Is Your Patch Process Hurting End Users’ Experience? Here’s How to Fix It
Key Takeaways
- Poorly tested patches can disrupt business operations and damage user experience.
- Ring-based deployment rolls out patches in phases, reducing risk by catching issues early.
- Gathering user feedback during each patch stage helps identify and address problems before broad impact.
- Combining ring deployment with user surveys builds trust and meets security compliance requirements.
Just one bad patch can cause key systems to fail, disrupting your teams and, ultimately, your customer experience.
While I was checking out at a supermarket self-service machine, the screen suddenly froze and then dreaded blue screen of death appeared. A nearby staff member quickly came over and, with a bit of a sigh, said it was the third time that day this happened. While I’ll never know for certain whether a patch was the only cause, businesses want to minimize these types of issues.
One bad patch can impact your organization, too. Imagine your customers unable to contact your client success team or your frontline workers unable to access critical data.
While you could delay patch deployment, you run the risk of a total company outage due to a ransomware breach or other cyberattack.
The reality is that vulnerability remediation requires never-ending vigilance. You can address many vulnerabilities through patch management, but without adequate testing, critical systems and business services can get disrupted, affecting your teams and, in short order, reducing profitability.
Let’s take a look at how poorly managed patch updates can cause major disruptions. I’ll also discuss how a ring-based deployment strategy, combined with user surveys after each stage of the rollout, provides a safer and smarter way to mitigate vulnerabilities and outages.
Patch deployment: The need for speed
Regular patch management is one the best ways to secure your data and services. Security frameworks provide best practices, guidance and standards for customers to adhere to; for example, CIS Controls v8 guides teams to apply critical patches in less than seven days, and remediation must occur faster (within 24 hours) if a vulnerability is part of the CISA KEV list.
Organizations comply with these (and the other controls) to reduce risk of catastrophic breaches, maintain regulatory compliance and reduction cyber insurance costs.
In addition, vulnerability exploitation surged by 34% compared to last year (2024). Ransomware-as-a-Service (RaaS) has transformed cybercrime into a subscription economy, where low-skilled attackers can rent powerful ransomware kits from dark web marketplaces. This model dramatically lowered the barrier to entry, fueling a surge in global attacks and extortion attempts.
Now, with the integration of artificial intelligence, threat actors can automate reconnaissance in attempts to locate vulnerable targets at speed. All this makes proper patch management more essential than ever. When a critically rated vulnerability is identified (e.g., a zero day), deployment speed is crucial — but you must balance it with control. Ring deployment acts as an early warning system by rolling out updates in controlled waves.
Ring deployment for secure, scalable patch management
Ring deployment for patch management is a phased approach to rolling out software updates or patches across an organization. Devices are grouped into “rings” based on risk tolerance and criticality. This tried-and-true method helps reduce the risk of widespread disruption by detecting and resolving issues early in the deployment cycle.
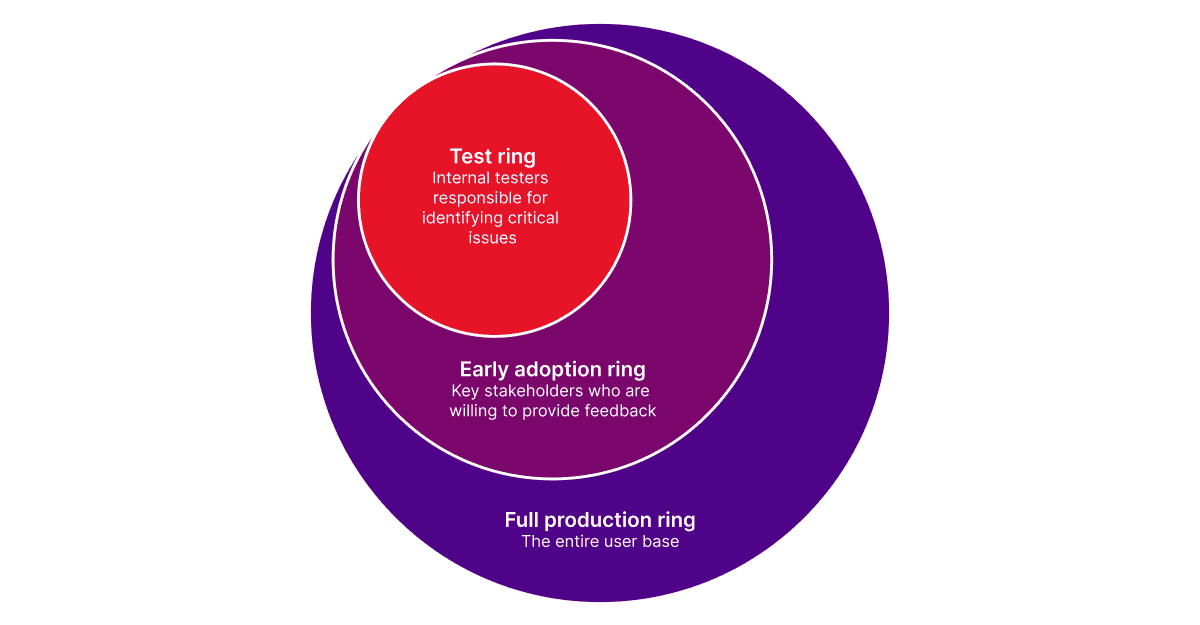
And it gets even more powerful when you combine it with telemetry from devices and user sentiment. Direct user feedback during each ring allows IT to deploy at scale and maintain speed.
