Vulnerability Prioritization: The Complete Guide
Key Takeaways
- Go beyond the CVSS. Combine CVSS with exploitability, asset value and threat intel to spot real risks.
- Visualize your priorities with a matrix. Use likelihood vs. impact to quickly prioritize what matters most.
- Prioritize together. Collaboration across teams and smart tools, like Ivanti RBVM, drive effective remediation.
With thousands of vulnerabilities discovered every year, not all pose the same risk. Some can cripple critical systems, while others have little real-world impact.
The key is knowing which threats to act on first. Vulnerability prioritization helps security teams cut through the noise, focus on what truly matters and build resilience against critical attacks.
What is vulnerability prioritization?
Vulnerability prioritization is the process of ranking vulnerabilities based on risk factors, such as exploitability, asset importance, threat intelligence and business impact.
Rather than reacting to every alert, proper prioritization allows organizations to focus on the vulnerabilities that pose the greatest danger to the business. Without prioritization, security teams risk wasting time patching low-risk flaws while missing critical exposures that attackers could exploit. If done well, prioritization enables smarter resource allocation, faster response to urgent threats and better alignment with compliance and business goals.
When talking about vulnerability management, it’s helpful to separate detection from prioritization: detection is the act of finding and listing vulnerabilities (often by using scanners or automated tools), while prioritization is the process of deciding which of those vulnerabilities to fix first, based on factors such as risk, likelihood of exploitations, business context and asset value.
In other words, detection is about making the list, and prioritization is about sorting through it by urgency and impact.
What is risk-based vulnerability prioritization?
Traditional methods of risk prioritization often rely solely on CVSS scores. While helpful, severity ratings alone ignore context, treating all environments with the same and overlooking business-critical risks.
Risk-based prioritization shifts the focus to what truly matters by incorporating:
- Asset criticality
- Type of exploit and active threats
- Business impact
- Threat intelligence
Combining these elements, risk-based prioritization ensures your security team focuses on vulnerabilities that are both exploit-ready and business-critical, instead of scattering efforts across every scan finding (many of which might be low-risk).
Without this approach, you risk patching low-impact test-server issues while overlooking high-impact, high-exploit vulnerabilities in your most critical assets. This method creates a triage process rooted in actual risk rather than just technical severity.
Advantages of risk-driven approaches
Adopting a risk-based approach shift the focus from only recognizing the severity of a vulnerability to addressing the factors the truly put your organization at risk. Here’s why that matters:
- Reduced noise — Eliminate alert fatigue by filtering out low-risk vulnerabilities that don’t require immediate action.
- Faster remediation of critical issues — Focus on your limited resources on the vulnerabilities most likely to be exploited.
- Better alignment with business goals — Prioritize what matters to your organization, not just what is perceived as urgent.
- Improved collaboration — Security, IT and DevOps teams can work from a shared understanding of what’s most important.
Risk-based vs. traditional prioritization models
Below is a quick reference table to help you understand how risk-based vulnerability prioritization contrasts with traditional approaches.
Traditional approach |
Risk-based approach |
|---|---|
| Based mostly on CVSS scores. | Incorporates exploitability, asset value and threats. |
| Treats all high CVSS scores equally. | Recognizes that not all "high" CVEs are high risk. |
| Generic, one-size-fits-all. | Tailored to your specific environment. |
| Often leads to patching low-impact vulnerabilities. | Focuses on what truly affects your business. |
How to prioritize vulnerabilities
Identifying vulnerabilities is only the beginning. With thousands of possible issues across networks and applications, knowing what to fix first is essential. Modern prioritization considers:
1. Asset criticality: Not all assets are equal. A flaw in a public-facing portal handling sensitive data is far riskier than one on a test server. Classifying assets by business value helps direct attention to where it counts.
2. Exploitability and threat intel: A vulnerability isn’t always a threat — unless attackers are actively exploiting it. Prioritize issues on the CISA KEV list, including ransomware kits, or with public exploits first.
3. Severity (CVSS): CVSS provides a baseline but should not be the only factor. High scores without exploitation may be less urgent, while medium scores with active threats may require faster action.
