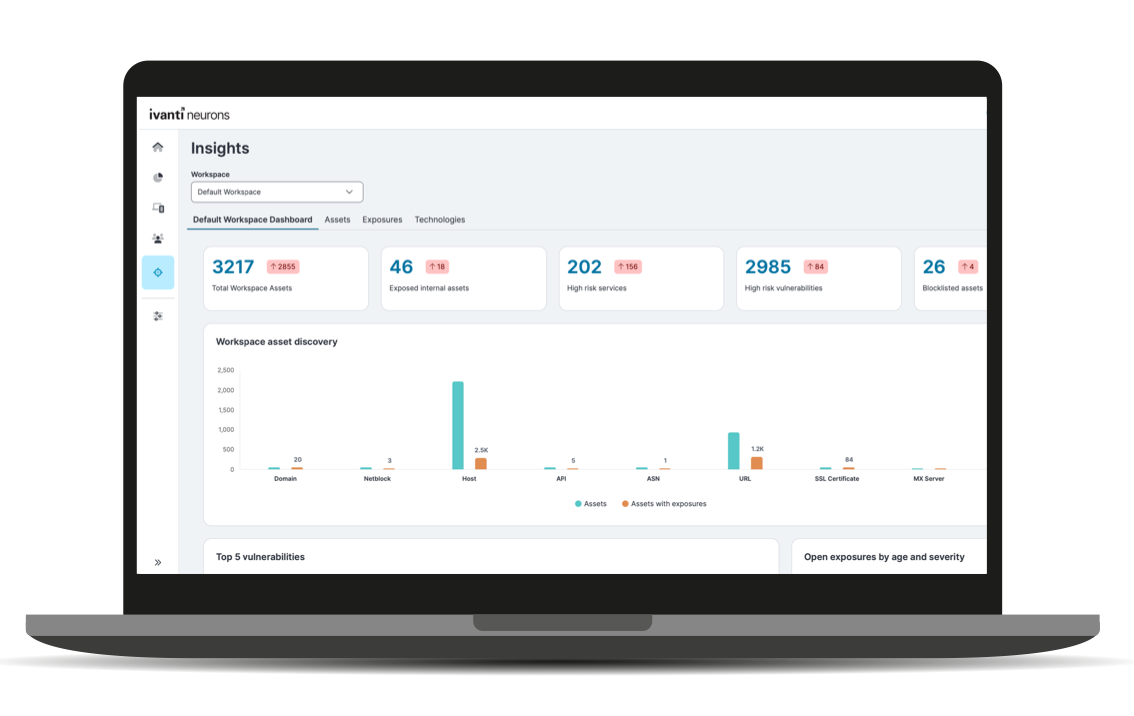
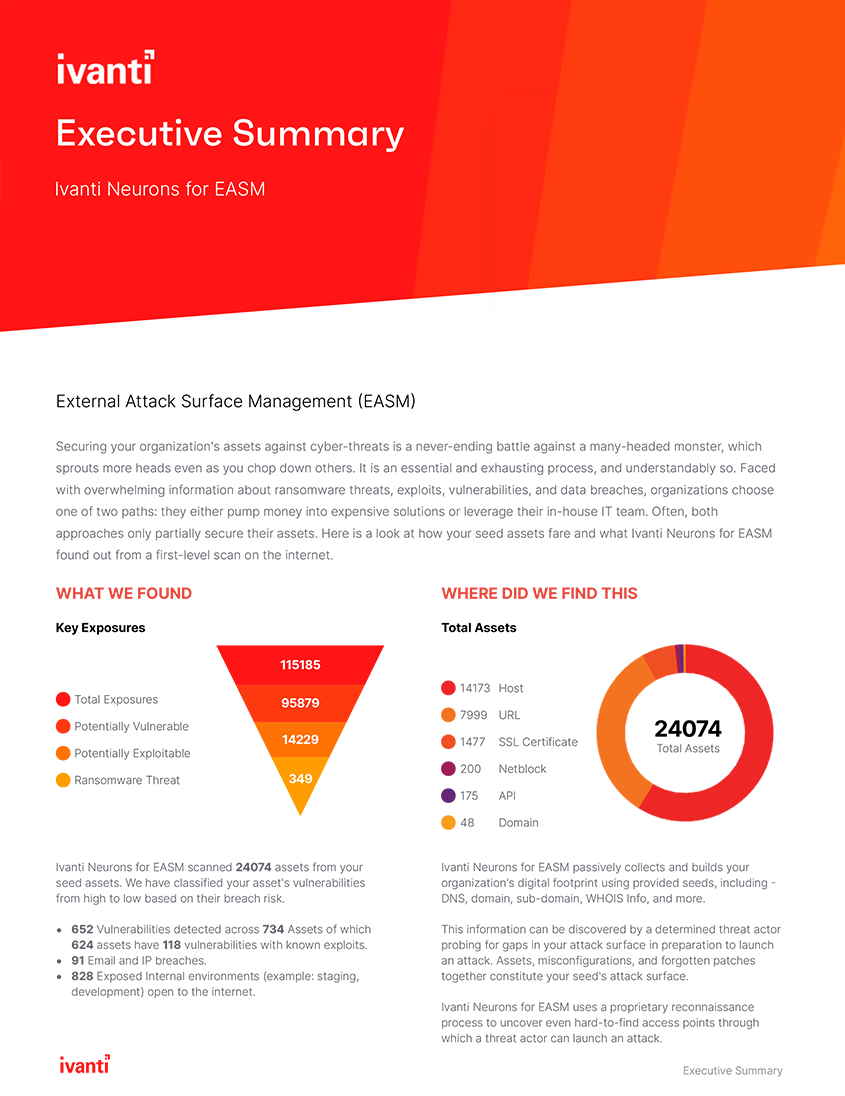
Ivanti Neurons for EASM gives you a powerful set of features in an easy to use, yet capable platform. Discover your external attack surface, prioritize high-risk exposures and address attack surface gaps.
With extensive risk vector coverage, Ivanti Neurons for EASM has you covered by finding vulnerabilities you may not be aware of before threat actors exploit them. Ivanti can even help you remediate the vulnerabilities you find.