Schrödinger’s Vulnerability: Why Continuous Vulnerability Management Isn’t Optional
Key Takeaways
- IT teams are struggling to test, validate and deploy patches as security teams shorten SLA timelines. Ivanti research finds that 39% of IT and security professionals find it a challenge to prioritize risk remediation and patch deployment.
- Relying on traditional, fixed patching cycles alone (like Patch Tuesday) creates dangerous exposure gaps, as modern threats and zero-day vulnerabilities require immediate attention.
- Proactive, always-on vulnerability management requires organizations to adopt a tiered patch management framework with four main tiers: routine maintenance, priority updates, zero-day response and continuous compliance monitoring.
The classic thought experiment known as Schrödinger’s Cat imagines a cat that’s simultaneously alive and dead; that is, until someone opens the box. In other words, it’s both alive and dead until the point that we can confirm the truth.
Now, swap the cat for software vulnerabilities, and you’ve got a fantastic analogy for what happens in today’s security environment. Teams won’t know a vulnerability exists until it’s discovered and in the worst cases, until it’s already being exploited.
That uncertainty is what I call Schrödinger’s vulnerability.
It’s the gap between the assumption of safety and the reality of exposure. And it’s a gap that traditional vulnerability management practices alone can’t bridge.
With threat actors leveraging automation and AI to enhance the speed and scale of their attacks, the time between the discovery of a vulnerability and exploitation is shrinking. Organizations can’t afford to waste time identifying and patching vulnerabilities.
Traditional patching methods are on a fixed cadence – once a month or once a week – but this approach is out of touch with the realities of modern threats.
Organizations need to branch out from relying just on reactive, scheduled patch management and remediation cycles. It’s time we shift our mindset to an always-on, comprehensive way of understanding a potential vulnerability – even before we know that the vulnerability exists.
The Patch Tuesday problem: real-world threats move faster
Let’s start with what we all know: Patch Tuesday is predictable. Patch Tuesday remains an important practice in helping security teams prioritize their updates and remediate newly-identified vulnerabilities. Leading tech companies like Microsoft, Apple and Ivanti itself release their updates and patches on a regular cycle, giving IT and security teams time to prepare their own maintenance cycles.
However, the problem is that many vulnerabilities aren't so predictable.
For example, popular third-party applications such as Adobe, Mozilla and Google are continuously releasing updates to common applications — such as browsers — that we all use on a daily basis.
For organizations only anchored to a monthly maintenance schedule, this can create a dangerous delay. Each time you “close the box” and wait for the next patch window, you leave a 29-day exposure gap wide open.
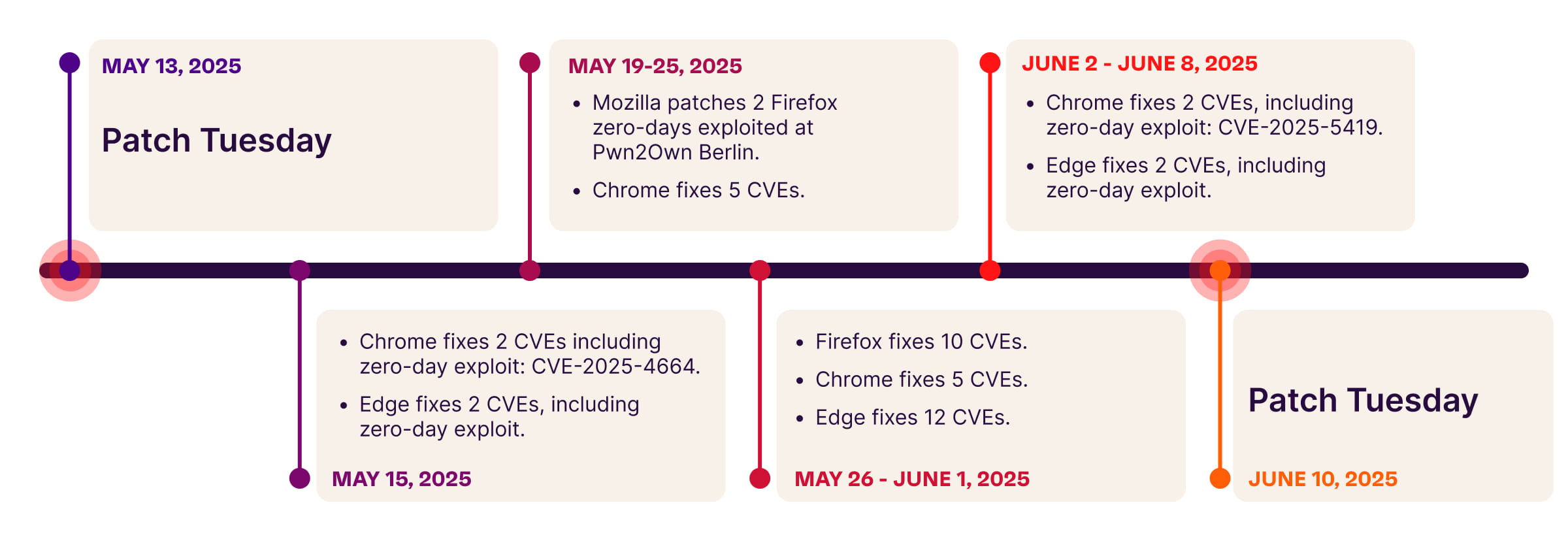
Consider what happened in the spring months of 2025: in the span of five weeks, Chrome, Edge and Firefox each identified zero-day vulnerabilities that required immediate attention:
- Two Firefox vulnerabilities publicly exploited at the Pwn2Own hacker competition
- An actively exploited zero-day in Chrome and its sibling browser, Edge
- Multiple rapid-fire CVE disclosures demanding swift action
Modern cyber attackers can reverse-engineer newly released patches to uncover the underlying vulnerability, weaponize proof-of-concept exploits and launch automated attacks.
