June Patch Tuesday 2016
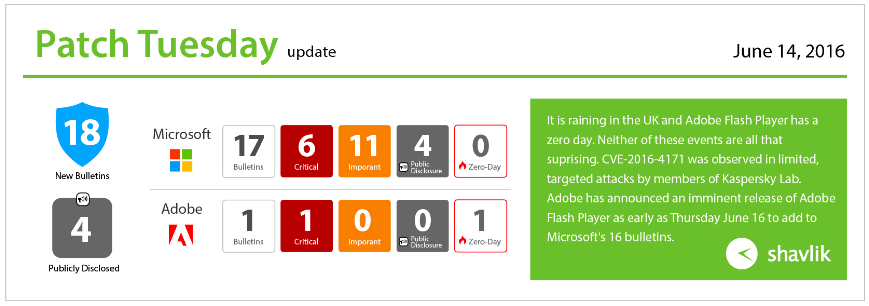
I am chilling up in Daresbury, UK this Patch Tuesday, so instead of working through lunch I am working through dinner. ROOM SERVICE! There are two not so very surprising events this evening. First, it is raining in the UK. Second, Adobe Flash Player has a zero day! Like I said, no surprises. CVE-2016-4171 was observed in limited, targeted attacks by Anton Ivanov and Costin Raiu of Kaspersky Lab. Adobe has announced an imminent release of Adobe Flash Player as early as Thursday June 16, so expect that to come later this week.
Of course, along with a Flash Player update, you should also expect updates to Chrome, Firefox and IE to support the latest plug-in. Also of note, Adobe has announced that the Flash Player distribution page will be decommissioned on June 30, 2016. The urging is for companies to distribute Flash Player to get a proper enterprise agreement in place to distribute Flash Player. Most of you, however, are only concerned with updating Flash Player instances in place for any reason other than your willingness to distribute it intentionally.
For personal use, users are directed to go to https://get.adobe.com/flashplayer/. Businesses looking to distribute Adobe Flash Player internally must have a valid license and AdobeID to download and distribute Flash Player binaries. For more instructions, go to http://www.adobe.com/products/players/flash-player-distribution.html.
Microsoft has released 16 bulletins currently, but with Flash Player releasing later this week there will be 17 total. Of the current 16, five are rated as critical, and the Flash for IE bulletin will also be critical. Altogether, Microsoft is addressing 36 unique vulnerabilities. The overall count across all bulletins is 44, but some of these are across common components used by many products.
I am going to talk about two things in particular in many of the bulletins below. User targeted vulnerabilities and vulnerabilities where privilege management can mitigate the impact if exploited.
User-targeted vulnerabilities are vulnerabilities that would require an attacker to convince the user to click on specially crafted content like an ad in a webpage or an attacked image or PDF. The exploited would be embedded in this specially crafted content allowing the attacker to exploit a vulnerability in the software that is rendering the file. This is a common form of attack to gain entry to a network, since all the attackers need is enough users in that network before they will convince one of them to open their crafty content. Phishing research, described in the Verizon 2016 Breach Investigation Report, states that 23 percent of our users will open a phishing email and 11 percent will open the attachment. If an attacker finds a list of about 10 of your users, they have roughly 90 percent chance of exploiting one of them and getting into your network.
Privilege management can mitigate the impact if exploited. This is a case where the vulnerability does not give the attacker full rights to the system. Instead, they are locked into the context of the user who was logged in. This situation means that if the user is running as less than a full admin, the attacker will have limited capabilities to do anything nefarious.
Many of the bulletins released by Microsoft include vulnerabilities that fit one of both of these categories. MS16-063 is a critical update for Internet Explorer that includes fixes for 10 vulnerabilities. Several of these are targeting a user, and several can be mitigated by limiting user privileges to less than a full admin.
MS16-068 is a critical update for the Edge browser that includes fixes for eight vulnerabilities. This update also includes one public disclosure (CVE-2016-3222). Public disclosures indicate a higher risk of being exploited, as an attacker has some foreknowledge of the vulnerability, giving them a head start on developing an exploit before you can get the update in place. Statistically, this puts it at higher risk of being exploited. Several of these are targeting a user and several can be mitigated by limiting user privileges to less than a full admin.
MS16-069 is a critical update for Windows that includes fixes for Jscript and VBScript for three vulnerabilities. Several of these are targeting a user, and several can be mitigated by limiting user privileges to less than a full admin.
MS16-070 is a critical update for Office and Sharepoint that includes fixes for four vulnerabilities. Several of these are targeting a user and several can be mitigated by limiting user privileges to less than a full admin.
The last of the critical updates this month, MS16-071, is an update in DNS, which includes one fix.
There are three more bulletins of note. Each of these includes a vulnerability that has been publicly disclosed.
MS16-075 (CVE-2016-3225), MS16-077 (CVE-2016-3236) and MS16-082 (CVE-2016-3230). These are all rated as important, but due to the public disclosures, they should warrant more immediate attention.
For a deeper dive into the full Patch Tuesday release, join me tomorrow for the Shavlik Patch Tuesday webinar. I will have a special guest, Gary McAllister from AppSense, who will be discussing concerns around user targeted vulnerabilities and vulnerabilities that can be mitigated with proper privilege management.