The Common Vulnerability Scoring System (CVSS) provides a standardized way to assess the severity of a vulnerability (typically on a scale of 0.0 to 10.0):
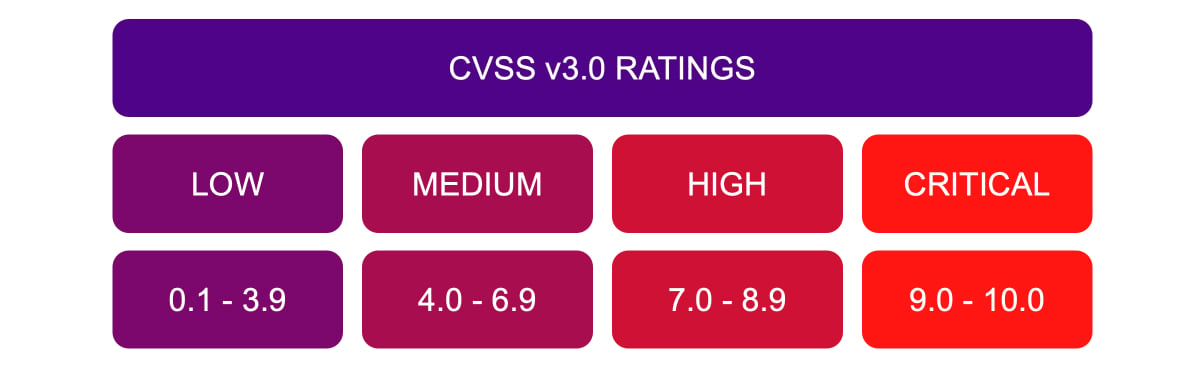 Why it matters:
Why it matters:
CVSS helps establish a baseline, especially in large-scale scanning. However, severity scores alone don’t take into account business or environmental context, so they shouldn’t be the only factor.
Best practices for effective vulnerability prioritization
Prioritization shouldn’t be an afterthought. You should build it into every stage of your vulnerability management process.
From the moment vulnerabilities are discovered, you should evaluate them based on the risk factors mentioned above to ensure remediation aligns with your organization’s threat landscape and operational priorities. Integrating prioritization early also helps reduce bottlenecks and streamline remediation workflows.
- Integrate into the VM lifecycle: Evaluate vulnerabilities by risk from the moment they’re discovered.
- Leverage automation: Tools like Ivanti Neurons for RBVM combine CVSS, threat intel and asset context to automatically assign risk scores.
- Continuously monitor: Threats evolve; a low-risk flaw today could become critical tomorrow. Regularly refresh threat feeds and reassess priorities.
- Foster collaboration: Security brings risk context; IT provides operational insight. Working together ensures prioritization is both effective and realistic.
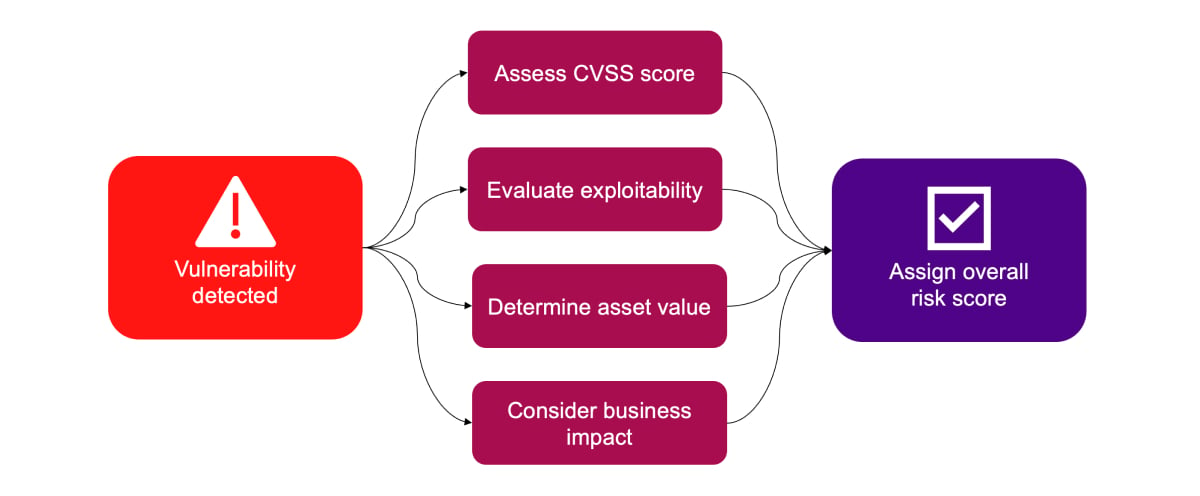
Manual prioritization is unsustainable at scale. To handle large volumes of vulnerabilities, organizations should leverage tools like Ivanti Neurons for RBVM and Ivanti’s Exposure Management solutions.
These platforms combine threat intelligence, CVSS scores, asset context, and business impact to automatically assign risk scores and suggest prioritization. Automation not only saves time but also improves accuracy and consistency, helping security teams respond to critical threats faster.
Vulnerability prioritization matrix: Make more strategic decisions
With security teams overwhelmed by thousands of vulnerabilities, effective prioritization isn't a luxury — it's a necessity. One of the most straightforward visual tools for helping teams decide what to fix first is the vulnerability prioritization matrix.
What is a vulnerability prioritization matrix?