Once a vulnerability is publicly disclosed, you enter a critical window to resolve the issue before threat actors can take advantage of it. In fact, the June 2025 zero-day in Chrome (CVE-2025–5419) was actively exploited in the wild upon patch release, underscoring how quickly adversaries can weaponize a disclosed flaw.
To extend our Schrödinger’s analogy: vulnerability management is like herding cats. And as anyone who’s tried to herd cats knows, it’s a 24/7, round-the-clock job. In other words, continuous vulnerability management is even more crucial now than before.
The IT burden: continuous releases and compressed SLAs
Threat velocity is only half the challenge. As more vendors shift to continuous release cycles, it forces security teams to shrink SLAs, sometimes dramatically. The result is often “smoke-test validation”, confirming a patch has been installed without fully checking its impact. That’s how bugs, compatibility issues and missed dependencies slip through. You’re increasing operational risk even when trying to reduce security risk. It’s like peeking in the box to see if the cat’s breathing and missing the open window behind it.
IT teams are struggling to test, validate and deploy patches at that increased pace, according to Ivanti research. Nearly four out of 10 (39%) cybersecurity professionals find it a challenge to prioritize risk remediation and patch deployment, and 35% aren’t consistently able to maintain compliance when patching.
A different approach is needed. Teams need to be more proactive and continuous in their approach. This means establishing a mindset of exposure management to be more proactive.
Risk appetite: the starting point for exposure management
Every organization has a different tolerance threshold regarding risk. That’s your risk appetite. If you haven’t formally defined that in your teams, you can’t operationalize an effective response strategy.
That’s why continuous vulnerability management starts with a conversation across stakeholders. You must bring security ops, IT and business leadership to the table to address critical questions:
- What level of exposure are we willing to tolerate?
- How fast can we realistically respond to zero-day threats?
- What's the financial, operational and reputational cost of being wrong?
The average cost of a ransomware incident is now reported as being upwards of $5 million. That’s no small sum, and especially for smaller organizations, the high costs may pose an existential threat to their business.
For enterprises, it’s more the brand damage and regulatory exposure where it stings the most.
No matter your size, these numbers demand a shift from measuring patching SLAs to actively managing exposure.
From cadence to coverage: tiered patch management framework
