Blackbaud Ransomware Attack Data Breach
 Sometimes you can do a lot of things right, but still appear to have gotten it wrong. As I pieced together information regarding the Blackbaud data breach, it became clear they are doing many of the right things. Like many organizations, there are always too many priorities, too many projects, and too many shifting variables that allowed a sophisticated threat actor to launch a double-extortion attack.
Sometimes you can do a lot of things right, but still appear to have gotten it wrong. As I pieced together information regarding the Blackbaud data breach, it became clear they are doing many of the right things. Like many organizations, there are always too many priorities, too many projects, and too many shifting variables that allowed a sophisticated threat actor to launch a double-extortion attack.
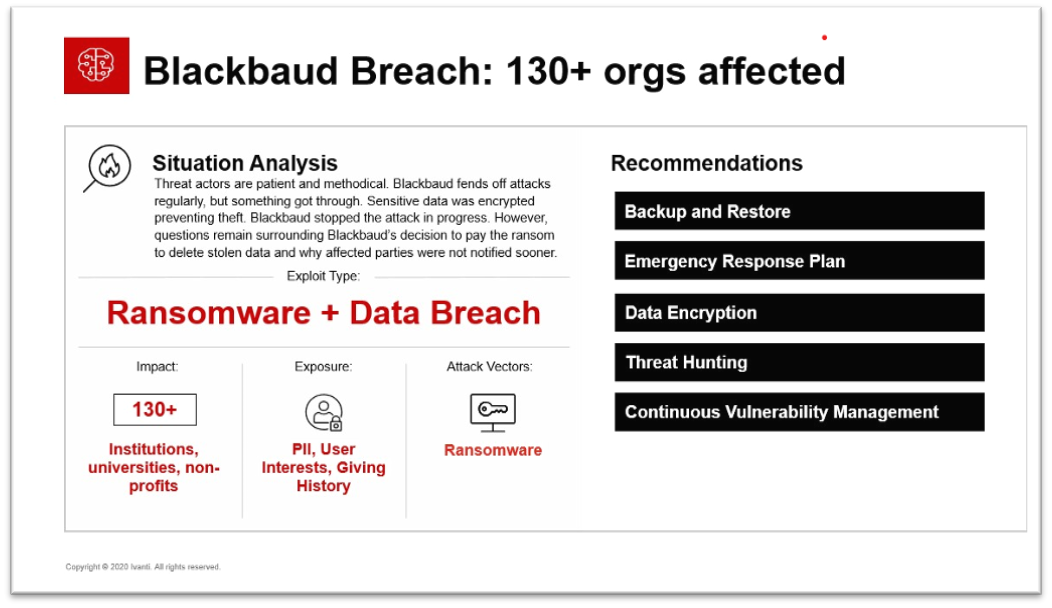
Threat actors have found that ransoming the critical data isn’t enough. Now they steal the data then encrypt it, so they have double the leverage on the victim. In this case, the attacker was thwarted during the exfiltration of data so they were not able to get a second lever on Blackbaud by encrypting the data for ransom as well, but that was still enough to extort a ransom.
Blackbaud is an organization that appears to take security seriously. This quote from TheNonProfitTimes outlines their security focus:
“We follow industry-standard best practices, conduct ongoing risk assessments, aggressively test the security of our solutions, and continually assess our infrastructure. We are also a member of various Cyber Security thought leadership organizations, including: The Cloud Security Alliance and Financial Services Information Sharing and Analysis Center (FS-ISAC), where we team up with other experts to share best practices and tactical threat information for the Cyber Security community,” said the spokesperson.
The article goes on to talk about Blackbaud President and CEO Mike Gianoni’s response indicating Blackbaud’s security and operations teams were able to stop the attack as it was occurring—that they have analyzed the attack and have already taken measures to prevent this from happening again. From those steps you can discern some of the issues that led to the breach. They are enhancing their capabilities around access management, network segmentation, and deploying additional endpoint and network solutions to plug gaps the threat actors likely exploited.
It appears that Blackbaud did a lot of things right leading up to and post breach, but there are a few things that have come into question. First, Blackbaud paid the ransom. Law enforcement agencies around the globe urge victims not to pay ransoms. It incentivizes threat actors to continue and does not guarantee you will gain access to your data or that they will not target you again. Second, Blackbaud delayed their response to customers who fell victim in this case. There was a two-month delay in response to those whose data was affected. Under GDPR and other data privacy acts this is a significant issue.
Let’s Pro\Con Blackbaud’s performance in this incident:
- Pro: Blackbaud has a reportedly strong security practice. They defend against a large number of attacks regularly. In this case they were able to detect and respond as the attack was occurring.
- Con: Blackbaud paid the ransom. This is not recommended as it can entice threat actors to continue their practices and possibly re-target Blackbaud in the future as they know Blackbaud will pay.
- Pro: Blackbaud has responded with a post-mortem evaluation, a response plan enacted to plug security gaps, and a third-party assessment to ensure those new countermeasures have been successful.
- Con: Blackbaud delayed disclosing the data breach to the affected parties, effectively delaying their responsiveness. In this case the type of data that was exposed is less sensitive, but still can be used to socially engineer targeted attacks if they got the right data on important persons. A lot of donations would come from people who would be ideal targets for fraud attacks.
What should we take away from this incident?
- Constant re-evaluation of your security posture is necessary. Blackbaud reportedly performs this type of activity and evaluates themselves against proven security frameworks.
- Continuous Vulnerability Management is critical. Discovery, Vulnerability Assessment, and Patch Management are critical to close gaps.
- A combination of Preventative and Detect and Response is critical. Blackbaud may be blocking many attacks each month, but this one got through. Prevention deflected a lot of risk, but Detection and Response stopped this incident from being much worse.
- Vendor Risk Management is a critical activity. Blackbaud is a service provider that many organizations have put their trust in; not unwarranted either from what I can see. Who are you putting your trust in? What data do they have access to? What security measures do they take? MSPs are becoming a more common target for threat actors as they can affect many organizations all in a single attack, maximizing their efforts.
Each month please join Ivanti CISO Phil Richards, and me, Chris Goettl, director of product management for Ivanti’s security solutions, for our Ivanti Threat Thursday webinars as we discuss the latest security-incident insights and trends.

