You Can Fly Round the World in 48 Hours but Can You Patch a Server?
It is becoming increasingly more difficult for organisations to keep up with the ever-growing security patching requirements. More stringent guidelines are being introduced, such as the Australian Cyber Security Centre (ACSC) Essential 8. To meet the highest level of maturity of the essential 8, an organisation must patch and secure critical security vulnerabilities within 48 hours of the release of the patch or discovery of the vulnerability.
The 48-hour turnaround time can be difficult to meet due to:
- Ineffective deployment methods;
- Red tape with process; and
- Lack of adequate reporting.
What happens in the wild?
From my personal experience with large organisations the complexity of the environments makes patching security vulnerabilities within a 48-hour time frame difficult. A combination of the complex environments, manual processes and stakeholder engagement inhibit the ability to make the time frame.
On the flip side in organisations that manage to meet this requirement tend to skip over the required processes. An outcome of this typically a lack of reporting and verification of the patching being completed.
What’s the best approach?
With those issues in mind it’s obvious a very mature streamlined and automated approach is required. An approach that can tie in the deployment method, the required processes and reporting on the results.
The flow on effect of building such a solution gives the added benefit of further streamlining standard patching. Increasing the confidence with stake holders and allowing for resources to be better utilised compared to the current manual resource driven patching processes many organisations still utilise.
How can Ivanti help?
A good place to start is Ivanti Security Controls (ISEC). ISEC allows you to patch both operating system as well applications for Windows and Linux. ISEC also allows the choice of agent or agentless patching, meaning you can avoid adding yet another security agent to the endpoints. Furthermore, ISEC also has the capability to take the output of vulnerability scanners allowing you to automatically convert a list of Common Vulnerabilities and Exposures (CVE) directly into a list of patches. Ivantis CVE to Patch technology is a great time saver you no longer have to have resources completing repetitive tasks to produce the patch list.
For the 48 hours patching use case pairing ISEC with Ivanti Automation is a must. The automation platform can control every step based on the defined processes of an organisation. This can be achieved using the Ivanti Automation Connectors allowing Automation to tap into ISEC, Service Management platforms (such as Ivanti Service Manager) as well as the Automation platform itself performing required health checks that are part of the process itself.
The final part of the puzzle is reporting and the tool for that is Ivanti Xtraction. Xtraction is a real-time intelligence platform. It allows you to build reports from multiple sources across vendors into easy to understand dashboards. Xtraction can be used to report on the patching status across an organisation allowing for easy single pane of glass view for the compliance status.
Putting it all together
Bringing all these pieces together is the real art behind successfully creating a process to meet the 48 hours critical patching requirement. From our experiences here at Ivanti a simple strategy utilising this approach would typically look like this: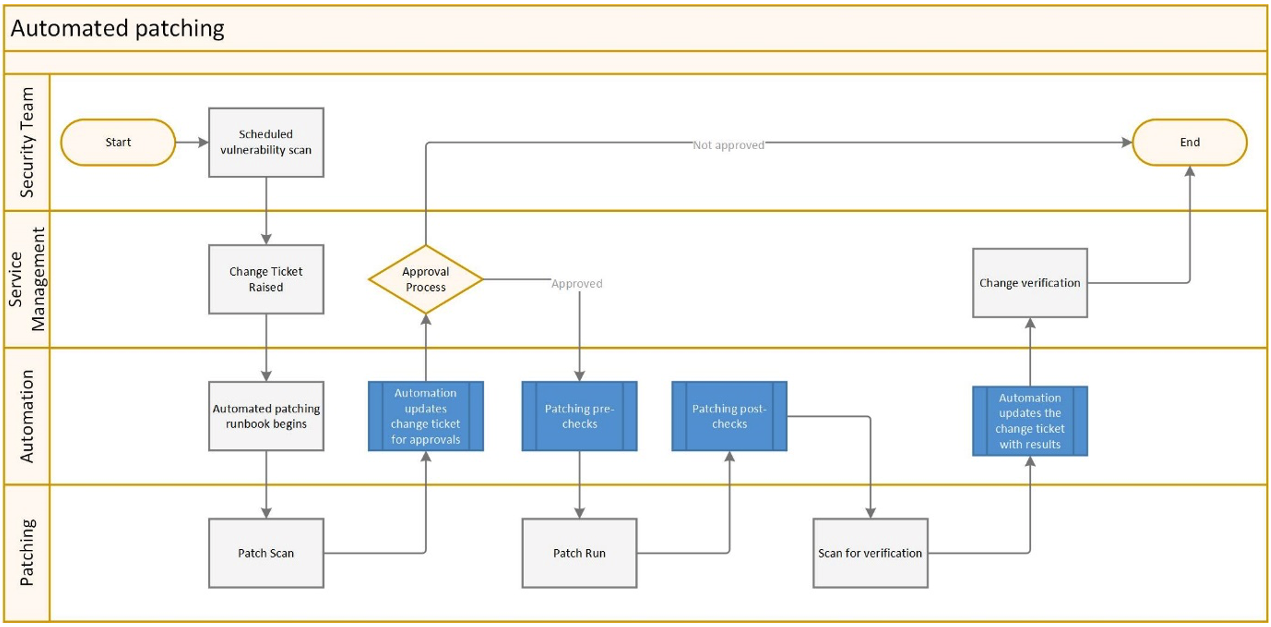
Underpinning all of this with Xtraction, allowing a live dashboard view of the whole process to be monitored.
The Ivanti approach allows for one vendor to cover this process, from the patch management, service management, reporting and automation. Also, for organisations that already have partial coverage Ivanti can plug the gaps to bring it all together.
What next?
Ivanti have a nice short demonstration of all aspects of the automated patching and reporting which can be found here.
If you would like to have a chat regarding automated patching you can reach out to us from our homepage.
