The Five Ws (and H) of Exposure Management
Key Takeaways
-
Exposure management is a proactive cybersecurity practice that enables organizations to maintain their exposures at a level that aligns with their risk appetite.
-
Implementing exposure management involves widening the attack surface aperture, reframing remediation efforts and reprioritizing exposures based on risk.
-
Key best practices for exposure management include validating exposures through methods like penetration testing and breach simulation and building a bridge to the business side to ensure alignment with organizational priorities.
The Five Ws and H — who, what, when, where, why and how — have long been used as a checklist in journalism to make sure a story covers every piece of essential information. The same concept is employed here to make sure all the essential information about exposure management is covered in this post.
Read on for a better understanding of exposure management (the Five Ws) and actionable guidance for implementing it (the H).
Who
Who invented exposure management?
The term “exposure management” has been used in various contexts for decades, though it’s unknown when it was first used within the context of cybersecurity. That being said, exposure management is an evolution of vulnerability management, so it’s not an entirely new concept within the cybersecurity space but rather a reimagining of a preexisting practice.
Exposure management started gaining popularity in the cybersecurity space in 2022 as analyst firms began publishing research reports on the topic and vendors began releasing exposure management products and services.
Who benefits from exposure management?
Exposure management benefits a range of internal stakeholders — I recommend reading on if you fit any of the following profiles:
| Role | Relevant Responsibility | Benefit |
|---|---|---|
| Security architect | Develop secure systems and networks | Improved understanding of risk posed to systems and networks |
| Vulnerability risk management (VRM) | Identify exposures and prioritize for remediation | Improved efficiency and accuracy of prioritization process |
| SOC / security analyst | Detect and respond to cyber attacks | Lower volume of incidents requiring reactive response |
| IT operations | Remediate exposures prioritized by VRM | Lower volume of exposures requiring remediation |
| Development | Make code changes to resolve exposures in software | Lower volume of exposures requiring resolution |
| Chief information security officer (CISO) | Oversee infosec program that protects systems and data | Stronger security posture better protects systems and data |
| Chief information officer (CIO) | Own management, implementation and usability of IT | Less downtime leads to improved digital employee experience |
| C-suite | Ensure day-to-day operations align with long-term strategies | Better equipped to make decisions regarding risk |
| Board of directors | Protect interests of shareholders and stakeholders | Fewer attacks means less damage to reputation and revenue |
| Business unit (BU) leader | Lead a specific division towards its goals | Decreased downtime of BU’s critical systems and services |
| Public relations (PR) | Reverse negative communication and perception around a crisis | Fewer PR crises stemming from cyber attacks |
| Chief financial officer (CFO) / finance organization | Maintain the fiscal health of the organization | Less unanticipated costs for cyber attack response and recovery |
| Compliance team | Ensure adherence to regulations and avoidance of missteps that could harm the organization | Lower odds of violating regulations or experiencing other harm thanks to fewer breaches |
External stakeholders also benefit when exposure management results in improved security postures for organizations. For example, customers are at lower risk of having their personally identifiable information (PII) compromised in a data breach and shareholders are less likely to see stock prices dip due to a brand’s reputation being damaged by a cyber attack.
Who “owns” exposure management?
This may seem illogical, or even controversial, but it’s the C-suite that owns exposure management. While Security owns day-to-day exposure management operations, those operations are executed at the direction of the executive team — as noted above, they’re the ones determining the organization’s risk appetite. The numbers support this stance. 86% of security professionals we surveyed said that cybersecurity is a topic discussed at the board level.
Such a stance may have been blasphemous in the past, as most C-suite members lack the knowledge necessary to make cybersecurity decisions. But by focusing on exposure management, organizations can use quantifiable data to assess risks, reducing reliance on subjective judgment. This means that decisions regarding cybersecurity priorities and responses can be based on measurable risk factors, such as the likelihood of a threat and its potential impact.
