March Patch Tuesday 2022
Key Takeaways
- CISA’s Known Exploited Vulnerabilities Catalog grew to 489 entries, with a recent addition of two zero day flaws in Mozilla Firefox that were patched on March 4. Ivanti tracks 60 of those CVEs as being used by Russian backed threat actors, many tied to ransomware.
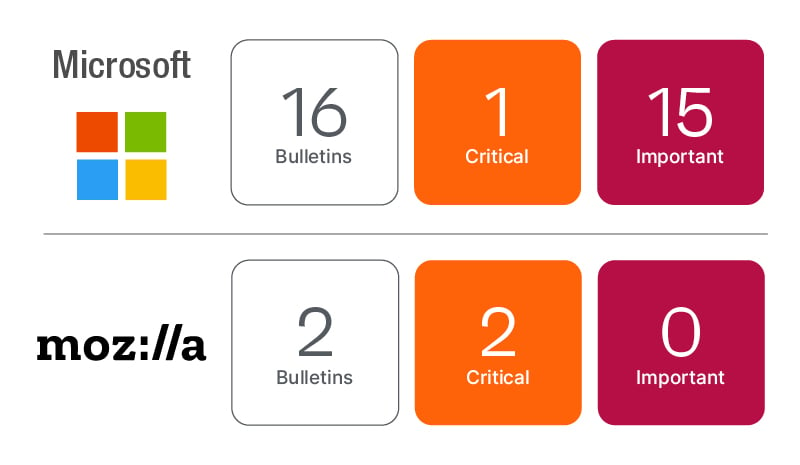
- Microsoft’s March updates include 74 CVEs, three critical. The Windows OS patch contains an RDP remote code execution and a Fax Scan elevation flaw that have proof of concept exploits, so the update should be applied as a critical priority.
- Mozilla Firefox and ESR updates, although rated high, should be treated as critical.
- Microsoft’s Exchange and SMBv3 patches address remote code execution flaws that require immediate deployment. Blocking TCP 445 at the network perimeter is recommended for SMB protection.
March Patch Tuesday got off to an early start this month with CISA adding 95 vulnerabilities to their Known Exploited Vulnerabilities Catalog. Yesterday another 11 vulnerabilities were added including two Zero Day vulnerabilities in Mozilla Firefox that were resolved in a release on Friday, March 4th. This brings the CISA catalog up to 489 total CVEs that organizations should be ensuring get mitigated or remediated as quickly as possible. With the invasion of Ukraine by Russia a heightened awareness around cybersecurity threats has also brought more attention to the vulnerabilities being used by known Russian threat actors. Ivanti Neurons for Risk Based Vulnerability Management is currently tracking a total of 60 CVEs that have been identified as being used by Russian-backed threat actors. Many of these have been tied to Ransomware.

Microsoft’s March Patch Tuesday includes 74 total CVEs, 71 of which are new unique CVEs, 3 of which are rated as Critical, and Mozilla resolved an additional 8 unique CVEs (not including Friday’s Critical release including two Zero Day vulnerabilities). Microsoft re-released 3 CVEs expanding affected products and documentation.
The good news on the Microsoft front this month is no additional Zero Day vulnerabilities have been identified. Most of the updates are rated as Important but given the cybersecurity war currently being waged, organizations should assume a higher level of risk for many vulnerabilities being resolved. For example, the Windows OS update has a pair of publicly disclosed vulnerabilities including an RDP Remote Code Execution vulnerability (CVE-2022-21990) and a Windows Fax and Scan Service Elevation of Privilege vulnerability (CVE-2022-24459) which have reached proof-of-concept exploit code maturity. This puts both vulnerabilities at a higher risk of exploit. The Windows OS update this month should be treated more like a critical update due to these risks.
The Mozilla Firefox and Firefox ESR updates are both rated as High but given the two Zero Day vulnerabilities resolved last Friday, Ivanti’s guidance is to treat these as Critical to ensure those known exploited vulnerabilities get plugged as quickly as possible. Consider it a defense in depth precaution.
Microsoft Exchange has been updated to resolve 2 CVEs including a Critical Remote Code Execution vulnerability (CVE-2022-23277). The RCE vulnerability does require authentication but can be remotely exploited over the network without user interaction. This means an attacker can trigger malicious code in the context of the server’s account through a network call.
Microsoft resolved a Remote Code Execution vulnerability in SMBv3 Client\Server that is getting some attention. It has not been publicly disclosed or known to be exploited at this time, but the vulnerability could allow an attacker to remotely exploit the vulnerability from off network over TCP 445 if it is exposed on the perimeter. The guidance in CVE-2022-24508 calls out additional steps to “protect my network” by blocking TCP port 445 at the network perimeter.
- TCP port 445 is used to initiate a connection with the affected component. Blocking this port at the network perimeter firewall will help protect systems that are behind that firewall from attempts to exploit this vulnerability. This can help protect networks from attacks that originate outside the enterprise perimeter. Blocking the affected ports at the enterprise perimeter is the best defense to help avoid Internet-based attacks. However, systems could still be vulnerable to attacks from within their enterprise perimeter.
Microsoft also made an update to KB5004442 just after the February Patch Tuesday event. This article discusses a Security Feature Bypass in Windows DCOM Server. Hardening changes were made to DCOM in June 2021, but these changes are disabled by default. Coming in June 2022, the hardening changes will change to enabled by default, but with ability to disable via a registry key and change to enabled by default with no ability to disable come March 2023. Microsoft is giving ample time to ensure organizations have time to test these hardening changes as legacy applications could be impacted. The February 17 warning serves as Microsoft’s one year notice that you need to get things tested and fixed\updated if you find impacts.