April Patch Tuesday 2022
Key Takeaways
- Spring4Shell continues to be actively exploited, with attackers using it to spread Mirai botnet. Update Apache Tomcat and any Spring Framework deployments earlier than 5.2.20 or 5.3.18, then apply vendor patches.
- Microsoft released 117 CVEs, including one exploited and one publicly disclosed Elevation of Privilege bug. The Windows OS update covers all critical, exploited and publicly disclosed issues, so prioritize updating Windows, Adobe Acrobat Reader, Chrome and Firefox to mitigate the bulk of April risk.
- The Print Spooler and DNS Server each received a large number of fixes (15 and 18 CVEs). Test them thoroughly after patching, and note Oracle quarterly critical patch update due April 19.
For those in the northern hemisphere, April is often viewed as a month of spring renewal – a time to do some spring cleaning. April Patch Tuesday is looking to propagate this age-old tradition as Spring4Shell continues to see some attention both by adversaries and vendors. Attackers are exploiting the Spring4Shell vulnerability to spread Mirai Botnet malware. Attacks observed by Trend report systems configured with Spring Framework versions before 5.2.20, 5.3.18, JDK version 9 or higher and Apache Tomcat are being targeted.
Apache Tomcat updates released on April 1 resolved CVE-2022-22965. Updates from others vendors including VMware was also released and vendors like Microsoft released guidance for protecting against Spring4Shell. Make sure to spend some time evaluating your organizations’ exposure to Spring4Shell (CVE-2022-22965) and deploy recently released updates where needed.
There have been several third-party application updates in early April. Mozilla Firefox 99 released on April 5 resolving 11 security fixes including 3 high severity CVEs. Google Chrome released on Monday, April 11 resolving 11 security fixes including 8 high severity CVEs.
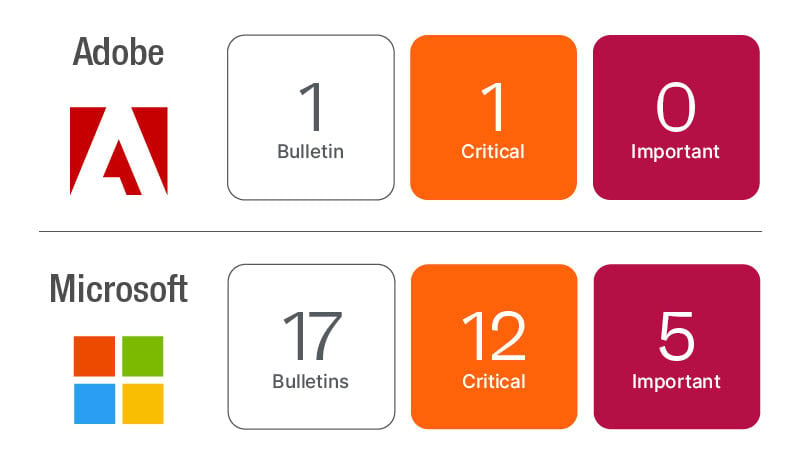
As far as updates that released on April Patch Tuesday, Adobe released APSB22-16 for Adobe Acrobat and Reader resolving 62 unique CVEs, 35 of which are rated as Critical.
Microsoft has resolved 117 new unique and expanded 2 prior CVEs for April Patch Tuesday, and 9 of the new CVEs are rated as Critical. There are also one publicly disclosed (CVE-2022-26904) and one exploited (CVE-2022-24521) CVE this month. The good news is 8 of the Critical CVEs and both the publicly disclosed and exploited vulnerability are covered by the Windows OS update this month. A significant amount of this month’s risk can be resolved by updating the Windows OS, Adobe Acrobat and Reader, Google Chrome and Mozilla Firefox.
Oracle’s Quarterly Critical Patch Update will occur on April 19th. Keep this in mind as you begin your patch maintenance this month.
Microsoft Patch Tuesday Highlights
Microsoft resolved one Zero Day vulnerability this month. A Zero Day vulnerability is defined as a CVE that has been exploited in the wild prior to an update being made available. CVE-2022-24521 is an Elevation of Privilege vulnerability in Windows Common Log File System Driver affecting all Windows Operating System versions. The vulnerability is only rated as Important even though it is known to be actively exploited. Organizations that utilize a Risk-based approach to prioritizing vulnerabilities have an advantage vs using just vendor severity and CVSS score, which can be misleading as the algorithms do not take enough real-world risk indicators into account. Alone, this Elevation of Privilege vulnerability may not be a high risk, but chained with additional vulnerabilities could be an effective combination. Monitoring exploits, usage by malware and ransomware families and if the CVE is trending are additional metrics used by Risk-based vulnerability prioritization systems to better articulate risk.
Microsoft resolved one Publicly Disclosed vulnerability this month. A Public Disclosure is a risk indicator. It means enough information may have been made publicly available prior to or simultaneous with the patch being made available. This often gives threat actors an advantage to create a weaponized exploit much quicker than defenders can plug the vulnerability. CVE-2022-26904 is an Elevation of Privilege Vulnerability in Windows User Profile Service. The exploit code maturity for this CVE is listed as Functional meaning working code samples were included in the disclosure. This gives attackers a head start on developing a weaponized exploit. This vulnerability affects all Windows Operating System versions.
Areas to test thoroughly
There are 15 CVEs being resolved in the Print Spooler this month. In February Patch Tuesday there were 5 CVEs resolved in the print spooler and some impacts were seen with a few printer vendors. 15 CVEs is a lot of change in code and warrants a little extra focus in your testing this month.
Windows DNS Server had 18 CVEs resolved this month and warrants some careful testing due to the number of changes in code.