How to Mitigate CVE-2022-0847 (The Dirty Pipe Vulnerability)
Key Takeaways
- The Dirty Pipe vulnerability (CVE-2022-0847) lets unprivileged users overwrite read‑only files by exploiting an uninitialized pipe buffer flag, enabling privilege escalation on Linux kernels 5.8+ and Android 12 devices.
- Affected systems can be identified by checking the kernel version, for example using uname -srm on Linux or the Kernel version field in Android settings.
- Mitigation on Linux requires updating the kernel to 5.16.11, 5.15.25, 5.10.102 or newer.
- On Android, apply the latest manufacturer system updates and use Ivanti tools to automate discovery and patch deployment.
What is the “Dirty Pipe Vulnerability”?
Dirty Pipe vulnerability is a Linux kernel vulnerability that allows the ability of non-privileged users to overwrite read-only files. The vulnerability is due to an uninitialized “pipe_buffer.flags” variable, which overwrites any file contents in the page cache even if the file is not permitted to be written, immutable, or on a read-only mount, including CD-ROM mounts. The page cache is always writable by the kernel and writing to a pipe never checks any permissions. An extensive write-up on the Dirty Pipe vulnerability can be found in the reference links at the end of this blog.
Why is this important?
This enables attackers to perform privilege escalation by overwriting data in arbitrary read-only files and injecting code from unprivileged processes to privileged processes. This can make Linux and Android systems vulnerable to a multitude of malware and other exploits, including ransomware.
Who is affected?
This vulnerability affects endpoints running Linux with a kernel version 5.8 or higher. This includes a multitude of devices running Android 12 and Linux.
How to find out if I am affected?
Linux:
From the Linux command line, run the following command:
uname -srm
Your output should show something similar:
Linux 5.13.19-3-generic x86_64
Android:
To find the kernel version on Android:
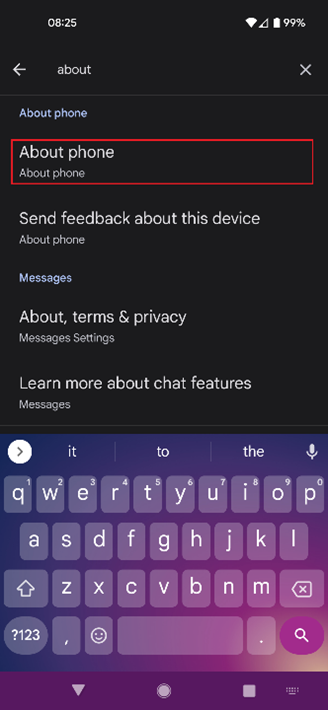
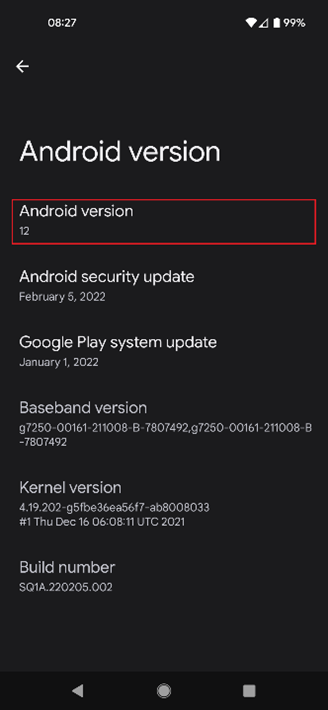
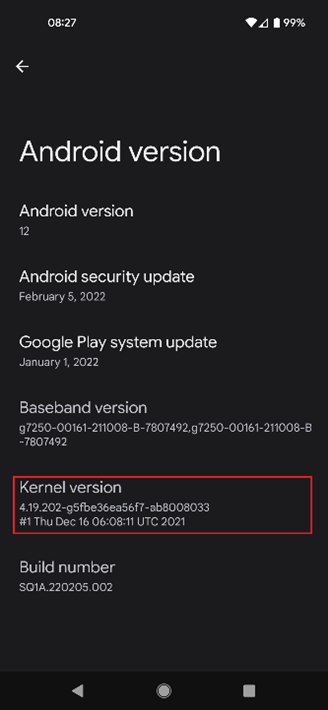
With most generic Android devices, go to setting and search or select “About Phone” -> “Android Version” and you should see the “Kernel version.”
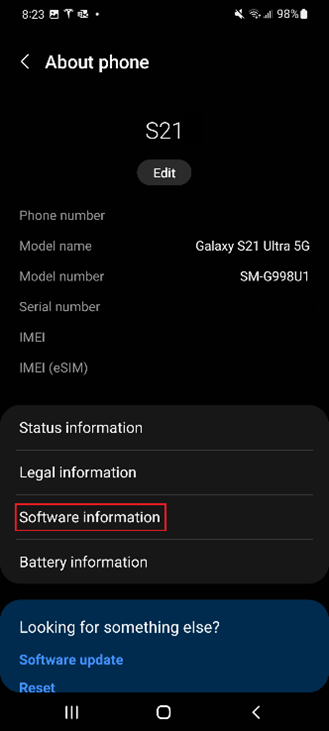
With Samsung, go to settings and search or select “About Phone” -> “Software Information” and your “Kernel version” should be displayed.
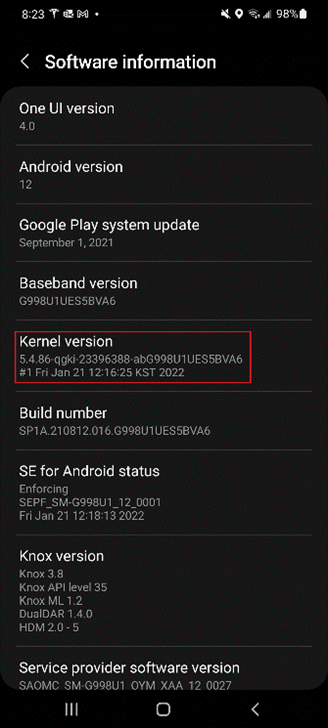
Currently, the most common Android devices affected by this vulnerability are Samsung S22 and Google Pixel 6 series.
How to mitigate Dirty Pipe
Linux
If your endpoint is running a Linux kernel version 5.8 or higher, you should patch your kernel to 5.16.11, 5.15.25 and 5.10.102 or greater. Most distributions have already released a kernel patch. You can run an update with your distro’s package manager to update to the latest kernel.
Ivanti Patch for Endpoint Manager can find which Linux endpoints are affected and automatically apply the vulnerability fix.
Android
On Android, manufacturers are working on applying a critical system update. It is highly recommended to contact your device manufacturer to confirm they are addressing this vulnerability.
You can create reports in Neurons for Discovery to find which Android endpoints are affected.
With Ivanti Neurons for MDM, applying a “System Update” configuration and setting the “Android System Update” to “Automatic” will push the latest manufacture approved system updates to your devices.

