Exposure Management vs. Vulnerability Management: Which Delivers Real Risk Reduction?
Key Takeaways
- Exposure management is an evolving cybersecurity practice that focuses on comprehensive attack surface visibility, risk prioritization and risk appetite to maximize organizational security.
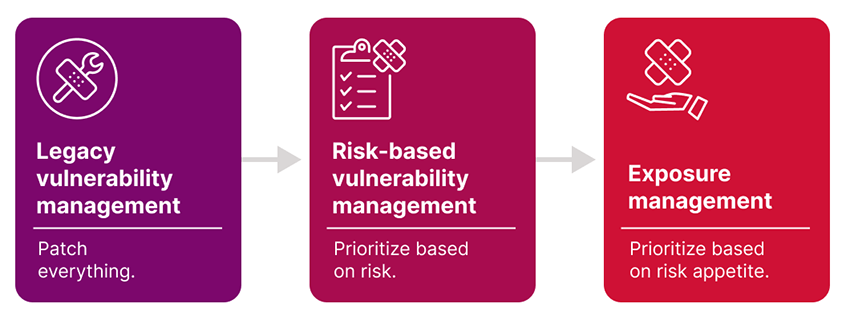
- Vulnerability management is a legacy approach geared towards remediating as many vulnerabilities as possible (not accounting for real-work risk, resources, etc.).
- While risk-based vulnerability management does factor in real-world threats, it falls short of exposure management’s holistic approach because it isn’t grounded in risk appetite.
- Exposure management covers more of your attack surface by securing newer types of assets (e.g., IoT devices, cloud infrastructures) and going beyond CVEs and CVSS.
Vulnerability management has served organizations and the cybersecurity industry for years. It is a capable practice that has helped companies defend their attack surface and prevent threat actors from exploiting vulnerabilities.
But technology and IT infrastructure have evolved. Vulnerability management no longer can meet the challenges that come with this evolution. Now, exposure management is here to provide an even more holistic approach to endpoint security that covers the areas vulnerability management falls short in.
Let’s dive into the distinctions so that you can decide how to protect your organization.
What is vulnerability management?
Vulnerability management is a cybersecurity practice that includes continuous and proactive identification, assessment, prioritization and remediation of vulnerabilities hackers can use to infiltrate your organization.
However, it’s important to note that there are two different types of vulnerability management:
|
Legacy vulnerability management |
Risk-based vulnerability management |
|
Involves attempting to remediate as many vulnerabilities as possible. This often results in substantial effort and unrealistic expectations for success while presenting a false sense of security. |
An evolved vulnerability management practice that accounts for risk in vulnerability prioritization. This allows organizations to patch the critical vulnerabilities that pose a real-world threat, protecting your organization from threat actors while also ensuring a strong security posture and effectively managing resources. |
A risk-based vulnerability management approach goes beyond legacy vulnerability management, providing your organization with the following benefits:
- Continuously monitors vulnerabilities for proactive security.
- Identifies actively exploited exposures.
- Enables effective remediation efforts.
- Reduces risk.
- Assists organizations with reaching compliance.
While risk-based vulnerability management covers a lot of bases, it still doesn’t offer the holistic approach to cybersecurity that organizations need to stay safe and secure. That’s where exposure management comes into the picture.
What is exposure management?
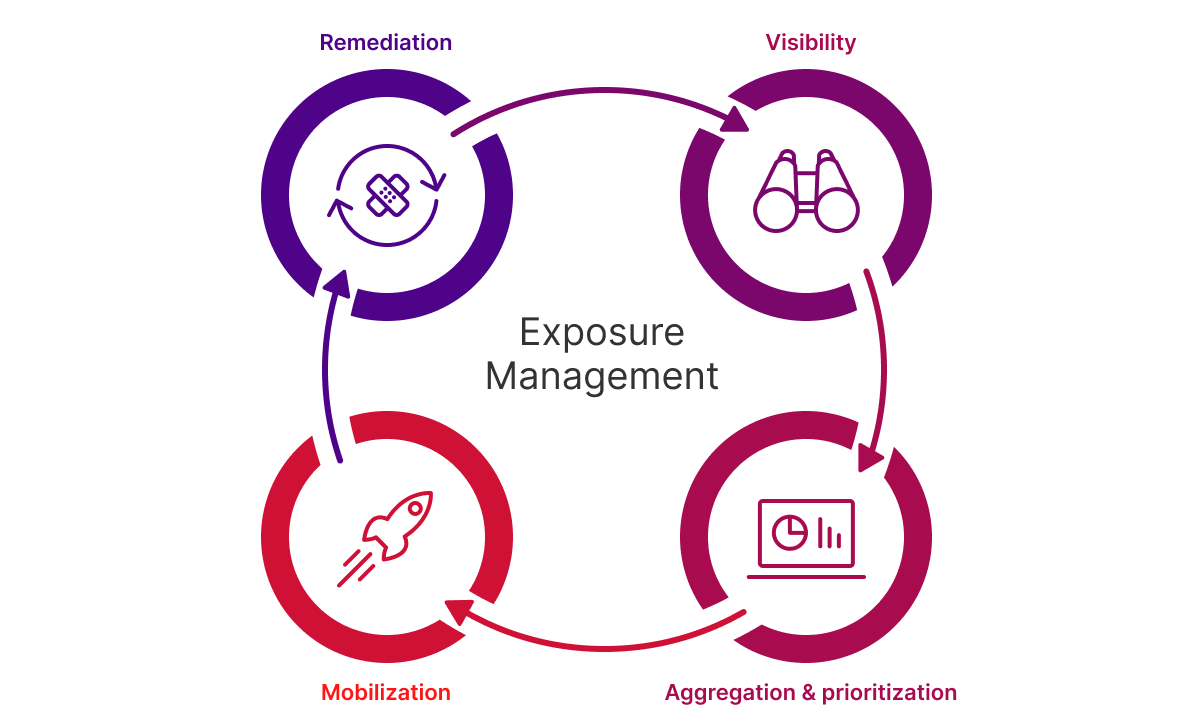
Exposure management is an evolving cybersecurity practice that provides comprehensive visibility across your entire attack surface. It allows IT and Security teams to identify exactly where your organization may be exposed while including risk-based prioritization, remediation and more. Exposure management focuses on maintaining an organization’s self-determined risk appetite. Therefore, it encompasses four stages:
Like risk-based vulnerability management, exposure management helps prioritize which vulnerabilities and exposures should be addressed first based on real-world risk, but it goes further by factoring in what is most relevant to your specific business. This cybersecurity approach ensures that the highest-risk exposures are remediated proactively, before they can be exploited by attackers.
Exposure management vs. vulnerability management: What’s the difference?
Exposure management represents the next evolution beyond traditional vulnerability management. While vulnerability management primarily focuses on identifying and addressing weaknesses in servers and endpoints, exposure management expands this scope by delivering complete visibility across the entire attack surface.
