IT Asset Management, a Three-Tiered Approach (Part 2 of 4)
Key Takeaways
- Define and classify assets, distinguishing monitored (user‑controlled) versus unmonitored (IT‑controlled) and decide which to track.
- Select agent-based discovery tools that can scan networks, integrate with directories, and import data from spreadsheets or RFID/barcode scanners.
- Choose a flexible asset database that supports custom fields, external linking, and integrates with ITSM to enable tier‑2 and tier‑3 lifecycle management.
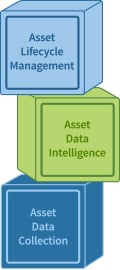
4 Steps to IT Asset Discovery, tier 1 of IT Asset Management.
Collecting IT Asset information is the first tier of any IT Asset Management strategy. This is where you build your database with assets that will be tracked. It is important to have a strategy for collecting, storing, and monitoring these assets. To begin you IT asset management project, start with these four steps to successfully collect your information.
First, you must define IT assets that need to be collected. Second, you need to identify assets that need to be monitored. Third, choose scanning tools that meet the requirements defined in step one and two. Fourth, choose an IT asset database that allows you to add and map custom fields
- Define IT Assets that Need to be Collected
Define IT Assets that will be managed and added to the database. Start by identifying assets controlled by the end-user. PCs, laptops, mobile devices, and associated software applications are often lost or misplaced overtime when not accounted for in an IT asset management solution. Next, consider tracking printers, network devices such as routers, switches, servers, and storage, with their associated applications.
- Identify IT Assets that need to be monitored
The level of tracking applied to an IT asset will vary. A good way to differentiate the level of tracking is to have "monitored" devices and "unmonitored" devices.
Monitored devices will generally be the devices controlled by the end-user like a laptop or PC. These assets are usually at the greatest risk for security attacks. Monitored devices generally need a service or client that runs on the device. The monitored device needs to be able to report changes quickly since it has to react to change. Servers and their associated applications should also be considered for monitoring.
Unmonitored devices would be devices that are generally controlled by IT, such as network printers, routers, and switches. These devices are usually changed proactively. Network devices under the control of the IT Management system should still follow ITIL principles relating to Configuration Change Management. Remember, “Unmonitored” refers to the level of tracking, not to be confused with monitoring/managing software that may be used to configure and alert on the health of the IT asset.
Mobile devices will usually fall somewhere between "monitored" and "unmonitored" but whatever is decided, they need to be tracked. At the very least, IT needs to know what mobile devices are connecting to and what is accessing the organization’s data.
Integration between your ITSM solution and your asset management solution should be part of your strategy. If an IT asset is serviced, the incident management tool should be able to view details about the asset from the asset management system. For example warranty, contract information, and installed software may be helpful to an analyst working the incident.
- Choose the right asset discovery Tools
Agent-based asset discovery tools have the ability to recognize everything that is connecting to your network. They also have the ability to collect detailed hardware information, including manufacturer and part numbers from various components of an asset.
For example, in addition to being aware of a laptop, information about the memory, hard drive, and monitor can be available to you if, and when, you need it. Furthermore, asset tools can provide you with the operating system information running on the laptop and any software application installed.
Choose a tool that can accomplish network discovery by accessing network directories such as Active Directory and that can do ping sweeps; even listen to network management protocols such as SNMP. You want to know an asset exists and the type of asset discovered.
The tool you choose should also allow you to manually input IT assets into the management system, often using forms. For example, a smaller company may want to track the lifecycle of assets but are not concerned with detailed information beyond the fact that it exists. A form can be created for end-users or an admin to enter the required information into the database.
Be sure to choose a tool that can import the asset data from an external data source. Make sure the software can talk to an external databases. Because spreadsheets are the most common tool used for IT asset management in organizations today, it is important to have the ability to access data from XML files, Excel files, or delimited-ascii files.
Many organizations use scanning tools, such as bar code scanners and RFID scanners. When building IT Asset Management, integration with mobile scanning tools should also be a requirement
- Identify the Best IT Asset Management Database
When you consider gathering the assets with all associated components and software, the amount of data collected can be extensive. As you prepare for tier two of IT Asset Management, you will want to carefully choose your asset management database and database tools.
Make sure the tools you choose allow you to extend the database with custom fields. For example, you may want to know the name of the person who scanned in a device with a barcode scanner.
If you cannot customize your asset management database to accommodate your requirements, then you are restricted by the limitations of the database. IT Asset Management Database tools must have the ability to add custom fields, to map IT assets to custom fields or link IT asset information to external sources. For example, you may want to link a mobile device to its associated account and service provider.
Processes defined at tier 1 are designed to get your IT Assets into your IT asset management solution. Processes defined at tier 2 normalize the database tables for consistency and accuracy. Tier 2 processes also map IT assets to others or to custom data that you define. Processes defined at tier 3 are aligned with ITAM principles for tracking the lifecycle of the asset.
The more information you collect and properly manage at tier 1, the better prepared you will be when implementing tier 2 and tier 3 of your IT Asset Management solution.