Further, by linking cybersecurity operations directly to risk posture, exposure management offers a greater opportunity for aligning these operations with the overall business strategy. Under this approach, cybersecurity is no longer just a technical requirement but a strategic enabler that supports broader business objectives.
What
What is exposure management?
Exposure management is a proactive cybersecurity practice that enables organizations to maintain their exposures at a level that aligns with their risk appetite. It is, in essence, an evolution of vulnerability management that addresses the shortcomings of traditional vulnerability management practices.
Exposure management practices are commonly guided by continuous threat exposure management (CTEM) programs.
Refer to Ivanti’s Exposure Management glossary page for a more thorough answer to this question.
What is continuous threat exposure management (CTEM)?
Continuous threat exposure management — or CTEM — is defined in the 2023 Gartner® Implement a Continuous Threat Exposure Management (CTEM) Program report as follows:
“Continuous Threat Exposure Management (CTEM) program is a set of processes and capabilities that allow enterprises to continually and consistently evaluate the accessibility, exposure and exploitability of an enterprise’s digital and physical assets.
At any stage of maturity, a CTEM cycle must include five steps to be completed: scoping, discovery, prioritization, validation and mobilization.”1
What are the components of exposure management?
In its current form, exposure management effectively combines capabilities from these existing categories:
- Attack surface management (ASM), e.g., external attack surface management (EASM) and cyber asset attack surface management (CAASM).
- Risk-based vulnerability management (RBVM).
- Validation, e.g., breach and attack simulation (BAS), continuous automated red teaming (CART) and penetration testing as a service (PTaaS).
Expect to see purpose-built exposure management products and platforms as the exposure management market matures.
What is risk appetite?
Risk appetite is the level of cyber risk an organization is prepared to accept in pursuit of its business objectives, such as increased agility, innovation or performance. To determine its risk appetite, an organization must weigh the cost of maintaining a certain security posture against the benefit of doing so. Setting risk appetite is a business decision, though one that must include input from Security.
Refer to Understanding Risk Appetite – a Critical Component of Exposure Management for an in-depth description of risk appetite.
Where
Where should exposure management be implemented?
Exposure management practices should be implemented at all organizations that rely on technology that’s accessible from the internet or other external pathways.
Exposure management is especially important for organizations that are beholden to laws and/or other regulations regarding the safe handling of personal data. Examples include the California Consumer Privacy Act (CCPA) and the General Data Protection Regulation (GDPR).
Organizations likely to have lots of unknown devices connecting to the network and other unknown internet-facing assets in their environment are also optimal candidates for exposure management. Unknown assets often proliferate as a result of bring your own device (BYOD) policies and mergers and acquisitions.
When
When should I implement exposure management?
According to a Gartner press release, “By 2026, Gartner predicts that organizations prioritizing their security investments based on a CTEM program will realize a two-thirds reduction in breaches.”2 We believe that’s a compelling reason to begin implementing exposure management as soon as possible. It’s also good news at a time when organizations’ attack surfaces are rapidly expanding, putting them at higher risk of attack.
More good news: any organization practicing vulnerability management has already laid the foundation upon which they can build an exposure management practice. Read on for actionable advice on how to do so.
Why
Why implement exposure management?
Many organizations have an incomplete understanding of their cyber risk due to limited views of the assets and exposures in their environments. Lots of effort is exerted in attempts to lower risk by remediating exposures, but the ROI on that effort is often low due to shortcomings associated with traditional vulnerability management methods.
Such organizations thus remain at elevated risk of experiencing cyber attacks that take advantage of un-remediated exposures and can negatively impact their operations, image and revenue. Exposure management solves this problem by empowering those organizations to maintain their exposures in alignment with their risk appetite.
The following is an overview of the shortcomings of traditional vulnerability management that exposure management addresses:
Shortcoming #1: Organizations look only at a narrow sliver of their continuously expanding attack surfaces.
Many organizations only closely monitor and manage their traditional perimeter — endpoints and servers — from a cybersecurity standpoint.
Why it’s a problem: Full attack surface visibility is needed to properly protect against all potential threats.
