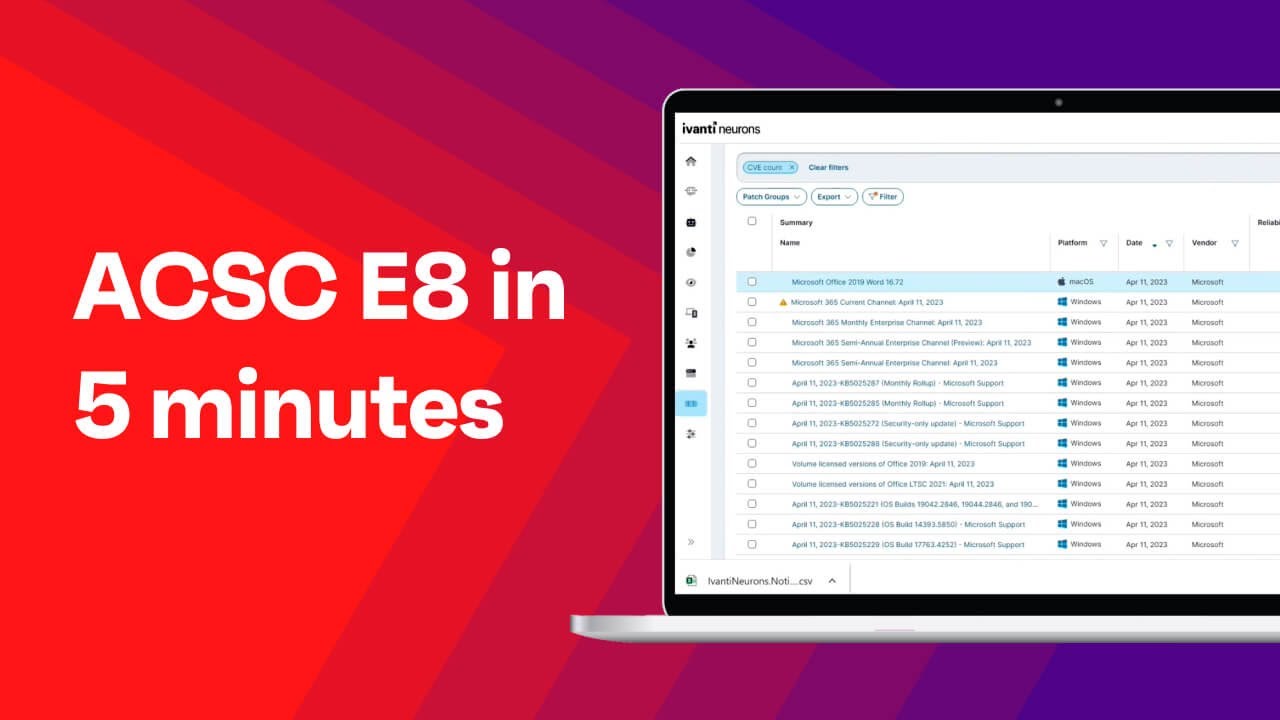
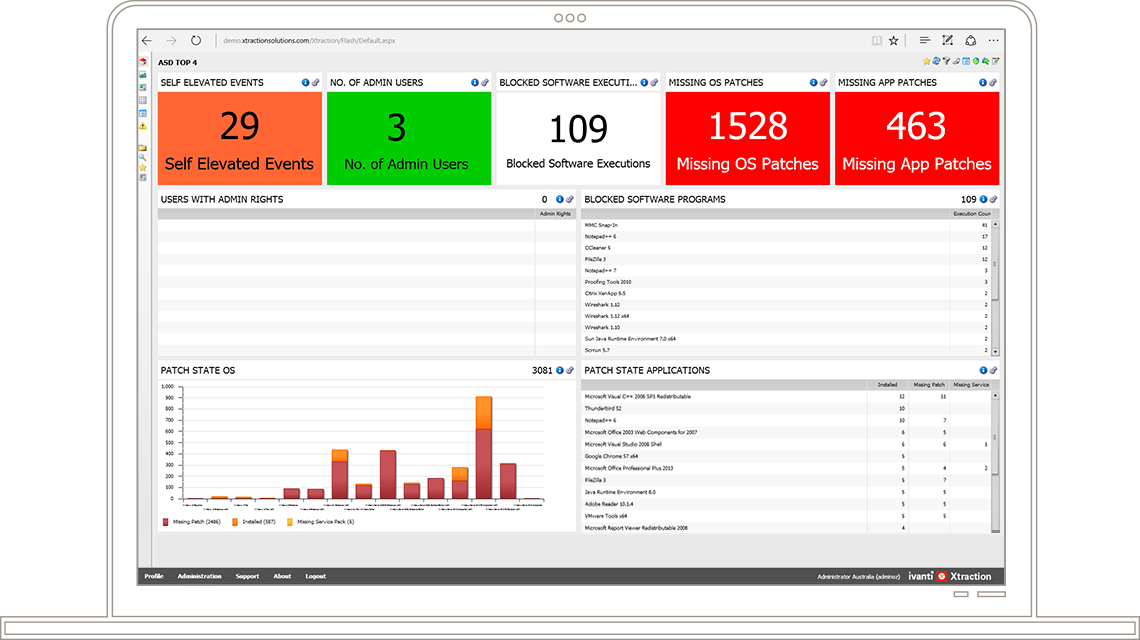
The ACSC Essential 8, (expanded version of ASD Top 4) is a list of essential eight mitigation strategies for businesses and large organisations to prevent cyber security incidents. The Australian Signals Directorate (ASD), in agreement with the Australian Cyber Security Centre (ACSC) has developed the Essential 8 strategies to improve security controls, protect organisations’ computing resources and systems and keep data secure against cyber security threats.
Implement the ACSC Essential 8
Reduce cyber security risks by 85% when you adopt the "Essential Eight" recommended requirements of the ACSC.