July Patch Tuesday 2022
Key Takeaways
- Microsoft’s July cumulative update aims to fix the CSRSS privilege escalation zero‑day. It also includes four print spooler patches that could impact printing services.
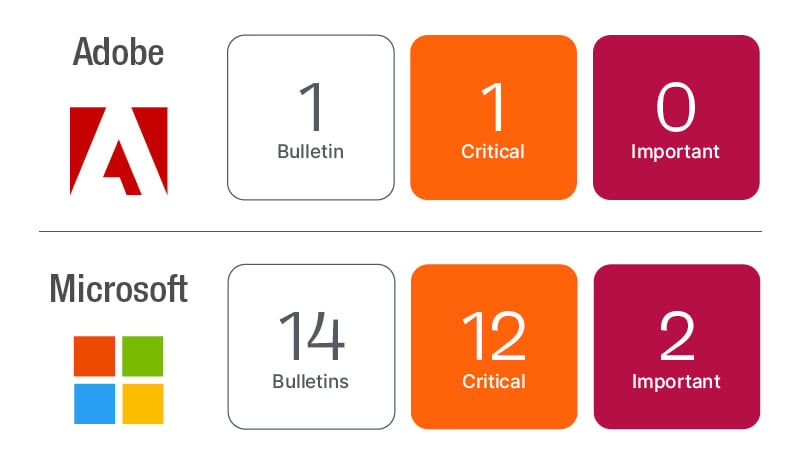
- Chrome, Edge, and other Chromium browsers need the latest update to address Google’s zero‑day in the browser engine. Adobe Acrobat and Reader updates resolve fifteen critical vulnerabilities.
- Internet Explorer 11 is now end of life. Any remaining installations should be documented and removed, and Edge’s IE mode should be used only for required legacy compatibility.
The July Patch Tuesday has more cleanup than net new activities as far as critical updates are concerned. July 4th saw fireworks across the U.S. for Independence Day and a Zero Day release from Google to resolve a buffer overflow vulnerability (CVE-2022-2294), which also means an update for any Chromium-based browsers such as Microsoft Edge. Microsoft has their standard lineup of updates for the Windows OS, O365, Microsoft Edge (Chromium-based), and Skype for Business. Adobe released updates for Acrobat, Acrobat Reader, Robohelp, Animater, and Photoshop and Oracle’s quarterly critical patch update is releasing on Tuesday, July 19. Expect more updates to come next week with all your favorite Java updates and Oracle middleware products.
Microsoft resolved a total of 88 CVE including a zero-day vulnerability (CVE-2022-22047), 4 Critical CVEs and 4 re-released\updated CVEs.
Windows CSRSS Elevation of Privilege Vulnerability CVE-2022-22047 is a known exploit which puts the OS update this month as a priority. Microsoft is only rating the CVE as Important, which means organizations prioritizing using legacy rating methods could miss prioritize the urgency of the OS update this month. Risk-based prioritization methods take into account known exploited, appearances in malware and ransomware and if an exploit is trending into account helping to more effectively reduce risk.
There seems to be a lot of confusion surrounding the end-of-support and retirement of Internet Explorer last month. Many expected it to be disabled or uninstalled from those systems which are no longer supported. Microsoft is reserving those options for a future cumulative update on those operating systems, but in the meantime opening IE 11 will display an EOL message and direct the user to a Microsoft Edge download. As announced, Microsoft recommends using IE mode in the Edge browser if you really need it for application compatibility. Organizations should be monitoring if and where IE 11 is installed in their organizations and if it is not documented as needed, should be taking steps to remove any instances found as it is not a potential risk.
Microsoft resolved four print spooler vulnerabilities this month (CVE-2022-22041, CVE-2022-22022, CVE-2022-30206, and CVE-2022-30226). All four are rated as Important and no disclosures or exploits. The risk is the potential to impact print functionality. Since Printnightmare, there have been many Print Spooler fixes and in more than one of those patch Tuesday events the changes have resulted in operational impacts. This makes administrators a little gun shy and warrants some extra testing to ensure no negative issues occur in their organization. The bigger risk is if this blocks an organization from pushing the July OS update it could prevent resolving critical vulnerabilities and the Zero Day vulnerability CVE-2022-22047, which is also included in the cumulative OS update.
Microsoft resolved 33 vulnerabilities in Azure Site Recovery that could allow Remote Code Execution, Elevation of Privilege or Information Disclosure. None are publicly disclosed or exploited and all are rated as Important. To successfully exploit an attacker compromise admin credentials on one of the VMs associated with the configuration server or be an authenticated user logged on to the vulnerable system depending on which of the 33 CVEs is being exploited. The concern is in the number of vulnerabilities resolved. They were identified by several independent researchers and anonymous parties which means the knowledge of how to exploit these vulnerabilities is a bit more broadly distributed. The resolution is also not simple. It requires signing into each process server as an administrator, downloading and installing the latest version. Vulnerabilities like this are often easy to lose track of as they are not managed by the typical patch management process.
Adobe released four updates this month resolving 26 CVEs, 15 of which are Critical. The update for Adobe Acrobat and Reader (APSB22-32) is the higher priority as it resolves 15 critical CVEs and of the four Adobe products is the most targeted by threat actors.
Keep an eye out next week as the Java updates start rolling out. Corretto, Adopt OpenJDK, RedHat OpenJDK, and other alternative Java solutions will also be updating to respond to the quarterly release from Oracle. Be ready.
Priorities for July:
- Google Chrome and Microsoft Edge (Chromium-based) – make sure you are up to the latest to resolve the recent zero-day vulnerability.
- July Microsoft OS update is priority this month to resolve the new zero-day vulnerability in CSRSS.
- Ensure you have identified any remaining IE 11 instances and have them documented otherwise remove them. IE 11 is now end of life’d and will become a target.
- Update Adobe Acrobat and Reader to resolve 15 Critical CVEs.