At Ivanti, we’ve operationalized this mindset through a flexible, layered policy framework within our Neurons for Patch Management platform. This starts with three policy tiers that align with real-world vulnerability response patterns:
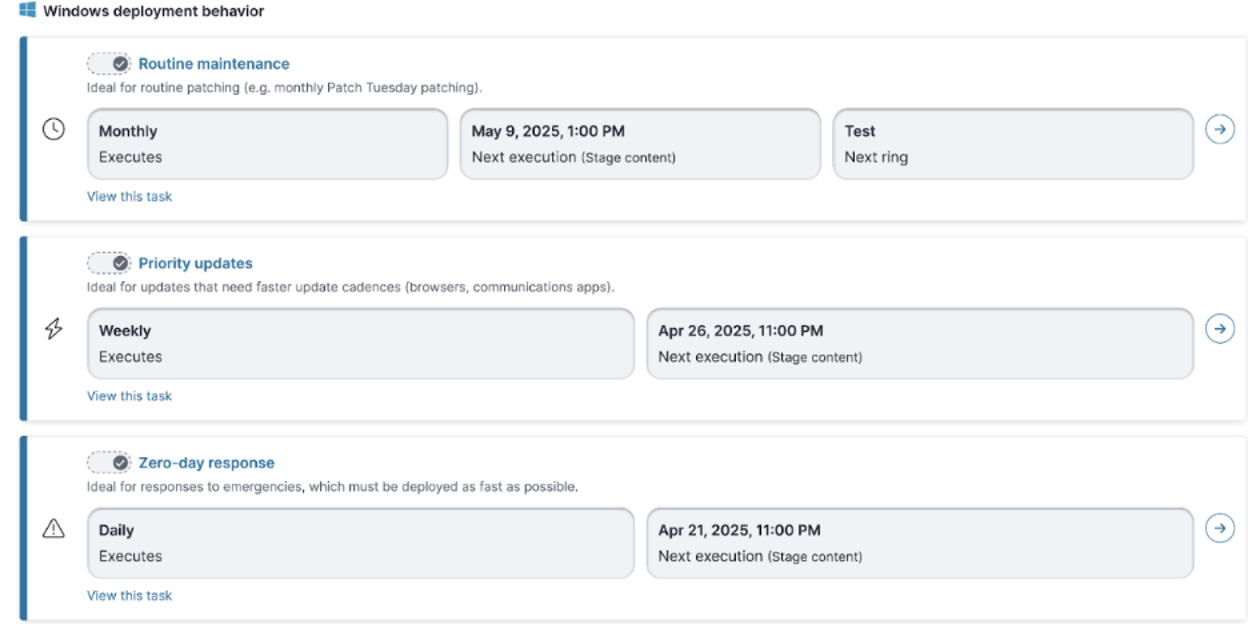
1. Routine maintenance
This is your baseline: OS updates, scheduled, third-party patches, standard hygiene. While essential, it’s insufficient if it stands on its own. You’re keeping the lights on, but you’re not ready when a storm hits.
2. Priority updates
Browsers, collaboration tools and document apps change constantly, making them prime targets for exploitation. Because of the perpetual change and evolution of these apps, they require faster response cycles and purpose-built policies. We’ve created default configurations to help customers proactively manage these risk-prone applications with minimal friction.
3. Zero-Day response
Agility matters most here. When a zero-day is discovered and disclosed (or worse, exploited), you don’t have time to debate or argue about what to do in response. You need preconfigured, battle-tested policies that you can pivot to immediately and patch outside your normal cycle.
These three tiers running parallel to each other give organizations a starting point for moving beyond cadence-based patching. They operationalize the concept of risk appetite by matching prescribed response urgency to the nature of the threat.
Multilayered vulnerability management and continuous compliance
Not every system is perfect, though. What happens when something falls through the cracks?
Maybe an employee was on vacation. Maybe a system was turned off. Maybe a new device was integrated without the latest patches. These are the edge cases that create silent, persistent risk. These are your very own Schrödinger’s vulnerabilities.
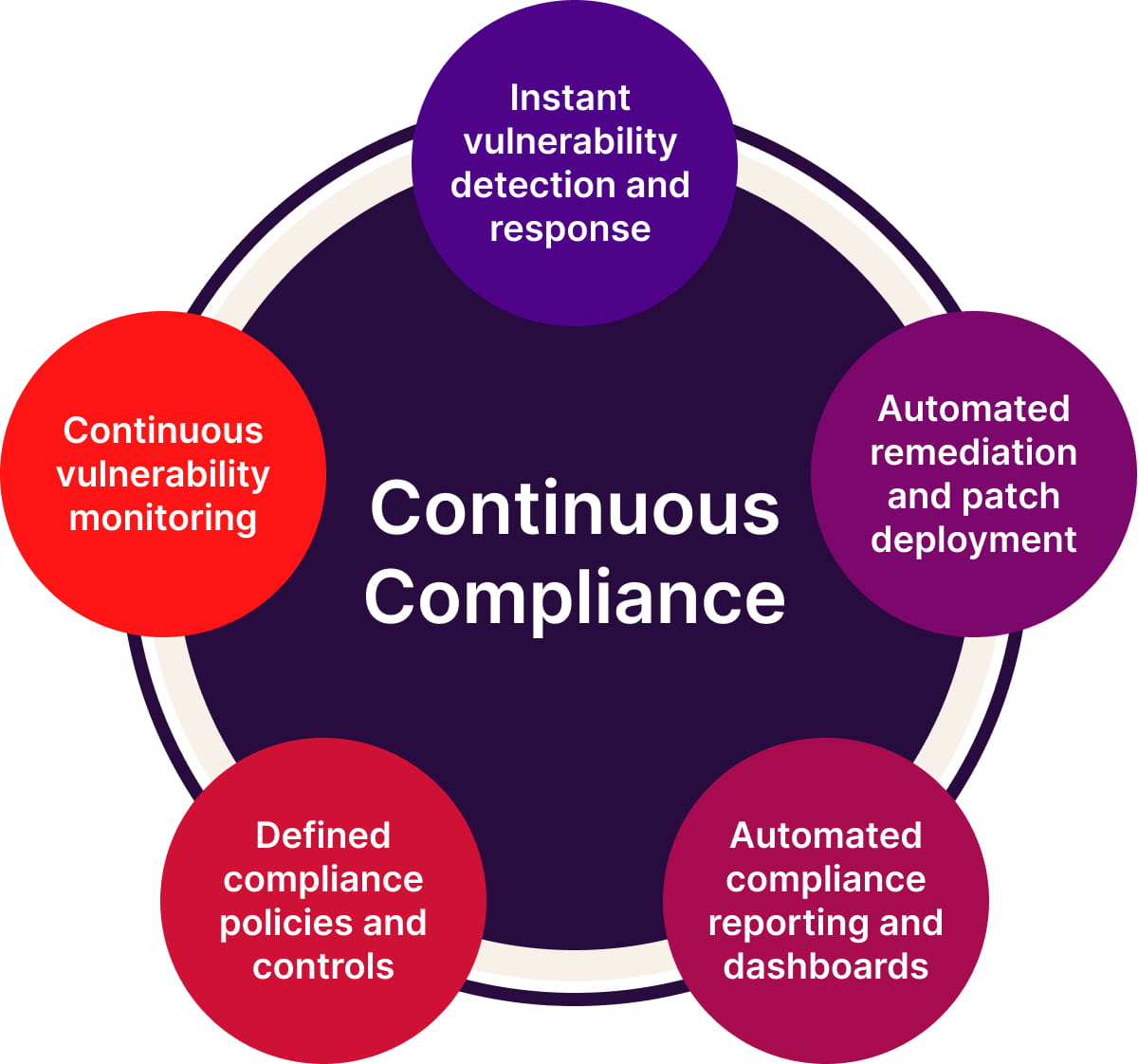
To solve this requires a fourth remediation track: Continuous Compliance.
This task runs in the background. It monitors for devices that don’t meet your latest patching baseline from routine to zero-day. When it finds gaps, it closes them automatically. It’s like a bank’s vault automatically locking shut when thieves trigger the alarm.
There’s no need to wait for the next Patch Tuesday or have someone manually watch the dashboard 24/7. This is where true continuous vulnerability management takes shape. Ongoing coverage (and security) rather than manual reaction.
Shrinking the noise: focus on what matters
There’s another critical benefit here: dramatically reducing the volume of noise your security teams have to triage.
Take July’s Patch Tuesday. Microsoft released patches for 104 CVEs. Let’s do the math: say you have 3,000 Windows 11 machines in your user base. That means more than 300,000 “findings” for your vulnerability scanner.
