Security Awareness: Time to Rethink Your Security
Summer is one of my favorite seasons of the year: backyard barbecues, sunshine for days, the TV listening to my conversations.
Wait, what? You heard correctly. On March 7, 2017, what is arguably the largest code release of zero-day attacks, malware, vulnerabilities, and processes—used by the CIA to exploit everything from Smart TVs to iPhones—was provided online for free.
THE NEW AGE OF DIGITAL WARFARE THAT AFFECTS YOU
The WikiLeaks description for “Zero Day" Vault 7 reads: ”This extraordinary collection, which amounts to more than several hundred million lines of code, gives its possessor the entire hacking capacity of the CIA.”
This extraordinary collection, which amounts to more than several hundred million lines of code, gives its possessor the entire hacking capacity of the CIA.
While extraordinary, this isn’t the first time a cyber arsenal has been released to the open Internet. In October 2016 the NSA leaked some of its tools through a group calling themselves the ‘Shadow Brokers.’ These included similar tools, but seem to be aimed at “penetrating foreign computer networks,” rather than the latest Vault 7 toolset owned by the CIA.
Initially, the NSA release was thought to be the careless leftovers of a hacking attempt on a server. However, and more significant, the NSA files “appear to have come from a source repository… meaning the leak came from inside a closed environment.”
WikiLeaks claims to have obtained Vault 7 from the CIA in the same fashion: Defense contractors allegedly handed them the files, hoping to “initiate a public debate about the security, creation, use, proliferation and democratic control of cyber weapons.” Regardless of the methods, these tools and processes are now in the wild.
Defense contractors handed [WikiLeaks] the files, hoping to “initiate a public debate about the security, creation, use, proliferation and democratic control of cyber weapons.”
Panic mode engage?
>> OPESEC: THE PRACTICE OF PRIVACY AND SECURITY
If anything, these events should drive us toward a better focus on privacy and security practices both personally and throughout the enterprise. There’s no security ‘Easy Button’ for our digital lives, but there are methods and tools to make us more aware and adaptable. This new reality of staying protected in an always-on world is called operational security (OPSEC).
This new reality of staying protected in an always-on world is called operational security (OPSEC).

I bet you’re thinking, “Operational security? What is this technical jargon you speak of?!” In fact, you’re not far off. OPSEC is derived from a military initiative to identify, protect, and promote the protection of information. A Google image search gives a propaganda-like feel to the phrase, but ultimately OPSEC is about three simple things (modified from the original definition to be more user friendly):
- Identify information:
Determine what information is critical (and what isn’t), and what the capabilities, activities, limitations (vulnerabilities), and intentions are. - Analyze the strengths and vulnerabilities within that information:
Understand if the information contains any attempt to disrupt or compromise your privacy or security, and what the inherent risks are. - Act on what’s identified:
This could be something as simple as not picking up an unknown USB drive you found, or ensuring a certificate of a secured website is valid.
OPSEC is derived from a military initiative to identify, protect, and promote the protection of information.
Even before this was officially introduced in the 1960s, OPSEC was part of the WWII culture:
>> OPESEC IRL (IN REAL LIFE)
In practice, OPSEC is like a muscle or talent: The more you practice, the better and more automatic your response will become. Releases like WikiLeaks’s Vault 7 or the NSA leak won’t end. The only option is to arm yourself with a mindset of being privacy and security aware.
Let’s look at some real-world examples of how the OPSEC process works in practice:
Example One: Free USB Drive!
We’ve all been there: You’re walking the street or even your workplace, and you see it—a free USB drive! Who cares what was previously on it. You’ll simply erase it (after looking through it, of course) and add it to your collection.
Let’s quickly go through the OPSEC process.
- Identify information:
The USB is free, but it’s capability when plugged into my computer is unknown. These drives can be harmless, but malicious USB activity has even gone full Hollywood (Mr. Robot, anyone?). Limiting my exposure to these threats does seem like the right thing to do, because the overall intention is unknown.
STRIKE 1
- Analyze the strengths and vulnerabilities within that information:
Because the USB’s original identity is unknown, the likelihood of a strong threat is very possible; and because the USB’s contents are unknown, the risk factor is off the charts. At this point you must assume that the unknown is a threat.
STRIKE 2
- Act on what’s identified:
This step should now be simple: You can’t identify the original intentions, the possibility of a threat is very likely, and the risk is high.
