October Patch Tuesday 2017
Key Takeaways
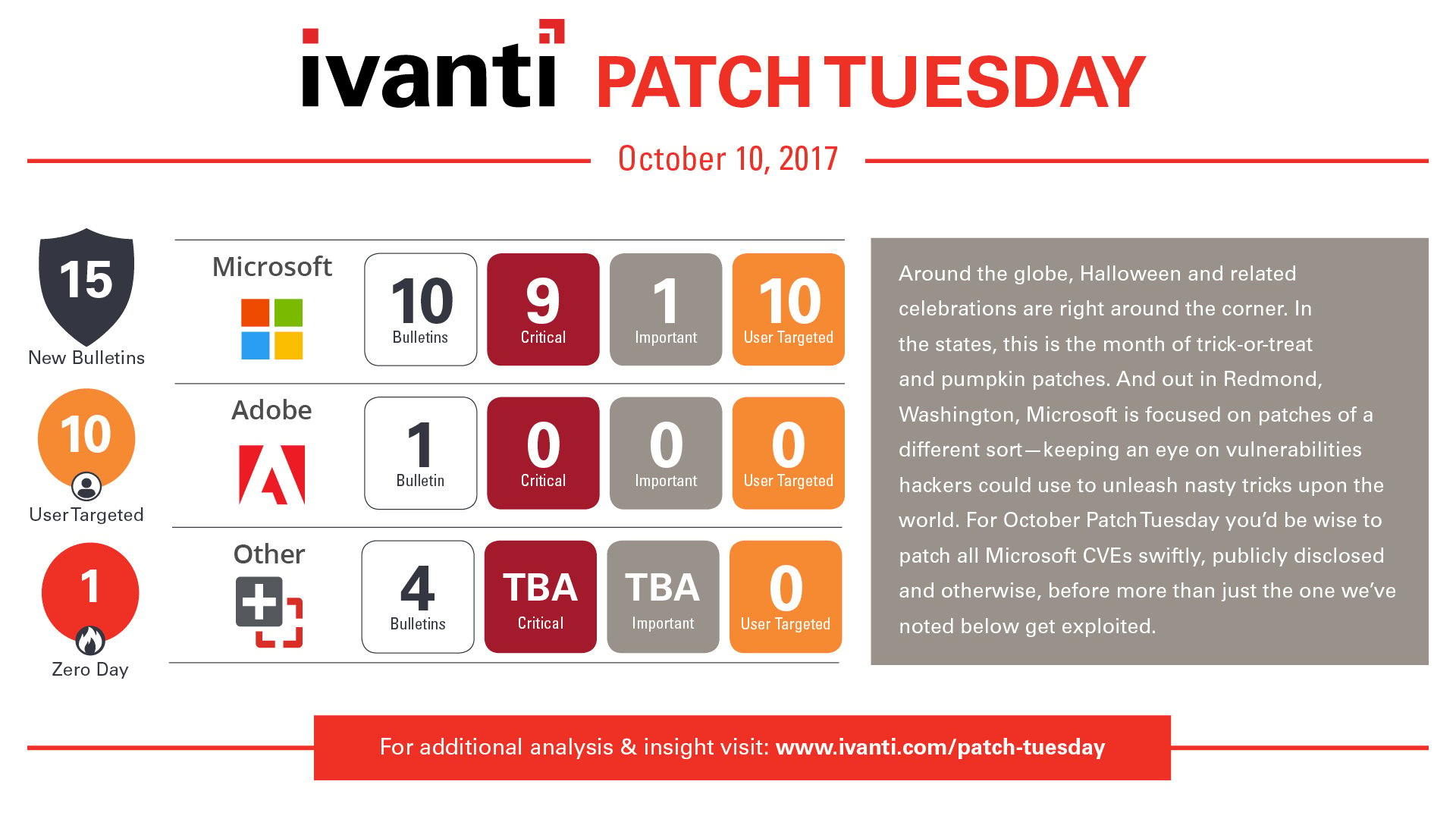
- Microsoft released 62 patches, nine rated Critical and one Important. The update stack included a publicly disclosed WSL DoS bug and two Office vulnerabilities, one exploited in the wild.
