Implementing the ACSC Essential 8: Top Considerations
2022 saw the number of cyber incidents and their scale and impact grow exponentially.
After a two-year pandemic where many businesses have suffered to some degree, with looming financial uncertainty, maximising return on investment is a key driver for many on their security journey.
We all know skilled resources are hard to find, hard to hold on to and hard to budget for, so supporting their work through automation is a key strategy to do more with less.
Enter the ACSC Essential 8 – a security framework when implemented appropriately and using the correct tooling, can have three major outcomes:
- Improving your security posture by protecting against 86% of targeted threats.
- Reducing manual effort to complete common cyber hygiene related work.
- Minimising the impact of security measures on user experience and productivity.
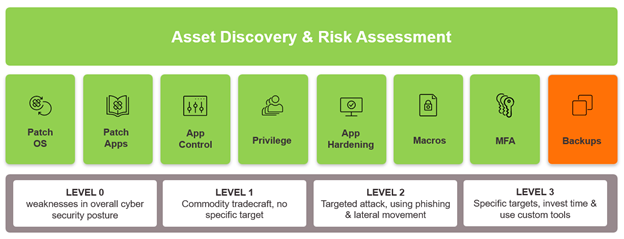
Understanding what you are protecting
Each organisation looking to adopt the ACSC Essential 8 needs to understand what they are trying to protect; from the applications that exist in their environment to the devices they are trying to secure. Maintaining a full real time asset inventory and performing a risk assessment of those assets is a key step to implementing the framework.
Understanding the level of maturity you are aiming for, the controls you need to implement and ensuring they are a good fit for your organisation, is fundamental to your planning.
Many basic tools used to complete patch management or application allow-listing come as part of the Microsoft toolset and enable customers to achieve a basic level of maturity for select controls. However, customers typically tell us these tools come with a large management overhead and associated operating costs.
When you need a more advanced level of maturity or to reduce workforce effort and operational costs when implementing and maintaining ACSC Essential 8 compliance, Ivanti can help.
Our solutions are designed from the ground up to automate, simplify and provide great user experiences, and reduce operational costs, all while driving higher compliance and maturity.
Which controls and how to implement?
The ACSC recommends that when deciding how to implement the controls organisations should consider the threat that concerns them most. We will look at two common ones here:
Targeted cyber intrusion
When an organisation is targeted due to the sector they operate in, the IP they hold or the sensitivity of the information they work with, preventing malware delivery and execution while limiting the extent of any incident is a key strategy.

Ivanti helps our customers implement Application Control to ensure only approved applications, scripts and binaries can execute on machines, reducing the chances of malware and macro attacks.
For over 20 years, Ivanti’s solution has reduced implementation and ongoing maintenance workload for thousands of organisations.
This is done with a focus on reducing the manual effort to manage lists of approved items, providing flexible and contextual policies and empowering users by providing simple exemption workflows when required.
Patching applications is key to limiting many targeted attacks that use known vulnerabilities, especially in commonly used third-party applications. Adversaries know these applications exist on many machines but are not routinely updated or patched to the same cadence as Microsoft and other operating systems.
Ivanti provides a full catalogue of third-party application updates, allowing you to patch hundreds of applications with almost no manual steps, reducing the cost and time to deploy, and has been securing assets for nearly two decades – assisting thousands of customers and OEM partners worldwide.
Ransomware
For many the fear of a ransomware attack is very real. We all have stories of ransomware attacks etched in our memories. Ransomware is an attack vector that not only disrupts but destroys and sometimes leaves an organisation crippled with months of work to rebuild their business.
The recent collapse of a local housing development company listed a cyber-attack as one of the key triggers behind their demise.
Ivanti helps protect you by ensuring only approved applications can run and users only have the privileges they need to complete their job. So, whether ransomware is introduced by email, download, macros or external devices those executions are denied with no excessive privileges available for compromise.
Many ransomware attacks use known vulnerabilities to attack and later, to move laterally. Protecting against this through regular patching is another key strategy.
Do you know which CVEs are associated with ransomware? Do you know if and where those CVEs are exposed in your environment?
Ivanti’s unique risk-based approach to patching OS and third-party apps shows you where to focus first to protect your most important assets from the biggest risks. Reducing your attack surface by prioritising your team’s focus to achieve quick wins means a better security posture with effort optimised.
Our platform provides visibility of patches that close ransomware exploits and where they need to be applied, leaving your team to automate remediation with a few clicks.
Why Ivanti for the ACSC Essential 8?
If you would like to know more on how Ivanti can help you to implement 7 of the ACSC Essential 8 all from one vendor and help you gain real time visibility to the assets on your network, please have a look at our ACSC compliance site and check out our videos, case studies and testimonials.
You’ll find information on:
- Reducing cyber exposure against common threats.
- Limiting and reducing manual effort of implementation and operational overhead.
- Reducing user impact.