STRIKE 3
- OPSEC ANALYSIS: THROW IT AWAY OR DESTROY IT
Releases like WikiLeaks’s Vault 7 or The Shadow Brokers won’t end. The only option is to arm yourself with a mindset of being privacy and security aware.
Example Two: ATTENTION! You’ve Got Mail.
Have you ever wondered how to protect yourself against email scams or threats? Called ‘phishing,’ these attempts focus on stealing information through common websites, or unknown execution of malware through downloading embedded or attached documents.
An example would be something like the following (names removed):
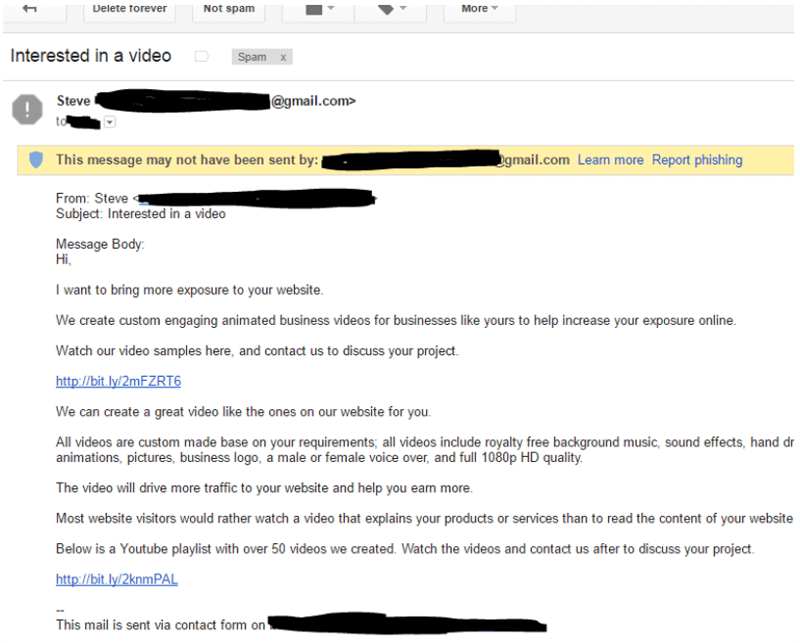
Let’s quickly go through the OPSEC process:
- Identify information:
Google has flagged this as a potential phishing email (that’s why it’s in the spam filter). The email text mentions increasing exposure to my website, but I haven’t reached out to anyone about creating a video, and I don’t know anyone named Steve. Overall this seems suspicious.
STRIKE 1
- Analyze the strengths and vulnerabilities within that information:
The email is unrecognizable. The links provided aren’t anything I recognize. They seem to be shortened and unassociated with YouTube. Also, it states I should contact them to discuss the project, but there isn’t any contact information.
STRIKE 2
- Act on what’s identified:
This step should now be simple: You can’t identify the original sender, you didn’t solicit any kind of video for your website, and the possibility of a threat by clicking the links or responding to ‘Steve’ is very likely.
STRIKE 3
- OPSEC ANALYSIS: REPORT AS SPAM AND DELETE IT!
As a follow-up, here’s what the links contained, including information gathered on ‘Steve’:
