asset visibility, exposure aggregation, risk-based prioritization and remediation of exposures. It’s a comprehensive cybersecurity practice that helps organizations define their risk appetite and keep levels within acceptable bounds.
EASM is just one part of exposure management (visibility, as shown in the graphic above). In cybersecurity, you can’t protect what you can’t see. So, let Ivanti help you get full visibility into your external attack surface with Ivanti Neurons for EASM.
FAQs
What is external attack surface management (EASM)?
EASM is a cybersecurity approach focused on identifying, assessing and protecting an organization’s external-facing assets to prevent security breaches. These assets may include websites, APIs, IoT devices, cloud tools and other internet-accessible resources.
What types of assets are included in the external attack surface?
Assets typically included in the external attack surface are web servers, DNS servers, IoT devices, mobile devices, network devices, application servers, cloud-based tools and shadow IT (unauthorized or unmanaged tech).
What is the relationship between EASM and exposure management?
EASM is a component of exposure management, which is a broader practice focused on proactively identifying, assessing, prioritizing and mitigating security exposures across an organization. Exposure management aims to keep cybersecurity risks within acceptable limits.
Does Ivanti sell EASM software?
Yes, Ivanti Neurons for EASM is a cloud-based solution that combats attack surface expansion with full visibility of external-facing assets and actionable intelligence on exposures.