A vulnerability prioritization matrix is a visual decision-making framework that helps security teams rank vulnerabilities based on multiple risk factors (typically likelihood and impact).
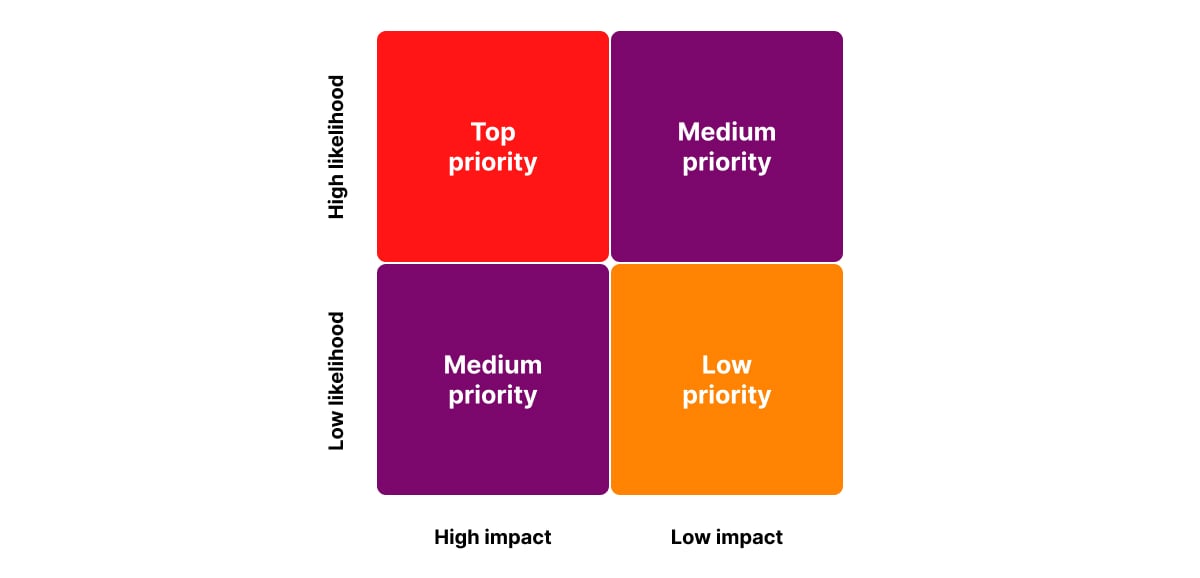 It plots vulnerabilities on a grid or heatmap, helping teams see at a glance:
It plots vulnerabilities on a grid or heatmap, helping teams see at a glance:
- Which vulnerabilities pose the highest risk.
- Which vulnerabilities can be deferred or monitored.
- How to allocate remediation resources.
Think of it as a risk lens that turns raw vulnerability data into actionable insights.
When to use a prioritization matrix
A vulnerability matrix is especially helpful when:
- You have limited resources and need to justify what to patch first.
- You're dealing with competing priorities across teams.
- You need a clear, communicable visual for non-technical stakeholders.
- You're building a case for risk acceptance vs. mitigation.
It’s a great tool for quarterly risk reviews, incident response planning, or as part of a risk-based vulnerability management (RBVM) program.
Prioritize vulnerabilities for resilience against critical threats
Vulnerability prioritization transforms endless scanning results into a clear, actionable roadmap. By going beyond severity scores to include exploitability, business impact and environmental context, organizations can focus on the vulnerabilities that truly matter. With risk-based approaches, visual tools like matrices, automation and cross-team collaboration, security teams move from reactive patching to proactive, risk-informed prevention.
In today’s threat landscape, simply detecting vulnerabilities versus prioritizing them effectively can mean the difference between resilience and compromise.
FAQs
What is vulnerability prioritization?
Vulnerability prioritization is the process of ranking security vulnerabilities based on factors like exploitability, asset importance, threat intelligence and business impact. The goal is to focus remediation efforts on the vulnerabilities that pose the greatest threat to the organization.
Why is manual vulnerability prioritization unsustainable at scale?
Manual vulnerability prioritization becomes unsustainable when organizations face thousands of potential vulnerabilities. It is time-consuming, prone to inconsistency and can overwhelm security teams. Automation and exposure management tools can help by analyzing large volumes of data and assigning risk scores.
How does risk-based vulnerability prioritization differ from traditional approaches?
Traditional methods mainly rely on severity scores like CVSS. Risk-based prioritization also considers exploitability, asset value, real-world threats and business impact. This shift helps organizations address the most relevant risks, rather than just the technically urgent ones.
Does Ivanti sell software for vulnerability prioritization?
Yes, Ivanti Neurons for Risk-Based Vulnerability Management efficiently prioritizes the vulnerabilities and weaknesses that pose the most risk to better protect against ransomware and other cyber threats.

