Not Another Phishing and Ransomware Blog!
What can I say further about Ivanti’s mobile threat defense (MTD) solution for iOS, iPadOS and Android devices that has not already been mentioned in any of my previous blogs and quick video demos? If I was to state where Ivanti has a clear advantage over other unified endpoint management competitors, it is with Ivanti’s MTD solution. Ivanti’s UEM competitors often partner with third-party mobile threat defense vendors which means the solution requires a secondary app to install onto the device. Even competitors that have their own MTD solution still require a second app to be installed. With a second app, the user might have to interact with the app to authenticate to their mobile threat defense portal and activate to start protecting the mobile device. There is a greater chance that the user may opt-out of installing the MTD protection, altogether. Even if the app is silently installed onto the mobile device, for iOS and iPadOS devices, the app has to be signed by the company's enterprise code signing certificate with every app update, or every other year when the certificate expires. This is an administrative pain to maintain and upkeep if there are a lot of corporate apps that are deployed to iOS and iPadOS devices.
Ivanti UEM Mobile employs a single agent app for UEM and MTD to manage and secure mobile devices which allows Ivanti’s platform to achieve closer to 100% user adoption, whereas a second app is closer to achieving 30% or less user adoption. The biggest battle for company cybersecurity architects and CISOs is getting threat defense installed onto mobile devices and endpoints, and then activated to start the protection from device, network, app, and phishing threats! Protection is now more important than ever. According to a recent Ivanti survey, 74% of respondents said their organization was a victim of a phishing attack in the last year, with 40% confirming they have experienced an attack in the last month alone.
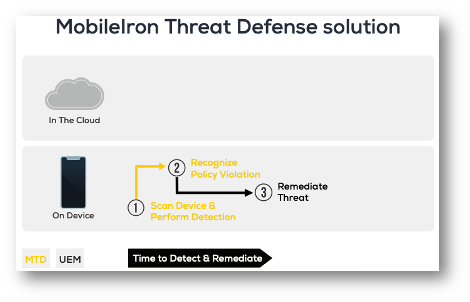
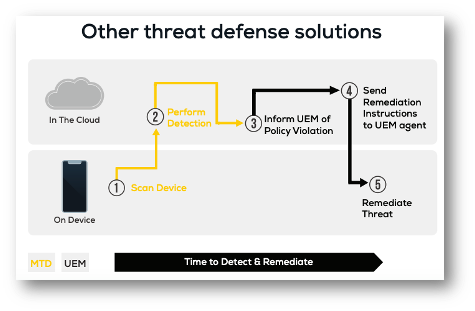
The slides below show that for other mobile threat defense solutions, they tout a lightweight agent that is cloud first and device-assisted to save on battery life. The problem there is it would take longer to detect and remediate mobile threats because the heavy lifting is done in the cloud. This could cause multiple round trips between the device and the cloud-based threat detection engine, and then to UEM to enforce a compliance action, and finally back to the mobile device to mitigate the detected threat. And, if the device's internet connection is interrupted the client engine could run in a degraded mode or leave the client brainless on the device making it unable to detect or remediate mobile threats.
Ivanti’s solution has two layers of protection. An on-device detection and remediation engine that is provisioned by UEM and works even without an internet connection to the cloud-based engine. It can detect and remediate 45 different device, network, and app threats. Even Ivanti’s phishing protection has an on-device engine that blocks the browser from landing on a malicious website. This is augmented by Ivanti’s cloud-based engine that can detect 63 different network, device, and app level threats, and assists Ivanti’s phishing protection with a cloud-based lookup engine that is updated more frequently.
According to Verizon’s 2021 Data Breach Investigations Report (DBIR), 36% of data breaches involved phishing attacks, last year. That is an increase of 11% from the previous year and it can be directly attributed to COVID-19 related spear phishing campaigns with the stay-at-home Everywhere Workplace paradigm shift that started to take effect at the same time. Sadly, that percentage is still rising and will lead to millions more stolen credentials used in more data breaches and ransomware attacks! Ninety-five percent of all attacks targeting enterprise networks are caused by successful spear phishing campaigns, and 97% of users are unable to recognize a sophisticated phishing email. Staggering numbers!
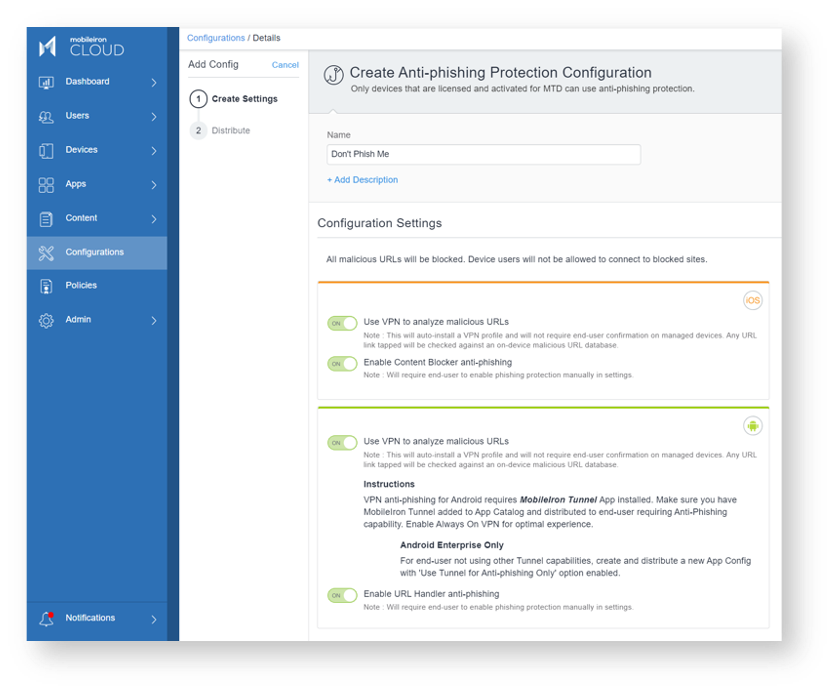
How does a cybersecurity architect and CISO counter these ever-growing sophisticated malicious cyber threat actors? They can configure both the on-device URL handler for Android devices and Content Blocker on iOS and iPadOS devices that blocks suspected malicious domains and websites when the user taps them. This is the first layer of protection. The local URL handler and Content Blocker database holds 35 MBs of data for its phishing database and machine learning classifiers. Both databases are updated every 8 hours.