Modern attack surfaces have expanded beyond the traditional perimeter to include mobile devices, applications, websites, certificates/domains and more. Each of these components introduces added risk to an organization that must be accounted for.
Shortcoming #2: The number of cybersecurity exposures organizations face continues to grow at an unmanageable rate.
There are hundreds of thousands of existing Common Vulnerabilities and Exposures (CVEs) and dozens — sometimes hundreds — more are published to the National Vulnerability Database (NVD) every day. And while CVEs are often the only type of exposure organizations account for, they face many others, such as misconfiguration of assets and security controls.
Why it’s a problem: Remediating all exposures is operationally infeasible, leaving organizations stuck in reactive mode.
Organizations are overwhelmed by the constant onslaught of exposures turning up in their environments. They can’t fix every exposure as that would require critical systems to be offline far too often — not to mention many exposures don’t have known fixes.
This forces them into firefighting mode, always trying to unbury themselves from endless exposures or overcome ongoing security incidents instead of working proactively to improve their security posture.
Shortcoming #3: Remediation activities are prioritized based strictly on the severity of vulnerabilities.
The Common Vulnerability Scoring System (CVSS) v3.1 is among the most popular methods for prioritizing vulnerabilities for remediation. CVSS assigns vulnerabilities with scores from zero to 10 based on their severity — zero being the least critical and 10 being the most.
Unfortunately, those scores don't account for real-world threat context — meaning organizations employing CVSS are misguided if their intent in doing so is to reduce risk.
Why it’s a problem: Remediation decisions are based on the makeup of vulnerabilities instead of a given organization’s risk appetite and the potential impact a given vulnerability may pose to their business.
Organizations that use CVSS are basing decisions on vulnerabilities’ characteristics without accounting for their own. For starters, since CVSS scores don’t accurately reflect risk, organizations can’t use CVSS to determine if a given vulnerability exceeds their individual risk appetite.
Further, CVSS doesn’t enable organizations to determine how a vulnerability might impact their business — certainly a crucial consideration when determining whether that vulnerability needs to be remediated.
How
How do I implement exposure management?
This bears repeating one more time: exposure management is an evolution of vulnerability management. Most organizations thus already have the foundation for its exposure management practice in place.
But how do you advance from vulnerability management to exposure management? Here are six best practices to guide the process:
Best practice #1: Widen your attack surface aperture
Evolving to exposure management requires widening your attack surface aperture to include non-patchable attack surfaces. While you’ll always need to account for traditional devices and applications, nowadays, you also need to account for all systems, applications and subscriptions, including those not owned by IT or even managed by the business.
Examples include everything from third-party applications and services — such as SaaS, supply chain dependencies and online code repositories — to corporate social media accounts and leaked data. To gain this visibility, you’ll need to implement digital risk protection services (DRPS) and external attack surface management (EASM) solutions in addition to any existing cybersecurity asset management (CSAM) tools.
Best practice #2: Reframe remediation
If you expand your exposure management program to include non-patchable attack surfaces, you’ll also need to expand it to include means for managing your exposure through ways other than patching.
There are many routes to resolution for threat exposures, ranging from accepting and managing the risk by increasing monitoring, through to mitigation and resolutions that, in addition to patching, may mean implementing a policy change or redeveloping an application.
Remember, there's often more than one fix to an issue, and your team will often need to collaborate closely with other teams to implement those fixes, including infrastructure and operations teams and enterprise architecture functions. In some cases, your team may need to acquire new skills and understanding to execute fixes that fall under Security’s umbrella.
Best practice #3: Reprioritize
As mentioned under “Why implement exposure management?” above, using CVSS to prioritize exposures for remediation omits risk from the prioritization process. That can be remedied through the use of risk-based vulnerability management (RBVM) solutions.
