The Future? It’s Weaponized Malware
Without question, hackers today can have a major impact on critical infrastructure worldwide—hospitals, banking systems, the power grid—especially when they’re partnered with aging, vulnerable technology like legacy software. And they appear to be more and more intent on making that happen.
That’s a nightmarish scenario. But cyber attacks are growing in sophistication, and evolving in intent—in no small part because sophisticated tools originally intended for cyber espionage and warfare are now readily available to any cyber criminal.
WannaCry ransomware crippled computers at hospitals, banks, and businesses around the world. Hospitals in the UK had to turn patients away while they grappled with computers held hostage. NotPetya affected hospitals too— leading to canceled surgeries—and other major organizations like airlines, banks, the Chernobyl nuclear power plant, and a global shipping company, which was forced to shut down container terminals in ports from Los Angeles to Mumbai.
How can security and IT pros protect their organizations from the perils of these kinds of sophisticated, nefarious attacks that are designed to have such a critical impact?
Focused Security Strategies? They Lead to IT Success
There are many parts to a successful security strategy. The most effective use a layered approach that provides multiple defensive options for any given situation. Get rid of the gaps.
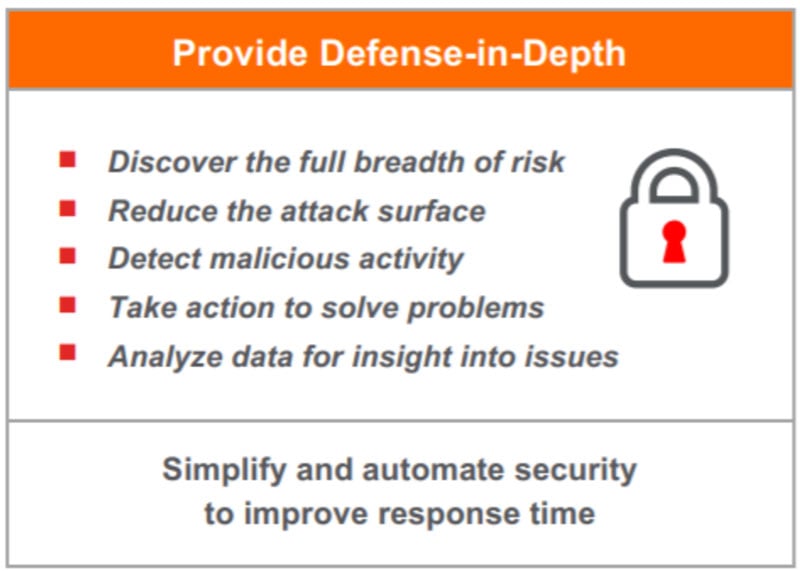
- Provide a complete picture of what is going on in your environment, because you can’t protect (or defend against) anything you don’t know is out there.
- Reduce the attack surface—prevent malware and exploits from executing to give your security capabilities and team a fighting chance to hunt down threats that make it through.
- Detect malicious activity post-execution.
- Respond to and contain malicious activity and potential vulnerabilities.
- And underscore your efforts with rich data that informs your security posture and compliance.
You also need simpler, streamlined tools that automate security processes. Automation can help remove the burden of detection and investigation from your already swamped resources.
And finally, you should look for threat mitigation that protects and even boosts user productivity. Because users who can’t get their work done WILL call the help desk more, and even go around IT with “shadow IT” workarounds, introducing risk into the environment.
Where Do We Go From Here?
To understand why the user is—more often than not—always your weakest link, click back to the previous blog post in the series, The User: Always Your Weakest Link.
For an even fuller picture of the cybersecurity landscape, check out our white paper: What to Do BEFORE All Hell Breaks Loose.
