Introducing Neurons For Secure Access – Saving Time While Providing Unified Visibility and Management For Distributed Ivanti Connect Secure Deployments
Where were you when VPN went from "nice to have for IT staff to remote in on the weekends" to "mission critical for the entire organization" almost overnight in March of 2020? Many companies were caught off-guard, with admins across the country taking a mad scramble to make sure their VPN solution is modern, sized to fit the demands of the remote workforce, and secure for their users. Many of our Ivanti Connect Secure customers (formerly Pulse Connect Secure) found themselves needing to stand up multiple virtual Connect Secure gateways around the world to keep up with the surge in demand from their users.
During these difficult times, we received a lot of feedback around the challenges of managing large Ivanti Connect Secure (ICS) deployments across multiple regions, and much of this feedback focused on time. It took a lot of time to manage these gateways, as each gateway needed to be individually managed and updated, and tasks like reviewing user activity could be challenging if the user was connecting to multiple gateways in different regions, requiring admins to pull logs from each gateway individually then collate that data themselves. This could be a lot of work, and very time intensive for admins who were often already under a time crunch to begin with.
With Neurons for Secure Access, we hope to give back much of that precious resource – time – as possible, while giving admins a centralized management platform which allows them to view their entire ICS deployment from a single pane of glass, track their users across multiple gateways with ease, schedule reports to be generated and delivered on a schedule that works best for them, reduce management overhead for tasks, and give them visibility into user’s risky behavior.
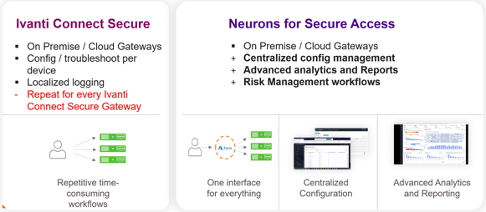
Figure 1 - Neurons for Secure Access consolidates administration, simplifies workflows, and saves time
Even better, Neurons for Secure Access is cloud hosted on Microsoft Azure, and is designed to exist as a management plane on top of your existing ICS deployment, without altering user connection flow or data sovereignty. Your organization’s sensitive data remains in your control, and the way your users access your ICS deployment does not change with Neurons for Secure Access.
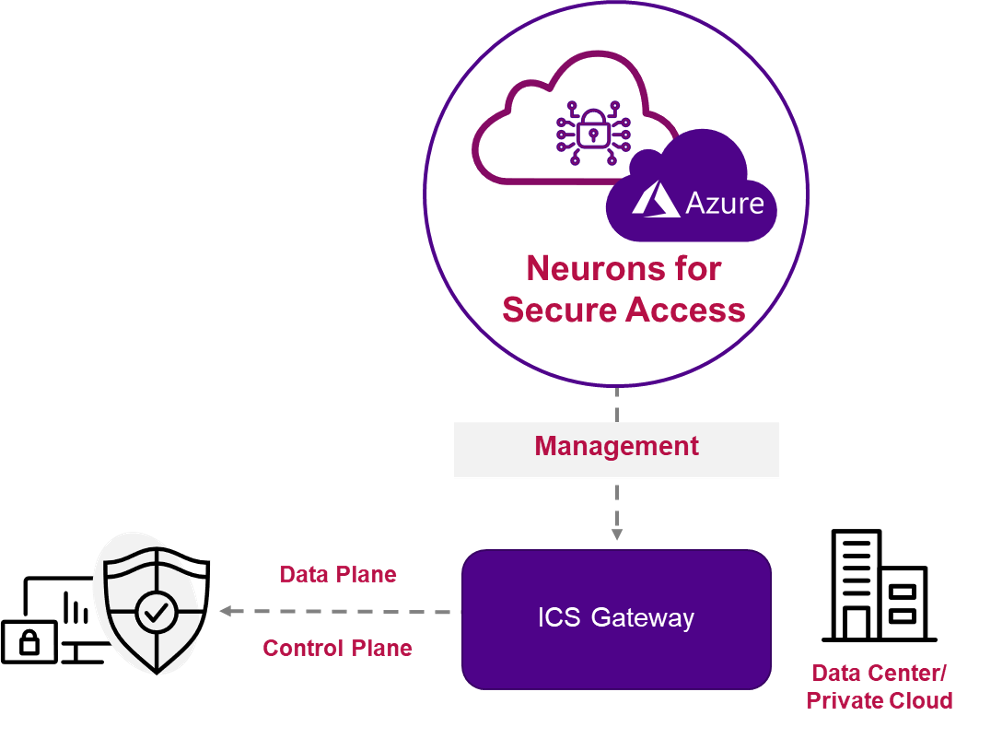
Figure 2 - Neurons for Secure Access exists above existing ICS deployments with no production data flow change
Unified logging brings new levels of visibility and accountability to distributed ICS deployments. Logs are collated automatically, meaning no manually combining log records to track activity. Further, advanced filter tools let admins apply as many filters as needed to drill down to the exact data they desire, then save those filters for future reference. Neurons for Secure Access also introduces custom reports, allowing administrators the ability to create their own reports with charts and graphs of activity data and schedule those reports to arrive in their inbox when they need them.
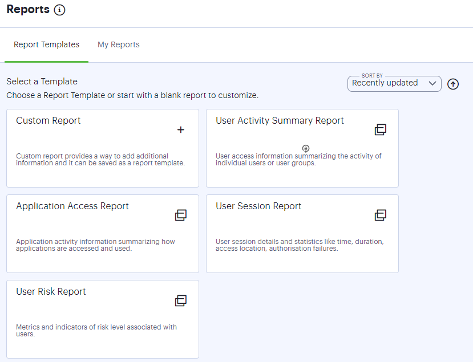
Figure 3 - Custom scheduled and on-demand reporting
Neurons for Secure Access also introduces user risk scoring, a method for detecting and acting upon risky or compromised user behavior, such as multiple logins from different times, devices or locations that are outside of the user’s normal behavior patterns. All these activities are formulated into a User Risk Score, allowing admins to take quick action when abnormal user activity occurs, no matter what ICS Gateway users are connecting to across the organization.
Finally, and probably the best part from a time savings standpoint, Neurons for Secure Access introduces “one button” upgrades of ICS Gateways. Upgrading an enterprise ICS deployment was often a huge undertaking, with each Gateway needing to be updated manually, a process that could potentially take hours for gateways across slow connections. Now with Neurons for Secure Access, administrators are automatically notified when updates are available for their gateways, and can upgrade each gateway with a single click, no more hunting for the right upgrade package!
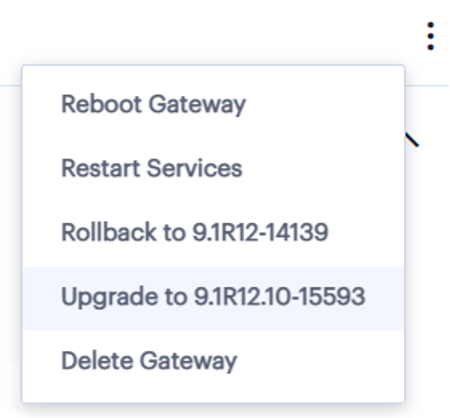
Figure 4 - One Click Gateway Lifecycle Management
Neurons for Secure Access brings convenience, visibility, accountability, security, and time savings to distributed ICS deployments, all without installing new software or redesigning your user workflows. Reach out to your Ivanti sales representative today for more details on Neurons for Secure Access, including a demo and free trial.
