February 2023 Patch Tuesday
Microsoft updates
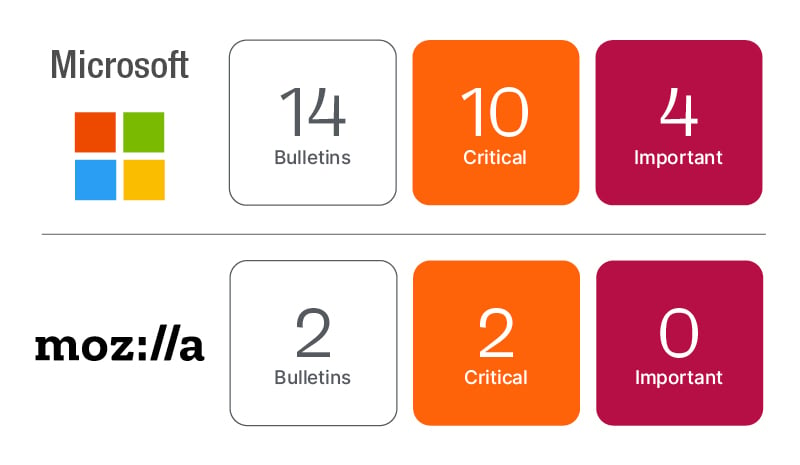
February 2023 Patch Tuesday includes fixes for 76 CVEs from Microsoft affecting Microsoft Windows, .NET Framework, Microsoft Office, SQL Server, Exchange Server, several Azure services, HoloLens and more. Nine CVEs are rated as Critical, 67 as Important and three CVEs have known exploits in the wild. The three zero-day vulnerabilities are all rated as Important and have CVSS ratings of 7.8 or less. Organizations are urged to expand their prioritization beyond just vendor severity and CVSS score alone, as many exploited vulnerabilities will be less than Critical or CVSS 8.0, which emphasizes the urgent need to utilize risk-based prioritization methods in your vulnerability management program.
Microsoft resolved a Remote Code Execution vulnerability in Windows Graphics Component (CVE-2023-21823), which has been exploited in the wild. The CVE was rated as Important and affects Windows 10 and Server 2008 and later Windows editions. The vulnerability also affects Microsoft Office for iOS, Android and Universal. If exploited, the vulnerability in the Windows OS could allow the attacker to gain SYSTSEM privileges. For the apps, the exploit could lead to Remote Code Execution. Windows customers are urged to update to the latest OS version. For the app updates, Microsoft included additional notes regarding how to update through the Microsoft Store or Play Store.
Microsoft resolved a Security Feature Bypass in Microsoft Publisher (CVE-2023-21715). The CVE was rated as Important and affects Microsoft 365 Apps for Enterprise and has been exploited in the wild. Microsoft noted that, “The attack itself is carried out locally by a user with authentication to the targeted system. An authenticated attacker could exploit the vulnerability by convincing a victim, through social engineering, to download and open a specially crafted file from a website which could lead to a local attack on the victim computer.” The exploit can bypass Office macro policies used to block untrusted or malicious files.
Microsoft resolved an Elevation of Privilege vulnerability in Windows Common Log File System Driver (CVE-2023-23376), which has been exploited in the wild. The CVE was rated as Important and affects Windows 10 and Server 2008 and later Windows editions. If exploited, the attacker could gain SYSTEM privileges. A privilege escalation vulnerability like this would be used in combination with other vulnerabilities in an attack chain.
The Microsoft SQL Server update resolves six CVEs, one of which is rated Critical. This is the most security fixes released in a single update for SQL Server in many years.
The Microsoft Exchange Server update resolves four CVEs, all of which are rated as Important. No public disclosures or known exploits have been included in this update yet, but Exchange has been targeted by sophisticated threat actors in the past couple of years. All four of these are Remote Code Execution vulnerabilities. They shouldn't be left too long.
Third-party update round-up
Mozilla has released updates for Firefox and Firefox ESR, resolving 19 and 14 CVEs, respectively.
Google Chrome released updates for Windows and MacOS editions on February 7th resolving 10 CVEs.
Microsoft Edge (Chromium) released an update on February 9th resolving 11 CVEs.
Apple released updates for MacOS BigSur (8 CVEs), Monterey (18 CVEs), and Safari (3 CVEs) in late January.
Oracle’s quarterly CPU released on January 17th and included an update for Java (4 CVEs). This event triggers the release of many Java frameworks in quick succession. There have been updates for Corretto, Azul Zulu, Node.JS and other Java frameworks since the CPU release.