In terms of key differences, these include:
- Exposure management is designed for newer types of assets: Modern IT environments have grown increasingly complex, now including assets such as Software-as-a-Service (SaaS) applications, IoT devices, cloud infrastructure and more. Exposure management is designed to account for these newer kinds of assets, ensuring IT and security teams can identify risks wherever they exist in the organization. By doing so, exposure management provides a comprehensive understanding of all potential entry points. This empowers organizations to manage and reduce risk more effectively than ever before.
- Exposure management understands the reality and champions a risk appetite approach: Again, vulnerability management is centered around patching vulnerabilities. While risk-based vulnerability management provides risk prioritization and remediation orchestration, the practice doesn’t acknowledge the fact that it’s not realistic for an organization to patch every vulnerability. The term risk appetite is an organization’s self-determined measurement of how much risk it is willing to accept. This is a significantly more realistic approach that rallies the organization together to achieve shared KPIs to measure success consistently across teams.
- Exposure management goes beyond CVEs and CVSS: Vulnerability management focuses primarily on common vulnerabilities and exposures (CVEs). While CVEs are an important target for most organizations, they are not the only catalysts that threat actors can use to cause damage to your organization. Hackers can still leverage the following exposures (that vulnerability management doesn’t cover) to infiltrate your organization:
- Misconfigurations.
- Application security issues.
- IT system policies.
- Privileged access controls.
Tying it back to the holistic approach, exposure management covers all these modern assets. Furthermore, vulnerability management is heavily reliant on the Common Vulnerability Scoring System (CVSS) for remediation prioritization. While CVSS is a solid measurement for severity, it provides an effective risk-adjusted perspective.
Risk is an important factor to keep in mind since it includes whether a vulnerability has been exploited, if it has ties to ransomware/malware or is currently trending. Not factoring risk creates a false sense of urgency with CVSS, causing IT and security teams to waste time and resources on vulnerabilities that are not truly urgent.
How to safeguard your organization
Now that we have covered the differences between exposure management and vulnerability management, it’s time to leverage the advantages that exposure management provides. Learn how Ivanti’s exposure management portfolio can elevate your IT and security teams.
FAQ
What is vulnerability management?
Vulnerability management is a cybersecurity practice focused on identifying, assessing, prioritizing and remediating vulnerabilities that attackers could exploit. It traditionally aims to patch as many vulnerabilities as possible, but this approach often leads to unrealistic expectations and wasted resources.
What is exposure management?
Exposure management is an advanced cybersecurity practice that provides full visibility across the entire attack surface. It prioritizes remediation based on risk and an organization’s risk appetite – the level of risk the business is willing to accept. It includes four stages: visibility, aggregation and prioritization, mobilization and remediation.
How does exposure management differ from vulnerability management?
- Scope: Exposure management covers modern assets like IoT devices, SaaS apps and cloud infrastructure.
- Risk approach: Exposure management incorporates risk appetite, acknowledging that patching every vulnerability is unrealistic.
- Beyond CVEs: Exposure management addresses misconfigurations, policy gaps and privileged access issues – not just CVEs and CVSS scores.
Why is risk appetite important in exposure management?
Risk appetite defines how much risk an organization is willing to accept. By aligning security efforts with this threshold, exposure management ensures resources are focused on the most impactful exposures.

