WannaCrypt Ransomware: Update for Ivanti Endpoint Security for Endpoint Manager Customers (LDSS)
UPDATE 5/18/17: As widely published, the WannaCrypt ransomware checks for a specific URL and proxy settings before it starts. If the URL is active, it will not run. Furthermore, if a proxy is required to access the Internet, the ransomware will not use the proxy to check the URL. We have released new content that will detect if the endpoint can reach out to the URL, and additional content that will detect if it has a proxy enabled. You may use these updates to detect if the WannaCrypt “kill switch” is effective for each scanned endpoint.
https://community.ivanti.com/docs/DOC-47905
https://community.ivanti.com/docs/DOC-47906
A lot has been written in the past few days about this large ransomware attack. In this post, I’ll provide information and tips on how you can use (if you're not using it already) Ivanti Endpoint Security for Endpoint Manager (formerly Landesk Security Suite) to protect against this attack.
The first line of defense is to protect the endpoint from ransomware damage. Make sure to enable the “auto detect and blacklist crypto-ransomware” checkbox found under the agents’ settings -> Security -> Endpoint Security -> Application Control.
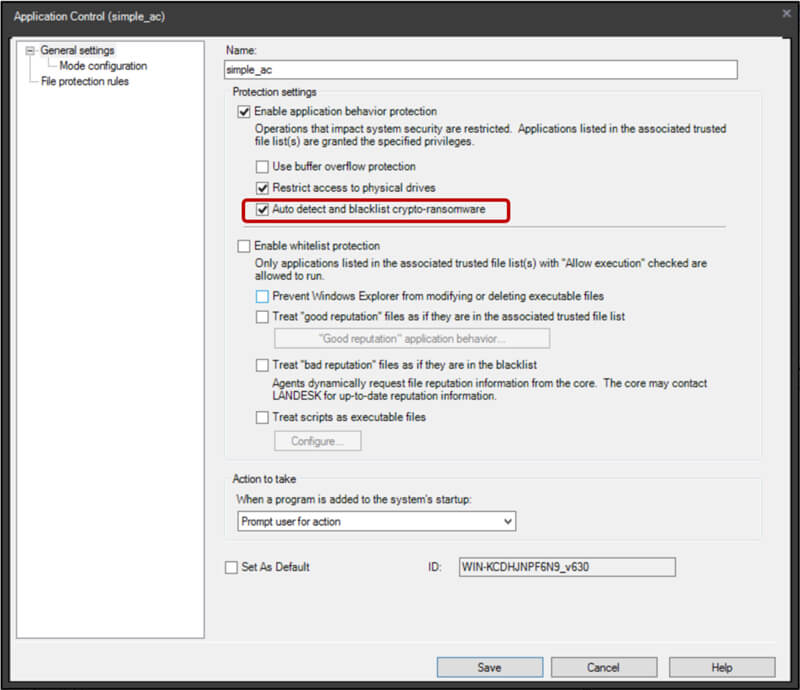
Once enabled, Ivanti Endpoint Security for Endpoint Manager will kill the ransomware encryption process before it encrypts most of your files. In addition, once ransomware is detected, our software automatically blacklists it, making sure no other endpoints can run the ransomware.
WannaCrypt is unique among ransomware, however, as it combines two processes: one for the encryption of files (which will be blocked and blacklisted by the previous feature), and another that scans the network for other machines to infect by exploiting a known Windows SMB vulnerability. Once a potential target is found, the second process exploits the vulnerability and runs the ransomware on the remote machine.
The best way to ensure the second process cannot remotely infect other machines with the SMB vulnerability is to patch all machines in your network. Use the following link to determine which patches you will need to apply to your endpoints: https://community.ivanti.com/docs/DOC-47867
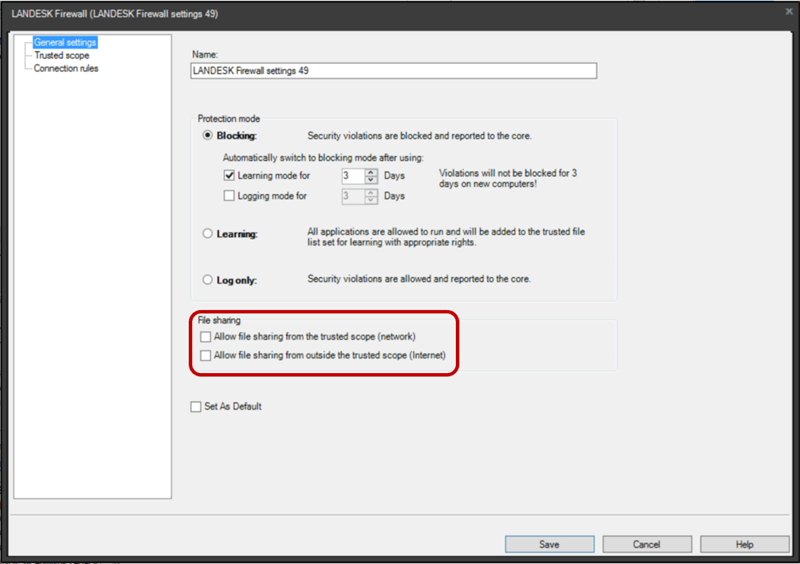
If you cannot patch a machine immediately, Ivanti Endpoint Security for Endpoint Manager provides another capability that will block the ransomware from remotely leveraging the SMB vulnerability to infect unpatched machines. The Ivanti firewall can be used to block any incoming SMB traffic. Once enabled, the protected machine cannot be used to share files over SMB (i.e., no other machine can connect to the protected machine, using the SMB protocol). However, the protected machine can connect to other machines for file sharing (over SMB).
To disable the incoming SMB connections, make sure that both checkboxes under the file sharing section in the Ivanti firewall settings are unchecked, as shown here:
If you currently not using the Ivanti firewall and would like to leverage this protection, you need to add the following connection rules to your Ivanti firewall agent settings. This will make sure the Ivanti firewall is only used to block incoming SMB connections:
- Name: "Deny incoming connection on port 139”, Direction: Incoming, Action: Drop, Protocol: Both, Apply to these local ports: 139 to 139
- Name: "Deny incoming connection on port 445”, Direction: Incoming, Action: Drop, Protocol: Both, Apply to these local ports: 445 to 445
- Name: "Allow any process to connect”, Direction: Outgoing, Action: Accept, Protocol: Both, Apply to these remote ports: 1 to 65535
- Name: "Allow any process to listen for connection”, Direction: Incoming, Action: Accept, Protocol: Both, Apply to these local ports: 1 to 65535
Please note that the rule order is important, as the first match is applied.
As additional protection against ransomware encryption, use file protection rules to prevent the ransomware from encrypting files on the infected endpoint. To learn more, visit this link: https://forums.ivanti.com/s/article/How-to-Use-Ivanti-Endpoint-Security-to-Protect-Against-Ransomware?language=en_US.
For Ivanti AV powered by Kaspersky customers, I recommend you ensure that the System Watcher component is enabled, as this component was proven to block ransomware attacks, including this one.
Check this post for continuous updates of the ransomware attack, and click below stop WannaCrypt and other malware with a free 90-day patch license.