This is augmented by Ivanti’s cloud-based lookup service that has its database updated every hour. On Android devices, the anti-phishing protection leverages Ivanti’s MobileIron Tunnel service. Within the MobileIron Tunnel app configuration, a UEM administrator can configure it to support anti-phishing only or also connect to an on-premises or datacenter site via MobileIron Sentry, and/or SaaS-based site in the cloud via MobileIron Access.
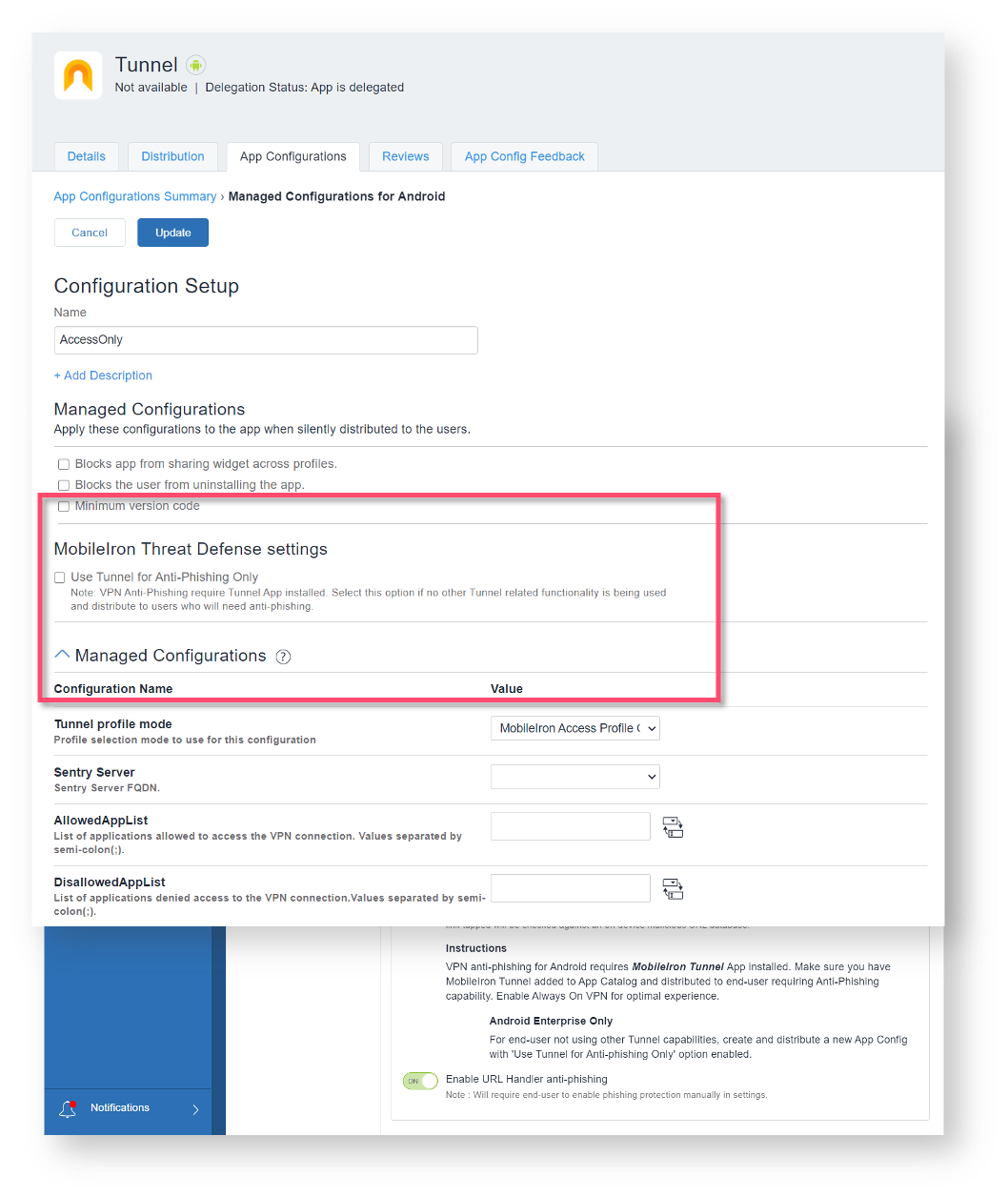
This capability is like the multi-layered anti-phishing protection on iOS and iPadOS devices also using Ivanti’s MTD solution.
Phishing and ransomware are intertwined in a malicious cyber threat actor’s exploit arsenal. Deploying Ivanti’s UEM for Mobile with MTD is a great start to fighting off these threat actors. Throw in Ivanti’s Zero Sign-On (ZSO) solution that can employ the stronger factors like inherence and possession in a multifactor authentication policy, instead of the knowledge factor that often use passwords. Passwords are the weakest link for most companies, so it is time to kill it off! #SummerOfSecurity
The demo video below highlights the power of our multiple-layered anti-phishing protection on an Android Enterprise device in a bring-your-own-device (BYOD) deployment scenario.