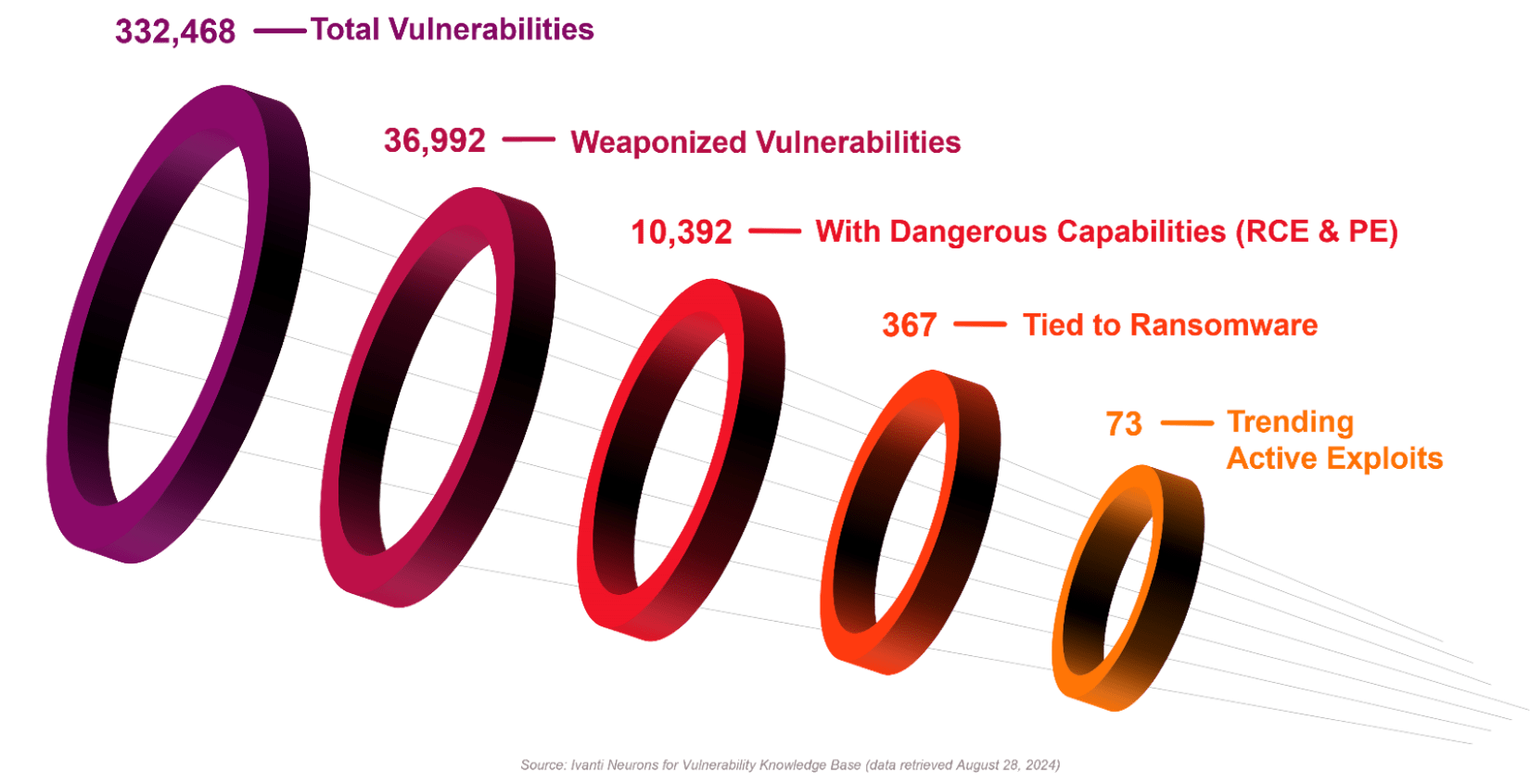
Here’s how such solutions improve exposure management, using the graphic above as a reference:
- There are 330,000+ known vulnerabilities.
- Fortunately, you don’t need to remediate every vulnerability in your environment. The number that are tied to ransomware is low, and even less are trending/active exploits.
