Bullet-Proof Application Access Control
Key Takeaways
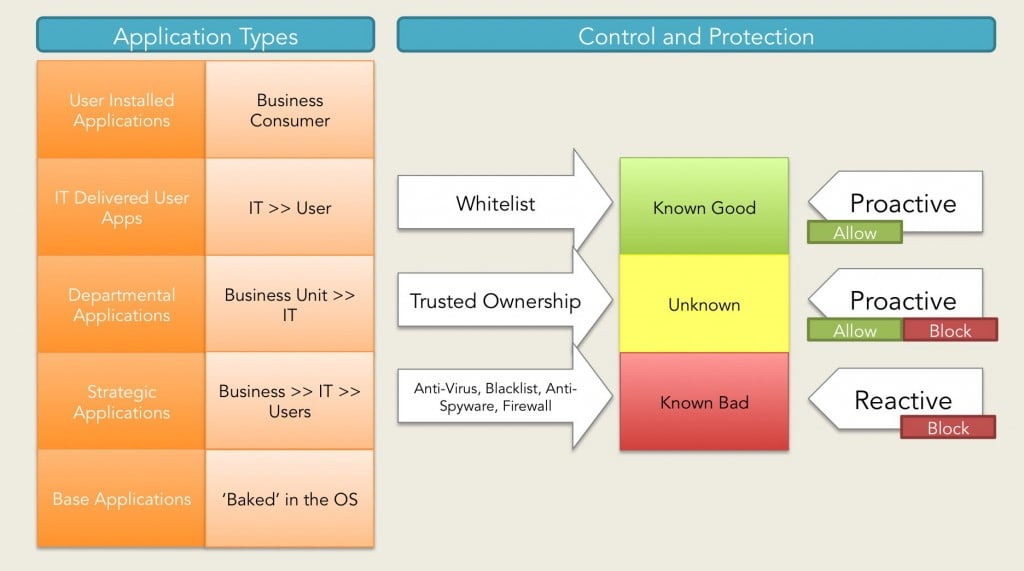
- Application entitlements can be defined per user, location, device, IP, time, and other criteria, and kernel‑level filtering blocks any execution request not explicitly allowed.
- Trusted Ownership automatically permits only applications installed by administrators and blocks all user‑introduced or unknown code, eliminating the need for complex scripts or maintained whitelist lists.
- Additional validation options include SHA‑1 digital signature checking and metadata criteria such as product name, version, and vendor, plus the ability to set privileges, resource limits, and personalization once an application is approved.
*This post originally appeared on the AppSense blog prior to the rebrand in January 2017, when AppSense, LANDESK, Shavlik, Wavelink, and HEAT Software merged under the new name Ivanti.

Regardless of how or where users access their desktops, IT teams need to both deliver the applications that users need to be productive and prevent the introduction of unauthorized applications. Introduction of unauthorized executable code not only impacts security but reduces desktop stability, breaches licensing compliance, causes downtime and increases desktop management costs.
Unfortunately, controlling application access can be difficult and costly despite it’s importance in desktop management. For many organizations, application access is managed by complex scripts and high-maintenance lists, which can be time consuming, inflexible and circumvented by savvy users. This method is also expensive, both in time and money, to implement and maintain.
Ok, let’s also talk malware. When we consider most (new) malware is unknown code, how do you protect yourself? You don’t know what you don’t know, and traditional anti-virus/blacklisting solutions don’t either, only protecting against malware code that is a match for a known threat. This makes it easy for the latest malware to bypass your defense with a new piece of code not listed in the definition library.
Whitelisting is another alternative, and is certainly a more preventive approach, allowing only pre-authorized 'known good' applications to run, but it can be tricked by users and is tedious to maintain for an entire organization.
Simple, Secure Control with AppSense Application Manager
With AppSense Application Manager, IT teams are in full control. Application access entitlements can be defined on a per-user basis based on factors such as user, location, device name, IP address, firewall settings and even time of day - providing complete control over what can be executed, from where, and when.
AppSense Application Manager is unique in that it focuses on only allowing known-good files to execute and by default blocks all user-introduced and unknown code. Using secure, kernel-level filter drivers and Microsoft NTFS security policies, AppSense Application Manager intercepts all execution requests and blocks any unwanted applications. Application entitlement is based on the ownership of the application, with default ownership being a domain administrator. By using this method, current application access policy is immediately enforced ‘out of the box’ without the need for scripting or list management. This is called Trusted Ownership™. In addition to executable files, AppSense Application Manager also manages entitlement to application content such as ActiveX controls, VBscripts, batch files, MSI packages and registry configuration files.
