April Patch Tuesday 2017
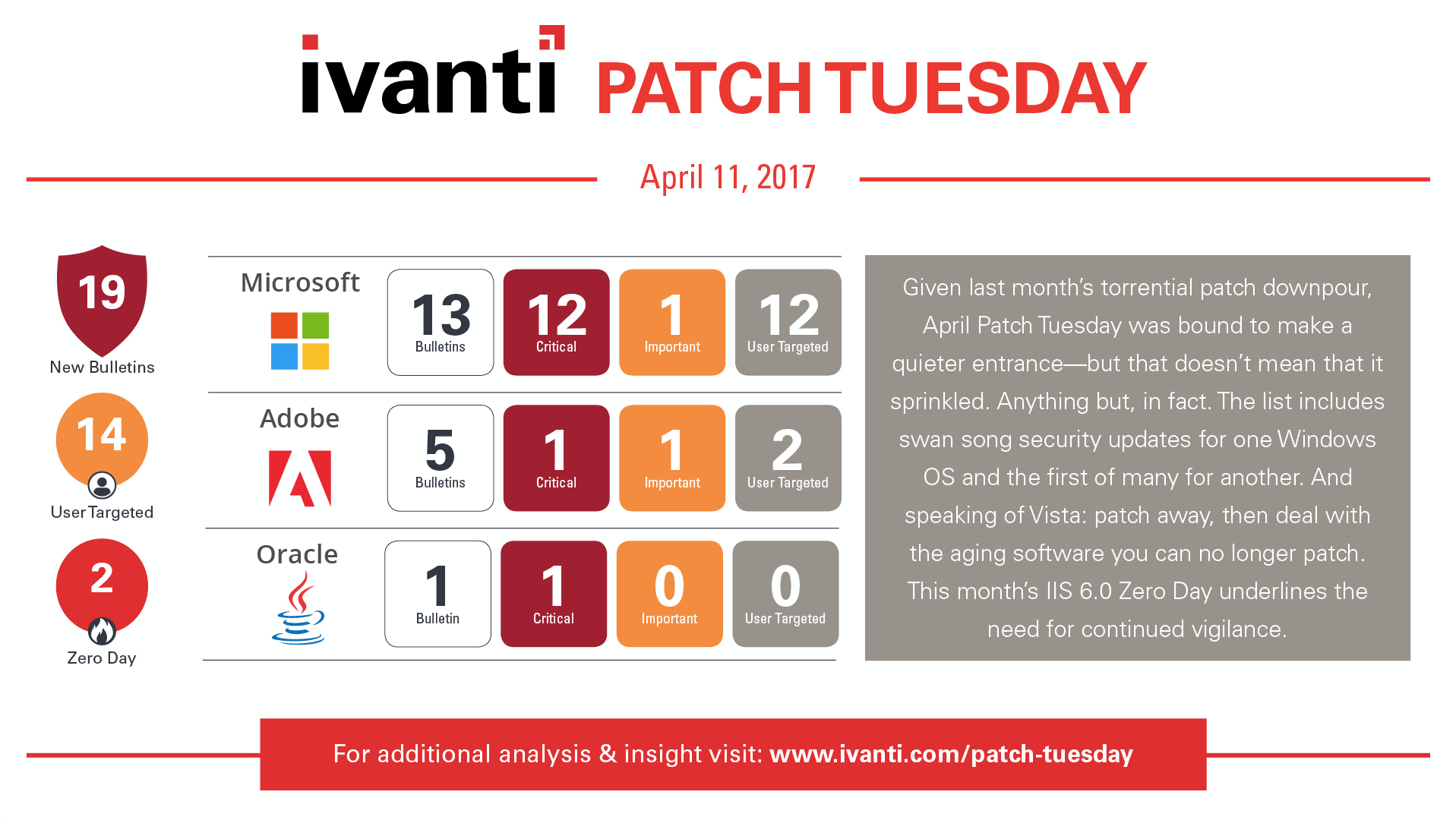
April Patch Tuesday release from Microsoft is only about a third of the size of the March release. There are a total of 46 unique vulnerabilities (CVEs) being resolved, three of which have been publicly disclosed (CVE-2017-0210, CVE-2017-0199, CVE-2017-0203) and two of those have been exploited in the wild or zero days (CVE-2017-0210, CVE-2017-0199).
Be sure to check out all of Ivanti’s patch products:
Patch for SCCM
Patch for Windows
Patch for Linux, UNIX, Mac
Patch for Endpoint Manager
While the number of CVEs is down, there are a lot of interesting changes that have caused anyone trying to research what has just released to have to learn how to run all over again. Microsoft has finally done away with the bulletin pages. You must now use the Security Update Guide, which provides a number of nice filtering options, but you lose a bit of the organization. For instance, to look at all CVEs that are resolved for a single update, you must now look at each individually where the bulletin page had them organized into one place. Likely, it will take a while for people to get used to.
Windows Vista has received its last round of security updates. Yes, Vista has finally reached the end of support.
Windows 10 1703 is available and already has an update to apply! For those of you on Windows 10 1507, keep in mind that it will stop receiving updates at the end of May unless you are on the LTSB.
There are a lot of Hyper-V vulnerabilities this month; 14 of the 46 CVEs address vulnerabilities in Hyper-V.
There are two zero days resolved this month and one of them is for Microsoft Word (CVE-2017-0199)! The other zero day is an elevation of privilege vulnerability in Internet Explorer that would allow an attacker to convince a user to visit a compromised web site that could exploit the vulnerability.
There is an additional zero day that was recently identified in IIS 6 (CVE-2017-7269). This vulnerability will not be resolved as it is in an old version of IIS that runs on Server 2003. More than 600,000 internet-facing servers running IIS 6.0 have the WebDAV module enabled, allowing this vulnerability to be exploited. With a Metasploit module on the way, or already out, you can bet these web servers will become targets if they are not already exploited. In my Patch Tuesday Forecast I talked about EoLed software and the risks of having it running in your environment.
On the non-Microsoft front, there are updates from Adobe and next week (April 18) we will also see the quarterly CPU from Oracle which will include a critical update for Java.
What you should prioritize:
Microsoft has rated the following updates as critical:
- Cumulative Rollup for Windows 10 and Server 2016
- Monthly Rollup for Windows 7, 8.1, Server 2008 R2, Server 2012 and Server 2012 R2 or
- Security Only Update + Cumulative Update for IE for Windows 7, 8.1, Server 2008 R2, Server 2012, and Server 2012 R2
- .Net Framework
- Adobe Flash for IE
- Microsoft Office
Adobe has rated the following updates as critical:
- Adobe Flash Player
- Adobe Acrobat and Reader
Oracle will be releasing updates on April 18, which will include a critical update for Java.
As always, we will have more details on the Ivanti Patch Tuesday webinar on Wednesday, April 12 at 10:00 a.m. CT. Talk to you then.