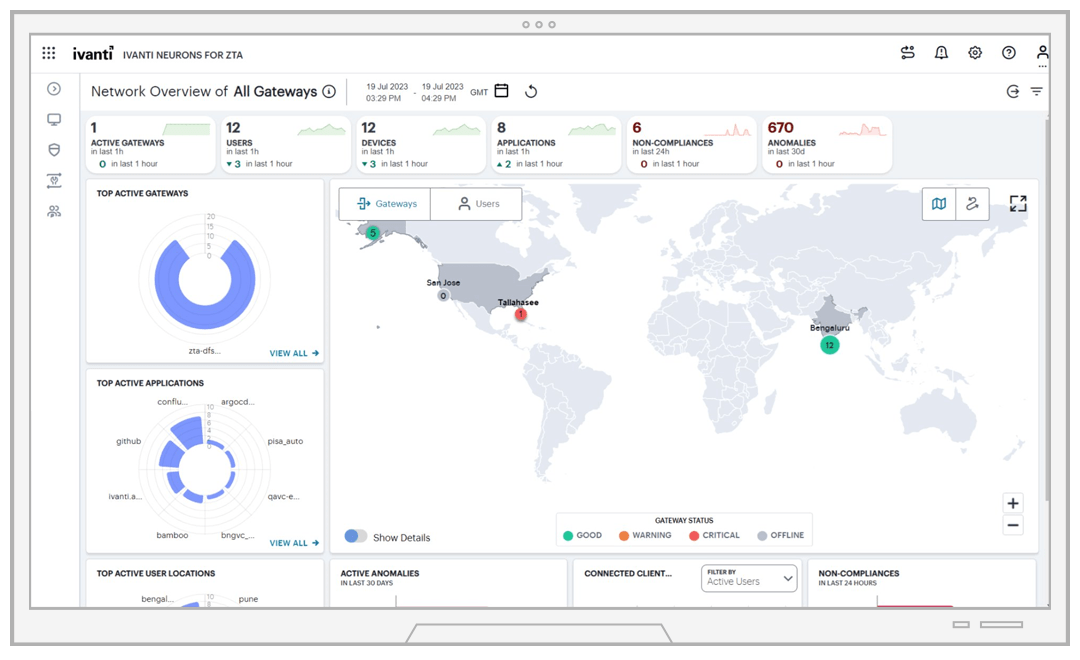
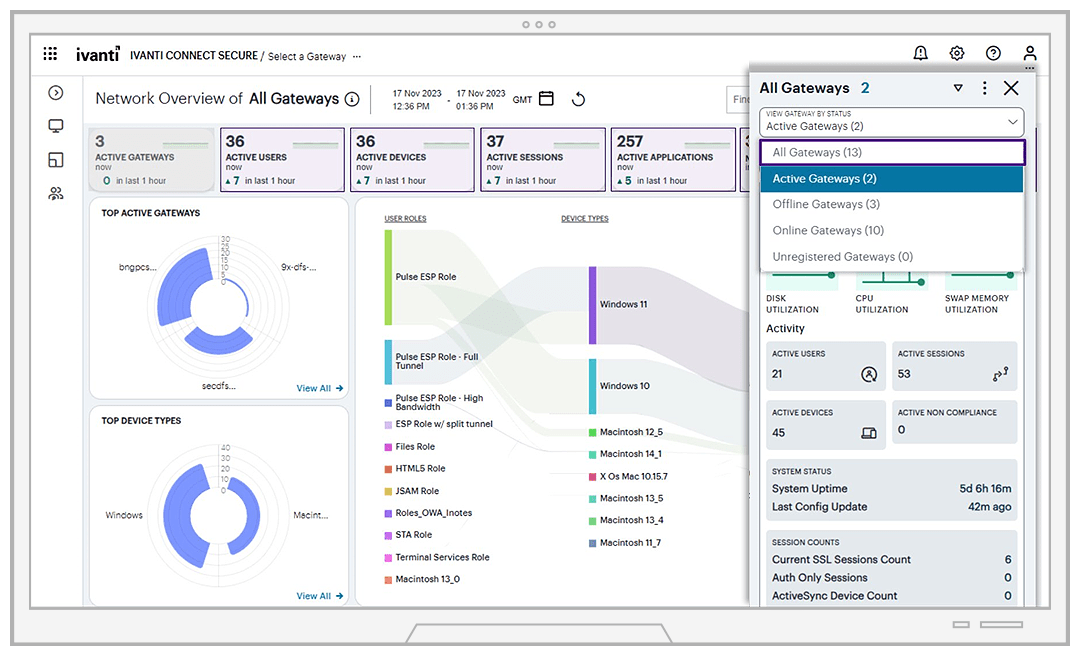
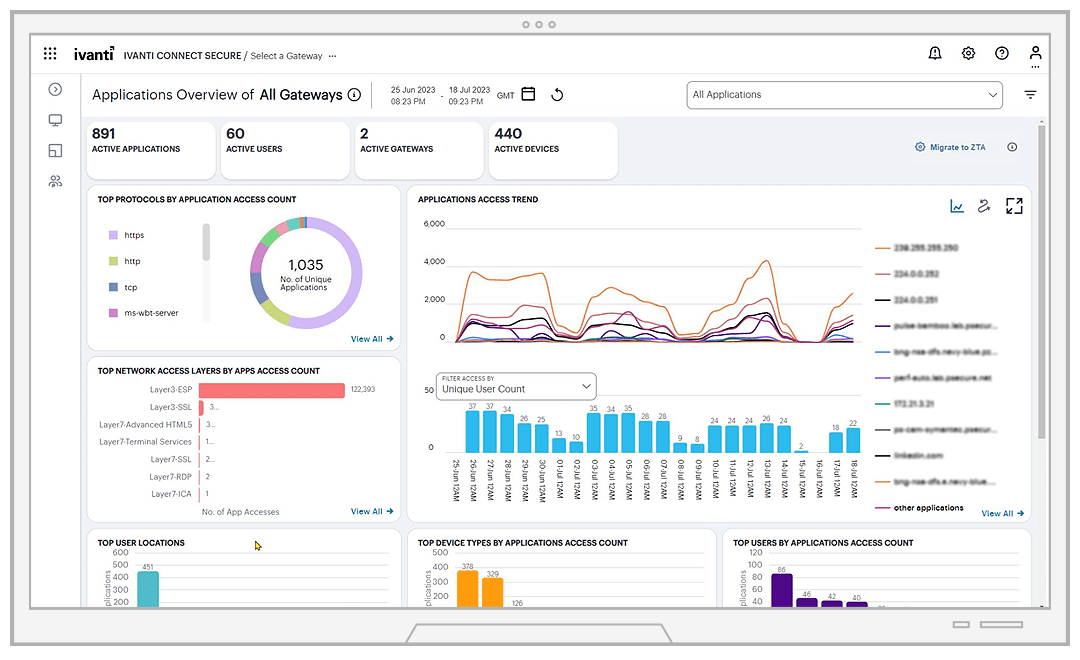
Providing secure unified access to all applications, anytime and anywhere, and reducing business risk while strengthening security posture is top of mind for enterprises, Ivanti network security solutions make it easy to leverage existing on-prem VPN investments while gradually adopting cloud analytics and management capabilities aligned to your budget and resources. The advantage: Expanded visibility across your entire estate with a single-pane view of gateways, devices, users and applications.
Secure by Design
Security measures are integrated from the beginning of the development process to ensure products are inherently more secure, reducing vulnerabilities and risk of cyberattack