Java Out of Band! This vulnerability fits the profile...
Oracle has announced an out of band Java update to resolve a publicly-disclosed vulnerability that can be exploited over the network, without need for authentication. The vulnerability fits the profile of one that’s more likely to be exploited in 3o days or less.
The Oracle Security Advisory for CVE-2016-0636 provides the CVSS details regarding the vulnerability. The vulnerability has a CVSS of 9.3, access vector is network, access complexity is medium and authentication is none. Confidentiality, integrity and availability are all complete. If you have taken a look at Verizon's 2015 Data Breach Investigations Report, the pattern indicates there is high risk of this vulnerability being exploited in a short time frame.
In the report, there is a section dedicated to indicators of risk, specifically focused on how they help to profile CVEs that are more likely to be exploited quickly. A vulnerability that ends up in the Metasploit framework is the most obvious indicator, since it would easily be replicated by a Threat Actor to exploit the vulnerability. However, based on the CVE information and analysis of over 67,000 CVEs, the Verizon team was able to uncover a pattern for vulnerabilities that have been exploited, including those exploited in less than 30 days.
The majority of vulnerabilities that have been exploited have an access vector of network; authentication would be none, and access complexity of medium or low. If confidentiality, integrity and availability are complete, and have a CVSS of nine or 10, it falls to a more critical time frame where it is likely to be exploited very quickly. (See image of the figure from the Verizon Breach Report)
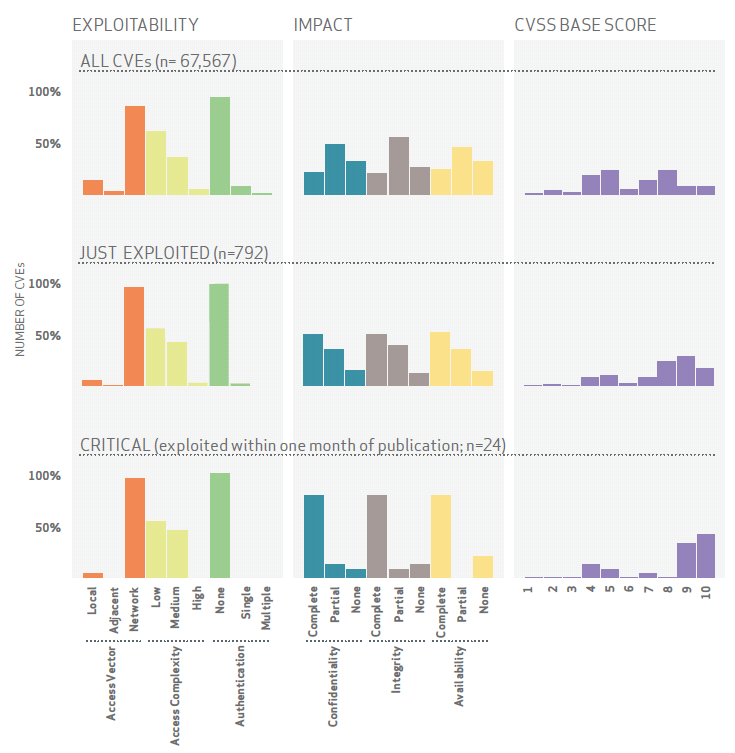
As a precaution, put some urgency on getting this updated as quickly as possible. Aside from meeting the pattern described above, this vulnerability has been publicly disclosed. The Shavlik Content Team is already working on releasing content for this update.