August Patch Tuesday 2022
Key Takeaways
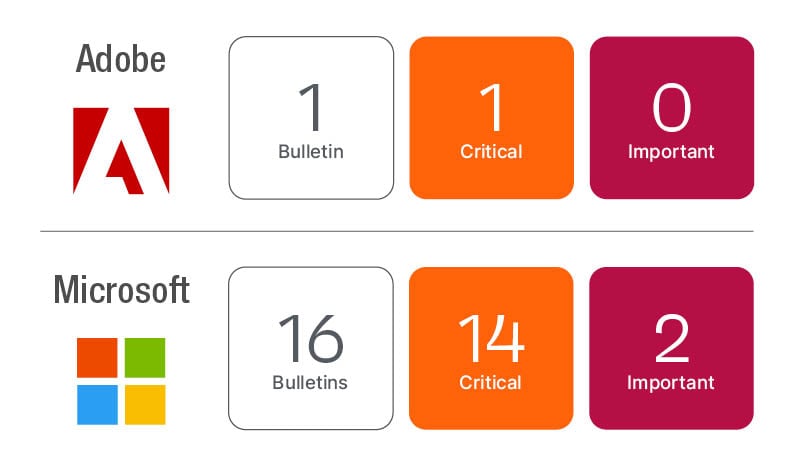
- Microsoft’s August Patch Tuesday addresses 123 CVEs, including a publicly exploited zero day in the Windows Support Diagnostic Tool (CVE-2022-34713) and an Exchange information disclosure (CVE-2022-30134). Both should be prioritized for immediate deployment.
- Adobe released five updates, with the Acrobat and Reader priority 2 update fixing three critical CVEs and requiring immediate response. The remaining four updates also contain at least one critical fix and should be applied as soon as practical.
- Windows 7 and Server 2008/2008 R2 have only six months of ESU remaining. Windows Server 20H2 ends support on August 9 and Windows 10 21H1 ends on December 13 2022.
- Organizations should plan migrations or upgrades soon to avoid loss of security updates.
Microsoft has released their Patch Tuesday update, which includes 123 unique CVEs this month, 121 of which are new CVEs. Two are revisions to older .Net updates to include .Net 3.5 on Windows 8.1 systems (CVE-2022-26832 and CVE-2022-30130). The Servicing Stack Updates advisory ADV990001 was updated. Additionally, advisory ADV200011 was updated with a standalone security update (KB5012170), which implements improvements to Secure Boot DBX. Of the 121 new CVEs addressed this month, there is a zero day (CVE-2022-34713) and a publicly disclosed CVE (CVE-2022-30134). Seventeen of the resolved CVEs are rated as Critical.
Affected products
- Windows Operating System
- Microsoft Office/O365
- Azure Sphere, Site Recovery, Real Time OS and Batch Node Agent
- .NET Core
- Visual Studio
- Exchange Server
Zero day vulnerabilities and public disclosures
Microsoft has resolved a remote code execution vulnerability in Microsoft Windows Support Diagnostic Tool (MSDT) (CVE-2022-34713), which has been publicly disclosed and observed in attacks in the wild. This is a user-targeted vulnerability, meaning the attacker can target the user with a variety of social engineering tactics, such as sending a specially crafted file via email or convincing the user to click on hosted web content specially crafted to exploit the vulnerability. The vulnerability affects all Windows OS versions and is rated as Important by Microsoft. Due to the public disclosure and known attacks targeting the vulnerability, it is recommended to treat this as a higher priority.
Microsoft resolved an information disclosure vulnerability in Exchange Server (CVE-2022-30134). The public disclosure does not provide functional exploit code. Aside from updating Exchange Server, there are additional steps needed to prevent an attacker from targeting this vulnerability. More details on the issue have been provided on the Exchange blog, and more information on how to implement Windows Extended Protection is available on GitHub.
Third-party updates
Adobe has released five updates today addressing 26 CVEs, including a priority 2 update for Adobe Acrobat and Reader (APSB22-39). Priority 3 updates for Adobe Commerce, Illustrator, FrameMaker and Premiere Elements have also released. All five updates include at least one Critical CVE fix, but Adobe priorities help to shift priorities by risk. Priority 1 indicates that the release includes a vulnerability that is actively being exploited, Priority 2 is urgent for products commonly targeted by threat actors, and Priority 3 is lower severity of CVEs or products less likely to be targeted by threat actors. Based on their prioritization, the Adobe Acrobat and Reader update should get immediate response. The other four updates should be addressed as soon as practical, but are not as urgent.
Microsoft OS lifecycle and supportability changes
There are only 6 months of ESU releases remaining for Windows 7 and Windows Server 2008/2008 R2, counting the August Patch Tuesday update. You should be planning to retire these legacy operating systems soon. Microsoft has plans to support a year 4 for Azure environments only. All other 2008/2008 R2 support will end after the January 2023 Patch Tuesday release.
Windows Server 2012/2012 R2 will be reaching its extended support end date on Oct 10, 2023. This may seem like a far-off event, but many organizations are planning budgets for 2023 now so it is an ideal time to think about your organization's plans for this server platform. If you plan to retire systems before the end date, then you have just over a year to ensure your 2012/2012 R2 workloads are planned for migration to newer platforms. If you know you will need to extend support, then starting to budget for ESU support now will ensure you have budget set aside come October 2023.
Microsoft is ending their Windows Server Semi-Annual Channel (SAC) support this month. Windows Server 20H2 reaches end-of-support on August 9 and will be the last of the SAC versions. There will be no more security updates for this version. Microsoft has shifted to their Long-Term Service Channel (LTSC) for server support, which they plan to release every 2-3 years and provide 5 years of regular support with an additional 5 years of extended security support. Windows Server 2019 and Windows Server 2022 are the latest LTSC versions, with regular support until January 2024 and October 2026 respectively. If you are running Windows Server 20H2 you are encouraged to update to one of the LTSC releases, but be advised that you will need to install a clean update from scratch, so plan accordingly.
Windows 10 21H1 Home, Pro, Enterprise and Education editions end-of-support date is December 13, 2022. Timing-wise the end date is falling in the middle of many organizations' IT change freeze and end-of-year holiday season. It's best to plan ahead to ensure you have upgraded these systems 21H2 or 22H2 (when it releases) and avoid a January scramble to upgrade these systems.
Microsoft is also removing the temporary mitigation for CVE-2021-33764 this Patch Tuesday. This mitigation allowed administrators to configure domain controllers to work with RFC-4456 incompatible printers. There have been several updates to KB5005408 throughout the year to help administrators identify and manage these non-compliant printers. Per Microsoft, effective August 9, “Smartcard-authenticating printers and scanners must be compliant with section 3.2.1 of the RFC 4556 specification required for CVE-2021-33764 after installing these updates or later on Active Directory domain controllers.” This could be disruptive if you have not planned and updated your printers. If you’re not sure about the impact for your environment, the August preview released on July 21 removes the mitigation and will block printing on non-compliant devices.
August prioritization
- Windows OS has a number of CVEs associated with the update and the known exploited/publicly disclosed (CVE-2022-34713).
- Exchange Server has a public disclosure (CVE-2022-30134), which also has additional steps to fully resolve the security vulnerability.
- Adobe Acrobat and Reader resolves three Critical CVEs and is a commonly targeted application.

