How EASM Discovers Your Attack Surface Vulnerabilities
Key Takeaways
- EASM continuously discovers and monitors all internet‑facing assets using public data sources, giving visibility into known, uncertain and unknown zones of an organization’s external footprint.
- The solution automates asset inventory and identifies vulnerabilities such as CVEs, misconfigurations and exposed services.
- Prioritization uses threat intelligence to enable proactive remediation before breaches.
- Implementing EASM supports regulatory compliance, streamlines security operations, and helps manage third‑party and supply‑chain risks by exposing hidden assets and vendor exposures.
With few exceptions, businesses of any scale depend on the internet. So, it’s all-important to manage and protect the external attack surface it presents to the world.
An organization's external attack surface consists of the totality of possible entry points through which an unauthorized user can access an IT environment. This includes everything from websites, web applications and APIs to remote access points and cloud services.
Attack surface size is based on the nature of the individual organization and the extent of its digital footprint. The move to the cloud and the profusion of new digital touchpoints means most companies have seen their external attack surfaces grow.
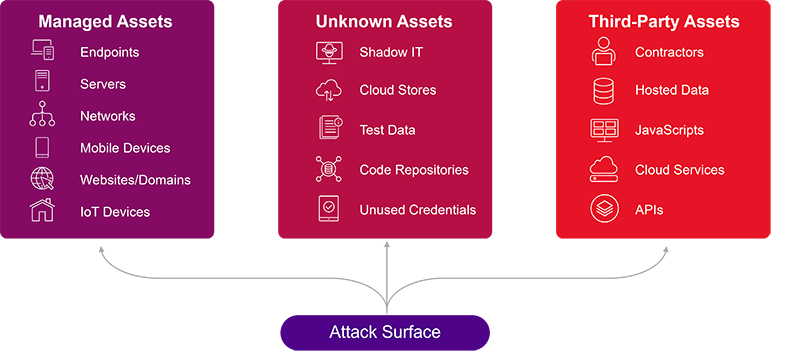
External attack surface management (EASM) is critical in bolstering organizational security and mitigating risks. Visibility being the cornerstone of protection, EASM tools provide organizations with understanding of their external attack surfaces by identifying, classifying and monitoring all internet-facing assets.
In doing this, they arm cybersecurity teams with the intelligence they need to shut security gaps, pre-emptively protecting against potential threats.
Learn more: What is an Attack Surface?
Reasons driving EASM adoption
There are multiple reasons more companies are turning to EASM solutions. Among them are the glaring examples presented by previous failures.
For instance, the WannaCry attack in 2017 exploited the EternalBlue vulnerability in Microsoft Windows, encrypting files on around 230,000 computers worldwide as hackers demanded ransoms in Bitcoin from major victims including Telefónica. Proper external attack surface management could have identified and fixed the vulnerability, preventing breaches.
A quick inventory of the reasons EASM adoption is growing:
- Rising cybersecurity threats: We've come a long way since WannaCry, as threats are more sophisticated and prevalent, with cybercriminals always evolving to exploit vulnerabilities in access controls. EASM solutions help organizations mitigate this by continuously monitoring to proactively respond to any suspicious activity.
- Increasingly complex IT environments: These include on-premises systems, cloud services, mobile devices and even post-pandemic BYOD usage. Making sure assets are secured across such diverse environments while ensuring compliance is challenging without an EASM solution to enable fast, reliable discovery.
- Regulatory compliance requirements: These primarily focus on data privacy and security and are becoming more stringent. Compliance with GDPR, HIPAA, PCI DSS and other rules that mandate strict access controls, discovery and asset inventory is difficult. EASM solutions provide the tools that help organizations stay on the good side of auditors.
- Increasing third-party risk: Many organizations rely on third-party vendors and suppliers, but this introduces additional security risks. EASM solutions help assess and manage the security posture of third-party vendors, monitor their external attack surfaces and ensure compliance with security standards and regulations.
- Phishing and social engineering attacks: Threat actors often leverage these techniques to exploit external vulnerabilities. EASM solutions help organizations monitor for phishing domains, identify spoofed websites and detect potential attacks targeting employees and customers.