Combine user surveys and ring deployment to stay ahead of potential patch issues
It’s that time again: your organization is rolling out a patch to address a critical vulnerability.
You start with a ring-based deployment — a small group of IT staff and early adopters gets the update first. This initial phase helps validate that the patch installs cleanly without breaking core systems. Once it clears that stage, the patch moves to the next ring — maybe 500 general users from non-critical departments.
With this quantity and diversity of devices, user feedback helps you determine if the overall update worked and can even help you identify when downstream issues may occur before you move onto the next ring.
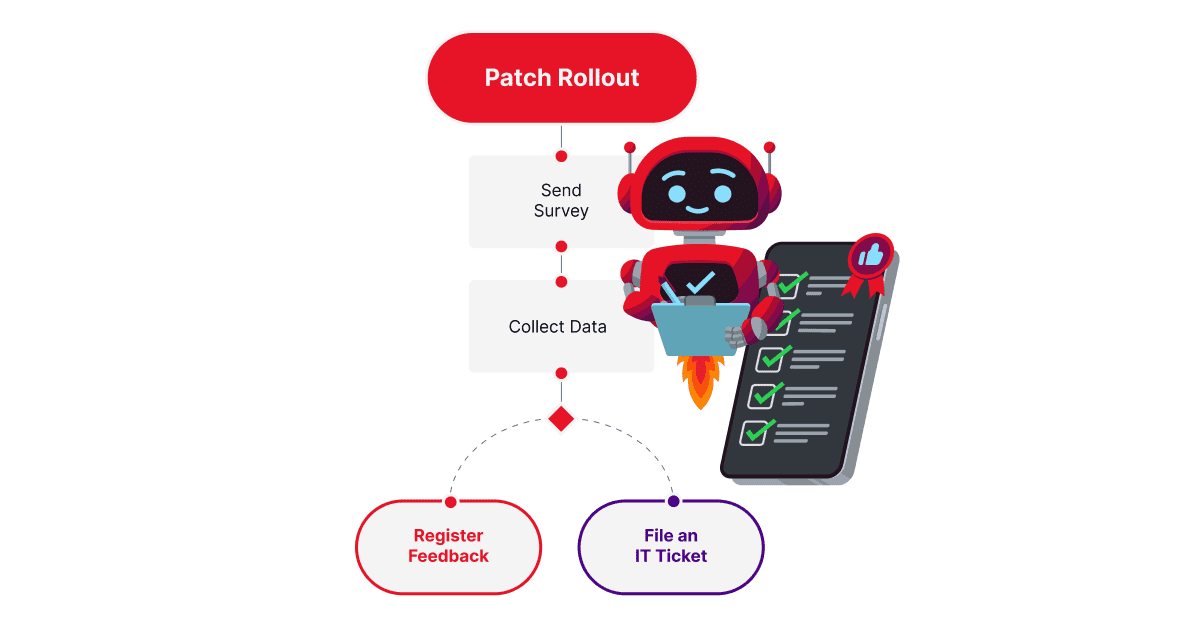
In your user surveys, collect feedback on:
- System performance.
- Usability.
- Post-patch issues experienced by users in the current ring.
This way, you can gate your rollout — if survey results reveal a high rate of negative feedback or unresolved issues, pause the deployment for investigation and remediation. Open support tickets, gather device logs and alert your IT team.
This feedback loop ensures that only stable, well-received updates advance, reinforcing trust in IT processes and reducing the risk of vulnerabilities making it into high-impact environments, like your customer care center.
Scale your security posture and minimize disruptions with ring deployment and user feedback
When you combine ring deployment and patch experience user surveys, your organization can successfully deploy all critical patches in a timely manner, meeting both security best practices and compliance requirements. Systems are secure, risks from known vulnerabilities are reduced and auditors can see evidence of a timely, controlled process.
Ivanti Neurons for Patch Management helps you make patch deployment a seamless process by surveying users directly in the patch experience, automatically pausing rollouts if survey results reveal issues or users respond negatively.
Remember, patching is never truly finished—new vulnerabilities are disclosed daily, and the next cycle of updates is already on the horizon. Staying secure means repeating this process consistently, ensuring that each patch cycle closes today’s risks while preparing for tomorrow’s threats.
FAQs
Why can patching cause disruptions to business operations?
Patching can cause disruptions if updates are not properly tested or if compatibility issues arise, potentially leading to system failures, downtime, or degraded user experience.
What is ring deployment?
Ring deployment is a strategy for software updates where new features are introduced in incremental stages, or “rings,” starting with a controlled group and broadening the scope to a larger user group over time.
How do user surveys support patch deployment?
User surveys collect direct feedback about system performance and usability after a patch, helping IT teams identify problems and gauge user satisfaction during each phase of the rollout.
Does Ivanti sell patch management software?
Yes, Ivanti Neurons for Patch Management is a cloud-native patch management solution that prioritizes and patches vulnerabilities based on active risk exposure, patch reliability and device compliance.