- RBVM solutions provide risk-based scoring and views to help you focus remediation efforts on that small number of vulnerabilities that pose a significant risk.
Ultimately, a risk-based approach ensures you don’t waste time and effort mitigating or remediating any of the hundreds of thousands of exposures that pose no real danger to your organization, and that the effort you do expend actually goes toward improving your security posture.
Best practice #4: Build a bridge to the business side
With traditional vulnerability management, the “business side” typically only learns a patch is coming when they receive a notification telling them their PC needs to restart to finish installing updates — such is not the case with exposure management.
For starters, their input is required to determine the business impact of exposures and your organization’s risk appetite. You’ll need to continually work with the revenue-generating functions of the organization to determine what systems and solutions have a high impact on their priorities so that exposures that threaten those systems and solutions can be prioritized accordingly.
This is the type of work that earns Security a seat at the business table — work that shows Security exists to enable the business. Of course, teams on the business side may not be thrilled with the prospect of taking on extra work for something that has never been their responsibility, but there are ways to earn their buy-in:
- CISOs need to lead the outreach effort — their position within the organization will make it easier for them to open the necessary doors.
- Once you’re in the door, work with senior leadership to develop metrics that will enable them to make effective exposure management decisions without having to be security specialists.
- Ensure you keep all the departments you interact with informed on the various options that exist for resolving issues that may impact them. You may need to put in extra time here to shed Security’s reputation for being overly restrictive.
- Make it clear to them that the business will simply have to accept large amounts of unknown and unquantified risk if a poorly governed exposure management program fails to accurately scope, discover, prioritize and validate issues, thereby leading to a lack of visibility into threat exposure.
Best practice #5: Validate, validate, validate
Traditional vulnerability management is guided by prioritization, while exposure management couples prioritization with validation. Validation is necessary since prioritization alone leaves a large volume of issues to resolve.
In the context of exposure management, validation involves:
- Assessing how potential attackers can exploit an identified exposure.
- Estimating the highest potential impact of potential attack paths.
- Identifying how monitoring and control systems might react in the event of an attack.
Validation can be conducted via a mixture of manual and technological methods, including:
- Penetration testing conducted by automated tools, internal teams or contract pen testing as a service (PTaaS).
- Red team exercises.
- Breach and attack simulation (BAS).
- Attack path analysis.
Best practice #6: Crawl, walk, run
Last but not least, the final best practice for evolving to exposure management is: don’t attempt to do it overnight. Use your vulnerability management practice as your starting point and expand from there by adopting the other best practices covered here as your bandwidth and budget allow.
- Gartner. D’Hoinne, J., Schneider, M., Shoard, P. (2022, July 21). Implement a Continuous Threat Exposure Management (CTEM) Program. https://www.gartner.com/document/4016760.
- Gartner Press Release. Gartner Identifies the Top Cybersecurity Trends for 2024. (2024, February 22). https://www.gartner.com/en/newsroom/press-releases/2024-02-22-gartner-identifies-top-cybersecurity-trends-for-2024.
GARTNER is a registered trademark and service mark of Gartner, Inc. and/or its affiliates in the U.S. and internationally and is used herein with permission. All rights reserved.
FAQs
What is exposure management?
Exposure management is a proactive cybersecurity practice that enables organizations to maintain their exposures at a level that aligns with their risk appetite. It’s an evolution of vulnerability management that addresses the shortcomings of traditional vulnerability management practices.
What is risk appetite?
Risk appetite is the level and type of risk an organization is willing to accept in pursuit of its objectives. It acts as a guide for decision-making, helping organizations balance potential opportunities and threats.
Does Ivanti sell exposure management software?
Yes, Ivanti’s products for exposure management include Ivanti Neurons for Risk-Based Vulnerability Management, Ivanti Neurons for External Attack Surface Management, Ivanti Neurons for Discovery, Ivanti Neurons for Application Security Posture Management and Ivanti Neurons for Patch Management.

