Hear From A Customer: Making the Everywhere Workplace a Reality
Key Takeaways
- Ivanti Workspace Control gave Syntrophos a single console to provision shortcuts, drive mappings, printers, and enforce context‑aware security policies, including managed applications, website, and certificate controls.
- Azure Active Directory integration and the Ivanti Cloud Relay tunnel let the organization extend IWC to corporate laptops outside the network, closing the remote‑work gap created by COVID‑19.
- Recent additions such as FSLogix Office Container support for Outlook cache and the Authorized Owners feature based on NTFS ownership improved user experience and stopped untrusted software execution.
Syntrophos is the Shared Service Center (SCC) for four municipalities on the island of Voorne Putten and the Regional Archive of Voorne Putten, The Netherlands.
Rico Roodenburg, Senior Workplace Management Engineer at Syntrophos, is responsible for designing physical and virtual workplaces. He is an SME when it comes to setting up, maintaining and automating IT services, and wrote the following blog about his experiences making the Everywhere Workplace a reality.
New infrastructure
At the beginning of 2019, we set up a completely new infrastructure for our end-users. Hardening, security and a seamless user experience were key for this project to be successful. Our end-users work with important and especially sensitive information from citizens, so it is very important that our information provision is equipped with the best security measures, and that our employees can help citizens quickly.
Ivanti Workspace Control
An important part of the new infrastructure is Ivanti Workspace Control (“IWC”). With IWC it is possible to easily set up and manage the entire virtual and physical workplace from A to Z. Configurations like shortcuts, drive mappings, printers or security policies can be delivered just-in-time and are fully context-aware.
Management of the user environment can be very complex and multiple disciplines are often involved. Ivanti Workspace Control provides the right discipline and the correct permissions so that all actions can be handled from one console.
Security
For Syntrophos, security is the most important and powerful component of the product. For example, the product includes the following security features.
- Managed Applications
- Website Security
- Authorized Files
- Authorized Certificates
- Authorized Owners (newly added in the 2022.1 release)
With the Managed Applications features, we can prevent unauthorized applications and executables from being used in the IWC managed user workspace. This prevents potentially harmful applications and executables from causing damage.
- Only applications that our team makes available to the user through the Workspace Control Console are authorized. All other applications are unauthorized and are prevented from starting.
- The end-users are prevented from running executables that they might receive through e-mail or the Internet. This prevents potentially dangerous executables containing viruses, spyware, and malware from contaminating the corporate network.
Integration
IWC offers various integrations with major well-known products such as Citrix, Microsoft App-V, and SCCM. But also, with Ivanti their products such as Automation, Identity Director, Virtual Desktop Extender, and Neurons for Edge Intelligence.
Challenges
Just after everyone got used to the all-new infrastructure, COVID-19 came knocking on our door and we had to switch to the work from home scenario. Initially, it was no problem at all for us, after all, we had a fully equipped Server Based Computing environment that could be accessed safely by any user from outside.
But then came the practical challenge. Although the SBC environment was available to everyone who has an internet connection, almost none of our employees was equipped with a corporate laptop. This was something we never thought about, something we had no experience with at the time because we had our complete SBC concept with thin clients which had always been suitable, until now. The infrastructure wasn't set up in a way that was forced upon us by Covid-19.
In a short time, we were able to offer a corporate laptop solution to the SBC environment using SCCM, Intune, and Microsoft Azure. The machines may now have been fully managed and secured, but the user experience was not the same as in the office.
Although users could not perform any application installations, they could launch portable apps. This is something that is, of course, not desirable from an information security perspective.
At that time, IWC did not yet have integration with Azure, making it impossible to distribute configuration to Azure users and groups. In addition, the laptops were not connected to the internal network, so the cached configuration of the IWC agents could not be updated in any way.
Help was on the way
This is where Ivanti came up with some new powerful solutions which we currently are evaluating. Until now, our team is very excited about the results and after further testing and evaluation with the team, we consider taking the next step of putting this into production.
- Azure Active Directory integration
- Cloud Relay
With the Azure Active Directory integration, it was now possible for us to distribute managed shortcuts to our users on devices that are members of the Azure domain. This enabled us to manage the entire workplace from A to Z again on these Everywhere Workplace™ devices.
But how do you get the configuration that is on an internal database pushed out to the agents that aren't connected to the internal Relay Servers? Correct! Through the Ivanti Cloud Relay tunnel!
