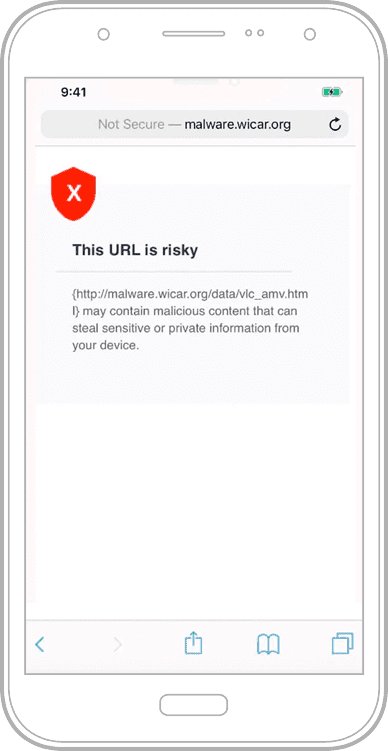
In fact, they cleverly exploit people's joyful mood for their own purposes. Mobile phishing attacks in particular are tricky and promising. And they are increasingly targeting employees who use their cell phones for both personal and professional purposes. Fraudulent links in messaging apps and social media or manipulated QR codes lure users to fake target pages. The targeted prey: your company data.
The good news is that Ivanti can instantly protect 100% of your remote employees from mobile phishing attacks.