In essence, with Trusted Ownership, only trusted applications installed by administrators are allowed to execute, while any user-introduced applications and unknown code is automatically prevented from launching by default.
Security Integrity with Digital Signatures
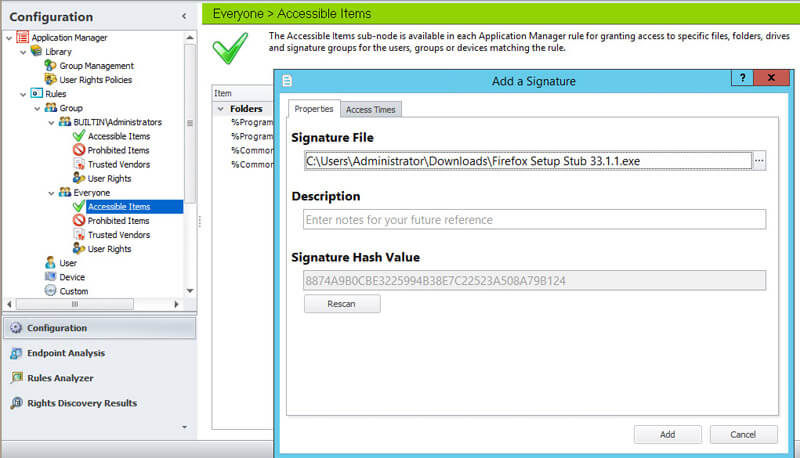
IT teams can add additional controls to our unique Trusted Ownership capability and ensure only trusted versions of applications can be executed by utilizing additional whitelist and blacklist controls whereby approval must be achieved based on a SHA-1 digital signature, a.k.a Cryptographic Hash Function (think electronic fingerprints), being applied to the specified file/application.
Digital signature checking gives administrators peace of mind, ensuring the applications and files installed on a system remain unaltered, maintaining system integrity and lowering maintenance costs. Digital signature checking is seen as the ultimate security method as it provides a powerful way of identifying an individual file. If one bit of a file is changed then the digital signatures will reflect the change and will not match.
When an application attempts to launch, we check the SHA-1 signature to determine if the file is legitimate and comparable to the signature defined in our configuration (see below). This ensures only specific versions of the authorized application are allowed to run, and prevents users from renaming a prohibited application to that of an authorized application on the whitelist. By providing SHA-1 support as an additional option for file checking, we follow our AppSense theme of offering the most complete and comprehensive User Environment Management solution.
AppSense SHA-1 Support Alert: While still secure, the somewhat old-aged SHA-1 cryptographic hash function produces a 160-bit hash value. In comparison, SHA-2 includes significant improvements from its predecessor, SHA-1. The SHA-2 family consists of six hash functions with hash values that are 224-bits, 256-bits, 384-bits or 512-bits compared to the 160-bit hash value in SHA-1. So, as you can see the SHA-2 function is far superior than SHA-1, and as such, keep an eye open for SHA-2 support in the next feature release of Application Manager (8.9)
Not just SHA-1, what about MetaData?
To further improve the granular options that govern whether an application can run or not, if it requires admin rights elevating or dropping and if it can connect to network locations, additional options based on the MetaData of a file can be evaluated to check against stated criteria to determine if the file or application can be run, elevated or allowed to access network resources.
We offer both SHA-1 and MetaData support to our customers. We added support for checking MetaData based on customer feedback around 18 months ago, and today it’s enormously popular.
The following MetaData items can be used as a qualification rule before a selected file or application can be run, elevated or allowed to access certain network resources:
- Product Name
- Vendor
- Company Name
- File Description
- File Version (minimum and maximum)
- Product Version (minimum and maximum)
Essentially we provide a wide range of options for blocking/allowing executables, balancing the trade off between IT ease of configuration & maintenance and extreme security control.
In Addition
Don’t forget, AppSense does much more than just control when and where applications can be executed - once an application is authorized to launch, AppSense can then configure the Windows Privileges for that application, assign configuration policies, assign predefined amounts of CPU and memory resources and apply unique personalization settings to the application.