State of the Union on Security: The Framework of CIS Critical Security Controls, Pt. 3 of 3
This last in a series of three posts recaps the final portion of the presentation that Chris Goettl, Ivanti’s director of Product Management for security solutions, presented at the recent IT Leadership Summit virtual event that’s available on demand.
Part 1 in this series, State of the Union on Security: The Rise of Nation-State Activities, discusses the rise of nation-state activities and a new evolution of cyber-attacks: the use of ransomware as a social and economic disrupter rather than a direct impact to attempt to get a payout. Part 2 in this series (State of the Union on Security: SamSam Attacks and the Need to Prioritize Risks) focuses primarily on SamSam attacks, including the one that hit the City of Atlanta in March of this year, and the importance of prioritizing risks in order to deploy the appropriate tactics to mitigate them.
CIS Controls—A Proven Security Framework
One of the ways we help customers focus on their security challenges is through the Center for Internet Security (CIS) critical security controls framework. The CIS Controls are recognized as best practices for securing IT systems and data against the most pervasive attacks.
The CIS framework embodies 20 security controls, and it’s been proven that implementing the Top 5 controls can mitigate or eliminate 85 percent the cyber threats we face today. Being able to focus on and eliminate the majority of that security exposure by applying a small subset of the overall framework makes you more effective. Again, this is about prioritizing effectiveness.
Much of what we need to do in securing our environments is evaluating things based on an 80/20 rule. How do you gain 80 percent of the value with 20 percent of the effort? You can actually realize upwards of 85 percent effectiveness in the security program by implementing the first five of the 20 controls. So, 25 percent of the work, 85 percent of the benefit. That's a pretty good payout for prioritizing your effectiveness.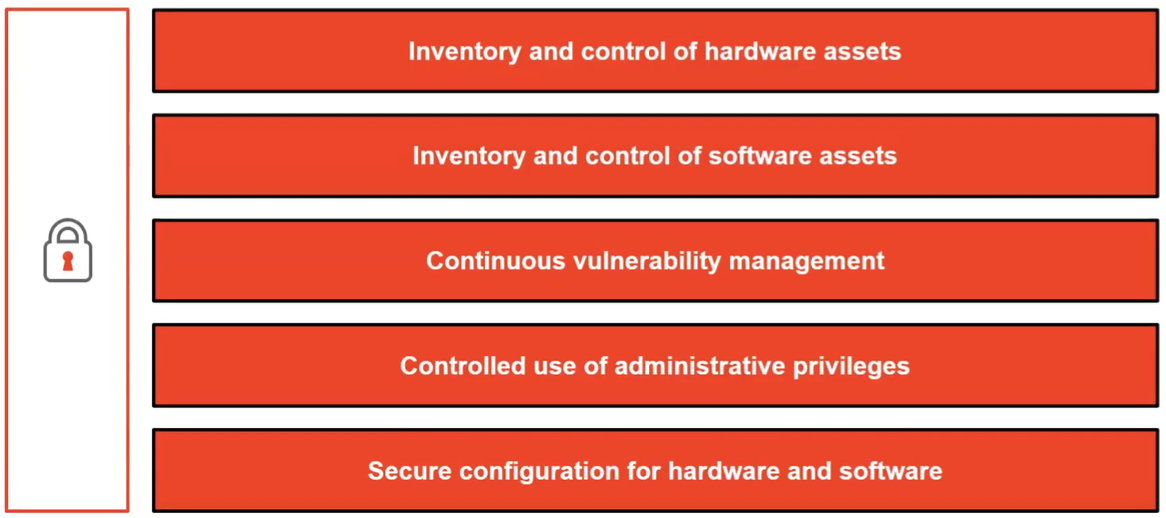
Inventory and Control of Hardware Assets
If you can't see devices and know where they are, you’re blinded to your security posture. You don't know what you don't know. So, you need a solid discovery program and then manage those assets all throughout. You need to understand the age of those assets, not just from a "Hey, do we need to refresh hardware?" costing standpoint, but also from a vulnerability standpoint. If you know you've got devices running on an older operating system, or running on hardware that will not receive firmware updates to defend against hardware vulnerabilities like Meltdown and Spectre, you can start to identify what’s exposed to older vulnerabilities and replace them.
Inventory and Control of Software Assets
This means actively managing inventory tracking and correcting software vulnerabilities on your network so that only authorized software is installed and can execute. And anything unauthorized or unmanaged can be prioritized for removal from the environment.
Continuous Vulnerability Management
This entails assessing and taking action continuously on known vulnerabilities in your environment. So, in order for this third control to be effective, you will have identified the software in your environment. By the same token, in order for the second control to be effective, you will have established a good inventory of a hardware in your environment. So, the controls here are prioritized in a way where each one of them becomes more effective because the first one was done.
In order to assess and manage vulnerabilities continuously, we’re really talking two different sets of technologies here. You have your security team and your vulnerability management software—your Qualys, Nessus, Tenable, Rapid7—whichever vulnerability vendor you're using, and then you've got your patch management solution from Ivanti, Microsoft, or other vendor.
These two groups and sets of capabilities need to work together to close those vulnerability gaps. Again, software vulnerabilities make up the largest part of the attack surface. Limiting how much of that surface is exposed helps close and lock the doors and windows.
Controlled Use of Administrative Privileges
Concerning some of the attacks we discussed before, many times a software vulnerability is exploited by attackers first getting on one system and then launching untrusted tools that shouldn't belong in the environment. And with those tools, they will compromise valid administrative credentials in the environment.
From there, by using a valid credential from your environment and readily available tools that you yourself utilize, attackers can use those capabilities and methods that are harder to detect.
So, the dilemma is, how do you filter through and scrutinize behavioral patterns when it's a user that you’ve created and it’s the tools that you've given access to? On one system, where that's being used against you in a malicious way versus one where it's being used in an approved way, how do you distinguish between the two? Letting these things occur makes the detect-and-response portion of a cyber security incident that much harder. So, we must lock these things down so attackers don't have these tools available.
Secure Configuration for Hardware and Software
This control is about making sure you’ve got good firewall rules and password complexity. It’s also about locking down vulnerable cipher suites, protocols, and applications running in your environment with hardened configurations. This extends to you IIS servers, SQL servers, etc. And again, with these Top 5 controls working together, you can mitigate or eliminate 85 percent of the threat right there.
Access the IT Leadership Summit Virtual Event to Learn More
Chris Goettl speaks in greater detail about these Top 5 CIS controls in the IT Leadership Summit virtual event that’s available on demand. Take some time to view the presentation, plus learn about how Endpoint Security solutions from Ivanti can help you mitigate the bulk of cyber threats.

