February Patch Tuesday 2022
Key Takeaways
- The February 2022 Patch Tuesday delivered 48 Important-rated CVEs and three reissued fixes, including a kernel elevation of privilege bug with publicly available proof of concept code. It also adds several Print Spooler and Hyper V issues, so test those components thoroughly.
- Firefox 97 and the ESR 91.6 branch each fixed several high-impact bugs, including privilege escalation and remote code execution. Prioritize updating browsers to mitigate these risks.
- The Win32k vulnerability CVE-2022-21882 is now listed as exploited in the wild. A large set of InsydeH2O UEFI firmware flaws have also been disclosed, so apply the latest Windows updates and monitor vendor firmware releases to address these issues.
System Administrators may be feeling a little gun shy after the January Windows OS updates went awry with three known issues. Details in the following out-of-band update on January 18 stated, "This update addresses issues related to VPN connectivity, Windows Server Domain Controllers restarting, Virtual Machines start failures and ReFS-formatted removable media failing to mount,” which did look to stabilize matters.
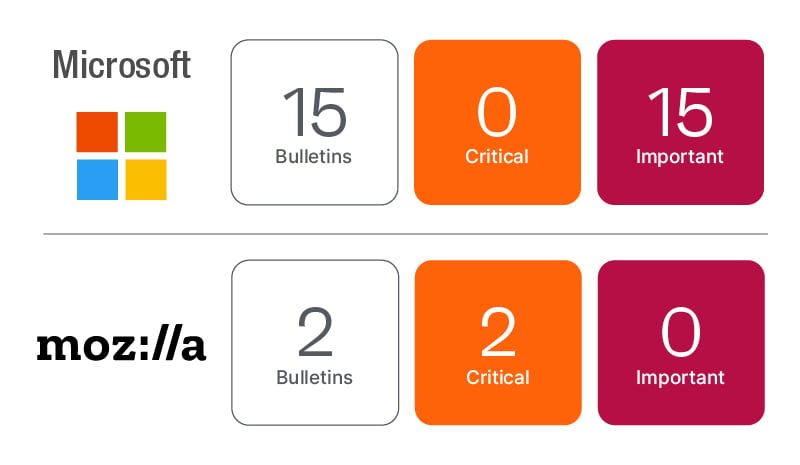
Enter February Patch Tuesday! The lineup this month is smaller than average, with only 48 new CVEs being resolved and three re-released fixes. Another interesting note is that all CVEs this month are only rated as Important. Digging down one more layer here is what we suggest for focusing your testing efforts this month.
Microsoft Patch Tuesday Updates
Microsoft has resolved an Elevation of Privilege vulnerability (CVE-2022-21989) in Windows Kernel that has been publicly disclosed. Exploit code maturity is at Proof-of-Concept. This means much of the initial investigative work for a weaponized exploit has already been done and details could be publicly available to threat actors. This increases the risk of exploitation of this vulnerability.
Microsoft has also resolved four CVEs in Windows Print Spooler which could allow Elevation of Privileges. (CVE-2022-21999, CVE-2022-21997, CVE-2022-22718, CVE-2022-22717) Three of these vulnerabilities had acknowledgments to external researchers. This indicates two things: First, that Print Spooler still has a bit of exposure being cleaned up post-Print Nightmare, and second, that there are several external White Hat researchers still digging in—so you can bet threat actors are likely doing the same. Also, there were several changes to Print Spooler, so test your printer functionality well this cycle.
Hyper-V has two vulnerabilities being resolved this month (CVE-2022-21995, CVE-2022-22712). With the recent issues from January’s updates, a little extra caution in testing is warranted.
Third Party Security Updates
Mozilla Firefox 97 (Security Advisory 2022-04) resolved 12 CVEs, including four High impact vulnerabilities. The release fixes privilege escalation, remote code execution, cross-origin and memory safety issues.
Mozilla Firefox ESR 91.6 (Security Advisory 2022-05) resolved eight CVEs, including three High impact vulnerabilities. The release fixes privilege escalation, remote code execution, cross-origin and memory safety issues.
Additional Vulnerabilities to note
Microsoft revised the Exploited status of CVE-2022-21882 to exploited on January 13, 2022. The Win32k Elevation of Privilege vulnerability has been observed in attacks in the wild in combination with other vulnerabilities, including an even older Elevation of Privilege vulnerability (CVE-2021-1732). This stresses the need to keep up with new security updates and ensure that older vulnerabilities have been resolved as well. CISA has added this vulnerability to the Known Exploited Vulnerabilities Catalog, which has now grown to 352 entries.
Researchers have identified 23 vulnerabilities in InsydeH2O UEFI firmware that could allow security feature bypass for security features like SecureBoot and Intel BootGuard, allow installation of persistent software and the creation of backdoors and communications channels that could be used to steal sensitive data. Expect several firmware updates from many hardware vendors over the coming weeks and months. (CVE-2020-27339, CVE-2020-5953, CVE-2021-33625, CVE-2021-33626, CVE-2021-33627, CVE-2021-41837, CVE-2021-41838, CVE-2021-41839, CVE-2021-41840, CVE-2021-41841, CVE-2021-42059, CVE-2021-42060, CVE-2021-42113, CVE-2021-42554, CVE-2021-43323, CVE-2021-43522, CVE-2021-43615, CVE-2021-45969, CVE-2021-45970, CVE-2021-45971, CVE-2022-24030, CVE-2022-24031, CVE-2022-24069) Sources: https://binarly.io/advisories/index.html, https://thehackernews.com/2022/02/cisa-orders-federal-agencies-to-patch.html
Microsoft Re-Releases
Microsoft updated affected products for a Remote Desktop Services Remote Code Execution vulnerability (CVE-2019-0887), adding the Remote Desktop Client. The original fix was released in July 2019. This CVE also received a revision in December 2021 expanding to cover Windows 11 and Server 2022.
Microsoft re-released a fix in Windows Kernel Memory to resolve an Information Disclosure vulnerability (CVE-2021-34500). The fix was first released in July 2021. The revision notes state, “To comprehensively address CVE-2021-34500, Microsoft has released February 2022 security updates for the following supported editions of Microsoft Windows: Windows 10, Windows 10 Version 1607, Windows 8.1, Windows Server 2012 R2, Windows Server 2012, Windows 7, Windows Server 2008 R2 and Windows Server 2008. Microsoft strongly recommends that customers install the updates to be fully protected from the vulnerability. Customers whose systems are configured to receive automatic updates do not need to take any further action.”
Microsoft has revised affected platforms for an update in Microsoft Diagnostics Hub Standard Collector Runtime, which could allow an Elevation of Privilege (CVE-2022-21871). The fix was first released in January 2022. The revision notes state, “In the Security Updates table, added the following versions of Visual Studio as they also affected by CVE-2022-21871: Microsoft Visual Studio 2019 version 16.9, Microsoft Visual Studio 2019 version 16.7, Microsoft Visual Studio 2017 version 15.9 and Microsoft Visual Studio 2015 Update 3. Microsoft strongly recommends that customers running any of these versions of Visual Studio install the updates to be fully protected from the vulnerability. Customers whose systems are configured to receive automatic updates do not need to take any further action.”