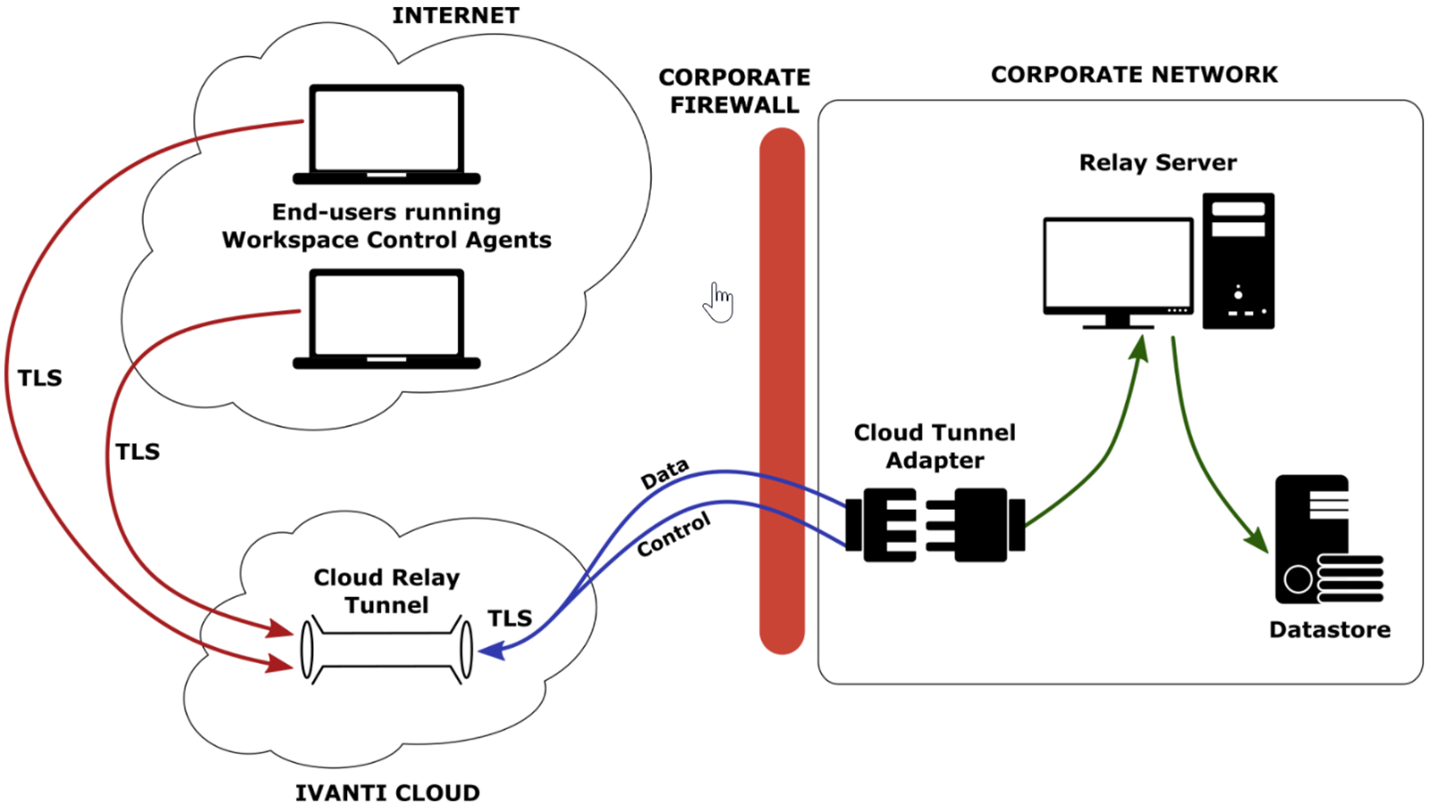
The Ivanti Cloud Relay Tunnel is an easy to implement and secure solution which allows the up-and-download processes of the IWC agent to connect to the Ivanti Cloud. Within the corporate network, one or more Cloud Relay Adapters need to be deployed which then provide the connection between Relay Servers and the Cloud Relay Tunnel. This way, only IWC related configuration, and logging data can flow from the corporate network to the agents and vice-versa.
So that’s it?
The software engineers behind the IWC product do not sit still, on the contrary! In addition to the above functions, the following functions have also been added to the product in the past year.
- Integration with FSLogix
- Authorized Owners
The integration with FSLogix Office Containers helped us save the Outlook cache after we migrated from an on-premises Exchange server to an Exchange online situation. Without negatively affecting our user's login times! Existing User-Settings could still be used for any of the other legacy applications. This way, the administrators or even end-users could still revert to any of the available versions of the saved application configurations.
The introduction of Authorized Owners increases the security of our Workspace Control environment by not allowing untrusted software to run. Untrusted software is software that is not installed by company authorized entities, such as administrators or automation accounts.
The feature is based on NTFS ownership and enables administrators to allow applications to be started only if the file owner of the executable matches the configured NTFS owner list. Because of all these developments, we can continue to develop our user- workplace without any worries.