- This is the last month Microsoft will support Windows 10 version 1511, so organizations should upgrade to the 1607 Anniversary Update or newer.
- Oracle’s quarterly CPU will arrive on October 17 with critical Java updates. Adobe Flash released a feature only update with no security fixes.
Halloween might be just around the corner, but this Patch Tuesday wasn’t scary and we didn’t see Microsoft play any tricks. In fact, we were given a special treat!
Microsoft resolved a total of 62 unique vulnerabilities, down nearly 20% from the 76 unique vulnerabilities resolved last month. There were 10 bulletins, nine of which were rated Critical and one rated Important.
Be sure to check out all of Ivanti’s patch products:
Patch for SCCM
Patch for Windows
Patch for Linux, UNIX, Mac
Patch for Endpoint Manager
The resolved vulnerabilities included two public disclosures and one vulnerability that has been both exploited in the wild and publicly disclosed.
Affected Microsoft Products:
- Internet Explorer
- Microsoft Edge
- Microsoft Windows
- Microsoft Office and Microsoft Office Services and Web Apps
- Skype for Business and Lync
- Microsoft SharePoint Server
We’ve been asked quite often if the Linux support that Microsoft is adding into their operating system is going to introduce additional vulnerabilities. The simple answer is yes, since any time new functionality is added, there is always opportunity for new vulnerabilities to be introduced. We’ve seen them pop up from time to time, and this month we have one that is publicly disclosed.
• CVE-2017-8703 | Windows Subsystem for Linux Denial of Service Vulnerability (Publicly Disclosed) – An attacker can execute a specially crafted application to affect an object in memory allowing them to cause the system to become unresponsive.
It’s interesting Microsoft chose to rate the severity of their Office updates this month as Important when there was both a publicly disclosed and exploited vulnerability resolved.
• CVE-2017-11777 | Microsoft Office SharePoint XSS Vulnerability (Publicly Disclosed) – An attacker can send a specially crafted request to an affected SharePoint server. The attacker would have the same security context as the current user allowing them to read data they should not have access to, use the victim’s identity to take actions on the SharePoint site on behalf of the user, and inject malicious content in the browser of the user.
• CVE-2017-11826 | Microsoft Office Memory Corruption Vulnerability (Publicly Disclosed\Exploited) – An attacker could exploit this vulnerability by sending a specially crafted file to the user and convincing them to open it. An attacker could also host a website containing specially crafted files designed to exploit the vulnerability. If exploited, the attacker would have the same context as the user. In this case, less privileges would mitigate the impact of an exploited system.
This is the last month that Microsoft will release security updates for Windows 10 1511. It is time to move to the 1607 Anniversary Update or all the way to 1703 Creators update if you want to have the latest version. If you have any questions, consult their help documentation.
Oracle will release its quarterly CPU next week on Tuesday, October 17, so expect critical updates for Java JRE and JDK as well as other Oracle products.
Special Treat
I mentioned we were given a special treat this month. For the first time in ages, Adobe Flash does not include any security fixes. That’s right! A priority three, feature bug fix-only release for Adobe Flash, and no required update from Microsoft!
In the News
The Equifax security breach and associated congressional hearing dominated the security news for most of September. The company testimony showed a breakdown in both the personnel and technology aspects of their patch program. Although the vulnerability was known for some time, the patch process was delayed due to employee initiative. And to add insult to injury, the tools they were using showed the systems as patched when they weren’t.
As I mentioned in my forecast blog, it may be time we all do a quick review of our patch policy and implemented processes to make sure we are minimizing our exposure and risk.
The complexity of attacks continues to rise, and the EternalBlue v1SMB vulnerability continues to be a an entry point. Recent announcements include the introduction of a banking system Trojan in Europe and Japan, and a complex hotel reservation system attack in Europe and the Middle East. Both attacks used a complex set of tools to gain access to the target systems and attempted to grab user credentials. This is just another example of why we need to remain vigilant and make sure we are keeping up with the latest patches to close these avenues of vulnerability.
For deeper analysis on the October Patch Tuesday release, join us live for the October Ivanti Patch Tuesday Webinar!