But here’s the thing: if your exposure management program is doing its job, 99% of those findings are already addressed and accounted for in your routine maintenance, priority updates or in your zero-day response tasks. No more needing to parse through mountains of redundant alerts – your team can now home in on what needs real attention, including gaps, anomalies and uncompliant systems.
That’s how you move from reactive alert fatigue to active risk reduction.
From patch management to preparedness
This, ultimately, is a mindset shift. You’re moving from a reactive model to a proactive one. You’re shifting from waiting for vulnerabilities to surface and deciding what to do about them, to responding with predefined and automated processes firmly in place.
That’s the difference between simply patching and being prepared. It matters more now than ever, with CVE counts rising and threat actors faster, smarter and better resourced.
Regulatory expectations are also growing. Whether it’s SEC disclosure rules, National Institute of Standards and Technology (NIST) frameworks or industry-specific compliance mandates, the bar for “reasonable security” is climbing.
The baseline has changed: it’s no longer patch and react. It’s continuous vulnerability management.
Not falling for Schrödinger’s vulnerability
Back to the cat. The whole point of Schrödinger’s Cat thought experiment is that uncertainty persists until you look.
That’s fun in concept, but it’s dangerous when you apply that mentality to cybersecurity. You can’t just hope you won’t get hit — you must manage risk through continuous monitoring, patching and enforcing.
With the right measures in place, you’re not opening the box wondering if a vulnerability is “alive” or not. You’ve already taken steps to keep it safe. You can open with confidence and then shut the window of exposure before it even becomes an open door.
Discover more best practices to elevate your current patching and remediation efforts to a proactive, high-performing security strategy in our full Risk-Based Patch Prioritization Report.
FAQs
How does an organization’s risk appetite inform their approach to continuous vulnerability management?
Organizations first need to define their risk appetite, the levels / types of risk they’re willing to accept before they can configure the different priority levels for their multiple remediation tracks.
What are the different tiers of a multilayered remediation strategy?
Multilayered remediation uses a tiered patch management framework with four main tiers: routine maintenance, priority updates, zero-day response and continuous compliance monitoring.
Does Ivanti sell products to help achieve continuous patch remediation and compliance?
Yes, Ivanti Neurons for Patch Management automates and tracks SLAs for multiple parallel patch deployments and continuously monitors and remediates devices to ensure they remain in compliance.

