June Patch Tuesday 2022
Key Takeaways
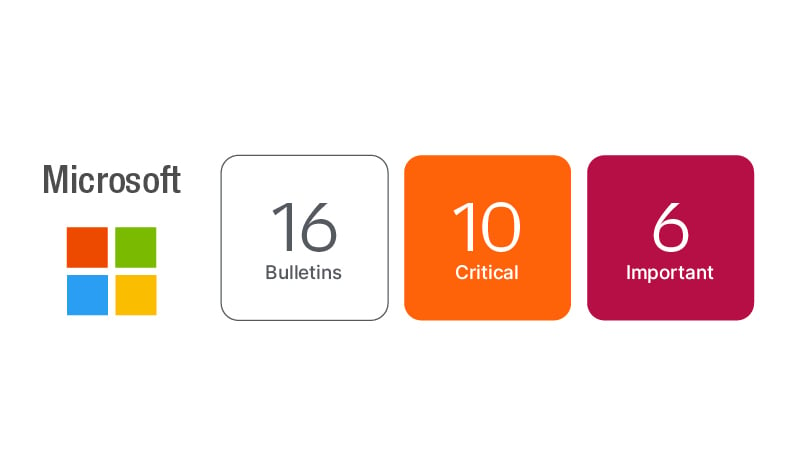
- Microsoft’s June Patch Tuesday delivered updates for 61 vulnerabilities, including three new Critical CVEs. CVE‑2022‑30136, CVE‑2022‑30139 and CVE‑2022‑30163 affect Windows Server components and should be patched immediately.
- The Follina vulnerability (CVE‑2022‑30190) in the Microsoft Support Diagnostic Tool, which enables remote code execution via Office document previews, was patched for Windows 7 through Windows 11. Organizations should confirm deployment to block active exploitation.
- Microsoft reissued the Phase 2 update for the DCOM Server Security Feature Bypass (CVE‑2021‑26414), which now enables the RPC_C_AUTHN_LEVEL_PKT_INTEGRITY registry key by default. The final phase is scheduled for the March 2023 Patch Tuesday.
June Patch Tuesday is here, and we’ve now reached the midway point of 2022. It’s been and up and down six months so far with a wide swing in the number of vulnerabilities Microsoft has been addressing each month. We started off with 85 CVEs addressed in Windows 10 in January, dropped to a low of 21 CVEs in February, and are back up to 97 CVEs addressed in May. This month, we saw 33 vulnerabilities fixed in Windows 10 and its associated servers. The hot discussion topic this past month was CVE-2022-30190, also known as the Follina vulnerability, which was fixed today with updates from Windows 7 through Windows 11. The second phase of the DCOM server security update was also implemented this month. Don’t forget to upgrade Windows 10 1909 and others that reached end-of-life last month and have a plan in place if you still need Internet Explorer 11 for any of your applications. Despite a standard set of updates from Microsoft, there is plenty of additional work to keep us busy this month.
Microsoft Patch Tuesday update
Microsoft has released their updates resolving 61 unique vulnerabilities, 5 of which are re-issued vulnerabilities from April and May. Only 3 of the new CVEs are rated as Critical. CVE-2022-30190, surprisingly rated as Important, is the only one reported known to be known exploited and publicly disclosed this month. Updates this month affect the Windows Operating System, O365 applications, Exchange Server, .Net, Visual Studio, RDP, Hyper-V and a rare security update to SQL Server as well.
The most important of the 3 new Critical updates is for CVE-2022-30136, a network file system remote code execution vulnerability impacting Windows Server 2012, Server 2016, and Server 2019. It has a CVSS score of 9.8 due to its Network attack vector and Low complexity to exploit. In addition to updates which were released, Microsoft has provided detailed mitigation options in the CVE KB. The other two Critical CVEs – CVE-2022-30139 and CVE-30163 are also remote code execution vulnerabilities in Lightweight Directory Access Protocol (LDAP) and Hyper-V respectively; these are more difficult to exploit with lower CVSS scores. All three should be given priority depending upon the level of risk they impart on your systems.
Microsoft has also re-issued an update from June 2021 to CVE-2021-26414 DCOM Server Security Feature Bypass. This is phase 2 of 3 in the process of improving overall server security. With the month’s release, the registry key RPC_C_AUTHN_LEVEL_PKT_INTEGRITY on DCOM servers is now enabled by default. Administrators can still manually disable it if needed for their environment. The final phase will occur with the March 2023 Patch Tuesday update where it will be permanently enabled. Complete details surrounding DCOM can be found in KB 5004442—Manage changes for Windows DCOM Server Security Feature Bypass (CVE-2021-26414).
Take note that Microsoft also released Advisory 220002 Microsoft Guidance on Intel Processor MMIO Stale Data Vulnerabilities which describes several CVEs addressed this month as part of a set of Intel updates.
The Follina vulnerability
The hot topic this month has been around CVE-2022-30190, also known as the Follina vulnerability. This vulnerability in the Microsoft Windows Support Diagnostic Tool (MSDT) allows for remote code execution. This diagnostic tool sends troubleshooting information back to Microsoft when you have a problem on your local machine. The vulnerability is exploited via malicious code included in a Word document, and what makes it particularly troublesome is the user doesn’t even have to open the document directly. Any Office program that provides a preview mode will trigger the exploit. This vulnerability has been under attack for several months. This vulnerability fix must have been a late addition this month, because although it shows up in the Vulnerabilities list of the Security Guide, it was not shown in the breakdown of CVEs for each patch.
EOL and EOS
Internet Explorer is officially (almost) coming to an end tomorrow - June 15th. Internet Explorer 11 (IE 11) is the last of the line and will no longer be supported in Teams, Office 365, and most versions of the Windows operating system. If you still need IE 11 for critical business functionality, Microsoft recommends using IE mode in the Edge browser. This functionality is scheduled to be supported in Edge until 2029. The IE 11 desktop application will continue to get security updates in Windows 8.1, Windows 7 (ESU), and Windows Server LTSC until they reach their respective EOL dates. This Microsoft FAQ provide the best details on the end of this longtime favorite application.
Remember, you won’t see any updates for Windows 10 1909 Enterprise and Education, 20H2 Professional, or Windows Server 20H2 this month. May contained the last Patch Tuesday updates for those operating systems, so you should be moving to an updated and supported version as soon as possible to minimize your exposure. Under the Microsoft SaaS model, the next Windows 10 EOLs come in December so you have a little breathing room until the next round.