This week in cyber threats: A suspicious Google Docs email and Intel's VPro vulnerability
Ivanti employees were recently alerted by Michael Lloyd, security engineer, that a scam email had surfaced and was spreading quickly. It resembles a very convincing Google Docs invitation, and may even come from someone you know. Here's a screenshot:
Google Docs scam
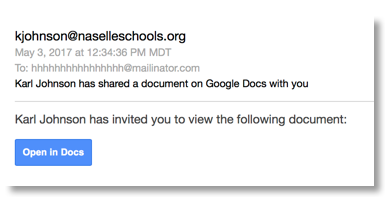
If you click "Open in Docs," you will be asked to allow more access to your Gmail account (which Google Docs would not do). Then it spams everyone in your contacts with the same Google Docs link. Those contacts will email their contacts, and on it goes.
"I recommend a healthy level of paranoia and that people activate Google 2-Step Verification," says Ivanti security expert Chris Goettl.
At Ivanti, we're encouraging employees who receive this email to send it to [email protected] and then delete it. The biggest red flag to watch out for is the [email protected] in the “To:” address. However, it might be best to avoid clicking any weird-looking Google Docs link for the time being.
Related: Clickbait, clones, and cash grabs: Sidestepping the scams on social media
In other news...
Intel chips have had a security flaw since 2010 that could potentially lead to spyware. This makes it possible for hackers to log into a computer's hardware and tamper with it.
"If you're using a machine with vPro and AMT features enabled, you are at risk. Modern Apple Macs, although they use Intel chips, do not ship with the AMT software, and are thus in the clear," states Chris Williams from The Register.
Here is what our CISO, Phil Richards, had to say about the issue:
"On May 1, Intel announced a significant vulnerability in their VPro platforms. VPro is a technology developed by Intel as their set of management and security features built into PCs that makes it easier for a sys-admin to monitor, maintain, secure, and service PCs. The discovered vulnerability allows escalation of privileges on the remote computer that can allow an unprivileged attacker to gain control of the manageability features provided by these products. This vulnerability has a CVSS score of 9.8 (out of a maximum of 10) meaning that the exploit is easy to do and grants privileged access to the hacker.
Fixes for this weakness are pending from BIOS firmware providers such as Dell and HP. Until these fixes are available and thoroughly tested, Intel recommends deactivating the VPro firmware so it is not accessible over the network.
Centralized management allows the business to immediately put in place a fix that will address the problem without impacting functionality for their users. The alternative is to wait for a BIOS patch from your hardware vendor. BIOS patches usually take a considerable amount of time to develop and test due to the the nature of BIOS.
Also, there is a high likelihood that a BIOS update will impact some set of your user community. By deactivating the VPro features, the impact to users is concentrated and isolated. This is great example of the power of centralized endpoint management and how it can be used to mitigate significant vulnerabilities, even when patches aren’t yet available from the manufacturers!"
Be safe out there! And be sure to check out our security solutions by clicking below.