Learn more: 8 Best Practices for Reducing Your Organization’s Attack Surface
The essence of EASM
External attack surface management relies on a proactive approach, whereas traditional security measures respond to threats after they’ve breached a system. EASM aims at stopping unauthorized access beforehand by using advanced tools to continually analyze the external attack surface for vulnerabilities.
Adopting EASM is different from onboarding a network or client-based security product in which most of the environment is known. External attack surface management is the opposite: Its primary use case is to discover and learn more about what isn’t known.
Moreover, EASM is a continuous process. The digital footprint of an organization is forever evolving with the addition of new services, disposal of old ones and the dynamic nature of internet-facing assets. The external attack surface is also fluctuating, necessitating ongoing management and security updates.
How EASM reduces your attack surface
The first step is identifying external-facing assets. For example, a capable EASM solution will crawl the internet to find these after a user simply enters a seed domain name.
Note that crawl is the right term, not scan, since the latter is associated with a need for connection and authentication to discover assets. In EASM’s case, the focus is on all publicly available data and assets.
When using that seed domain as input, an EASM tool conducts lateral and sub-domain discovery using publicly available sources such as DNS, WHOIS, Certification Transparency Logs, press releases, social media posts, news articles, blog posts and IP ASN. This provides a comprehensive inventory of all assets exposed to the public internet, regardless of the network, cloud provider or hosting account.
This graphic shows three broad categories of assets, organized by their visibility and exposure.
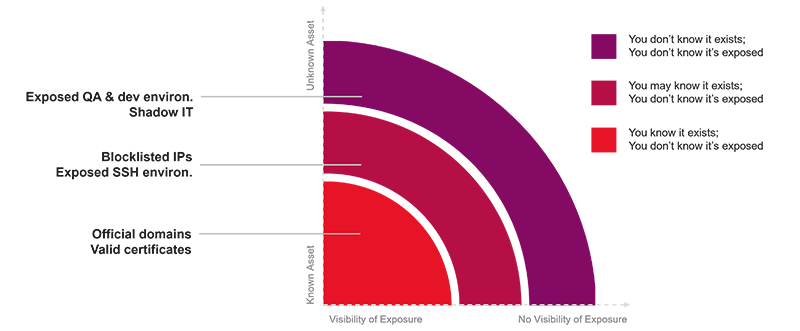
- The safe zone at lower left is where an organization knows an asset exists, even though it may not be sure if it’s exposed. This includes official domains, sub-domains, valid certificates and so on.
- The next zone is shadier: It’s where an organization might know an asset exists but doesn’t know if it’s exposed, such as blocklisted IPs or exposed SSH instances.
- The danger zone is where an organization has no awareness of an asset and therefore has no idea about its exposure. This includes exposed dev environments and shadow IT assets.
A good EASM solution can provide quick and complete visibility into all these assets, as well as insights into their potential vulnerability. It can identify known vulnerabilities (CVEs) published on NVD, as well as open ports, numerous software versions, common misconfigurations, default credential checks, secret keys, ASNs, programming frameworks and more.
If the external attack surface management solution provider operates a threat intelligence database, it will help determine which of these exposures are critical and pose the greatest threats to an organization, and they’re reported to the user.
Learn more: How to Identify Your Organization’s Attack Surface
Benefits of EASM
There are a lot of advantages from implementing an effective EASM strategy and solution:
Enhanced cybersecurity
External attack surface management significantly reduces the risk of data breaches, thereby safeguarding sensitive information and maintaining customer trust, as well as helping an organization avoid the costs and reputational damage associated with these breaches.
Improved compliance
As more regulatory and industry compliance standards such as PCI, HIPAA and GDPR are put into place, EASM-delivered security insights can discover any non-compliance. For example, knowing the geolocation of assets means a company can ensure compliance with that region’s regulations.
Streamlined security operations
EASM can streamline and optimize security operations by providing a clear and concise overview of the organization's external vulnerabilities, allowing for more targeted and efficient security efforts.
Third-party risk management
Organizations often work with a galaxy of third parties including vendors, partners, contractors and consultants. An EASM solution can provide supply-chain risk insights about any threats to an enterprise’s own security.
Better vendor evaluation
Before bringing a vendor onboard, an EASM solution can discreetly report on the vendor’s exposed cybersecurity risk. An extension of this use case is conducting due diligence for mergers and acquisitions.
See it in action: Ivanti Neurons for EASM