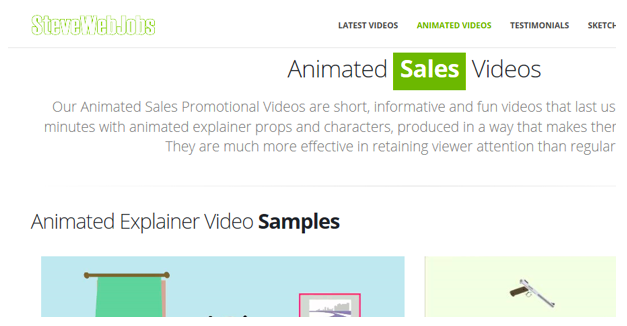
- SteveWebJobs.com is a website marketing animated videos. Much of the website is one page, with multiple contact forms. In fact, there are some examples from YouTube:
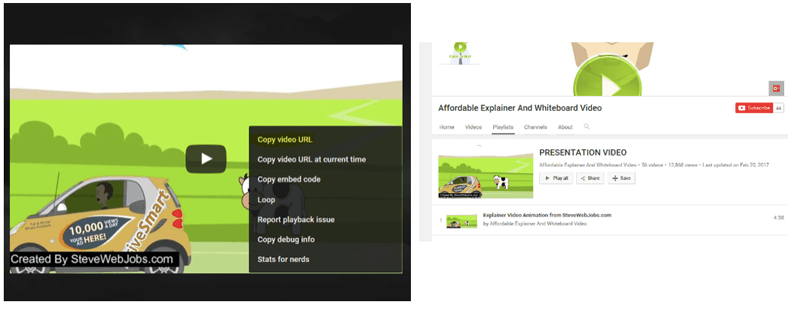
- I right clicked the top YouTube video and found the following YouTube page, which looks legit with a considerable history and number of video uploads:
- I still can’t find info on ‘Steve.’ I then went back to the webpage and looked at the page code and found more YouTube links—one of which took me to a different YouTube page:
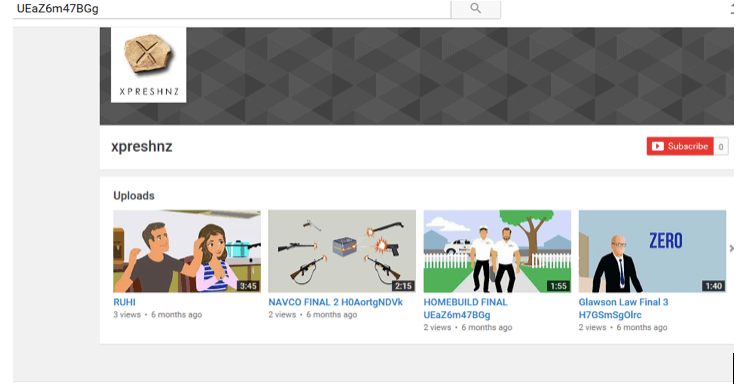
- I the googled the user name ‘xpreshnz’ and found multiple references to a Vimeo channel, and a LinkedIn profile which I traced to a page and picture of ‘Steve’ (not his real name):
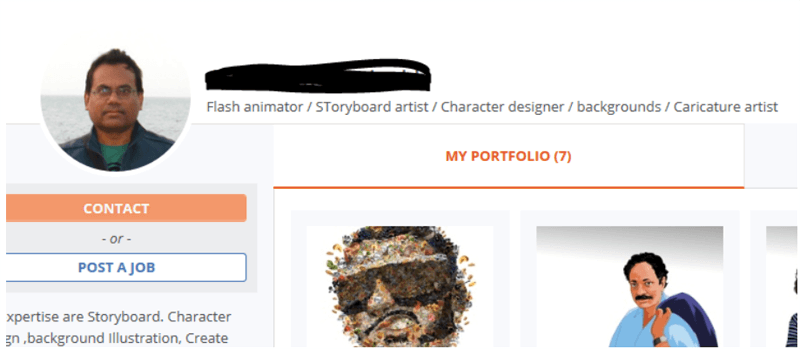
And there he is!
- To further verify this is he, I performed a reverse image search on that headshot, which came back empty:
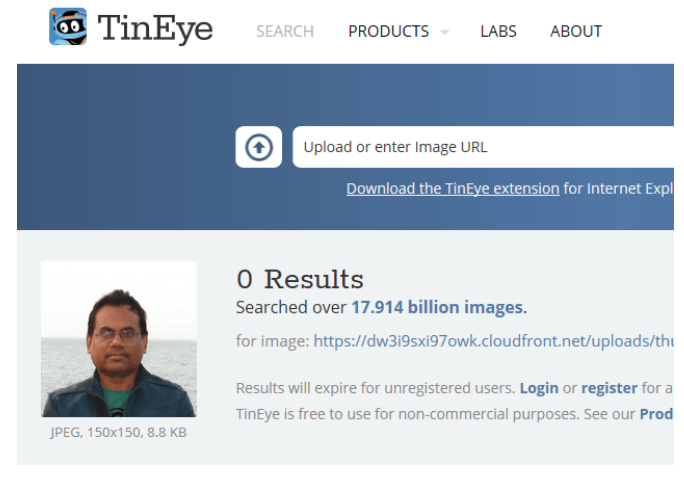
- So ‘Steve’ is a freelancer based in Kolkata, India, and seems to be pushing his brand through SteveWebJobs.com and a pseudonym YouTube account called “Affordable Explainer And Whiteboard Videos.”While not malicious in content, the methods and content present a conflicting view of the true nature of this individual and business approach.
>> START PRACTICING OPSEC NOW
With OPSEC defined and two examples of how OPSEC works daily, choose to make the summer of 2017 the time when you take control of your privacy and security. The tools, news headlines, and ‘digital noise’ you’ll continue to hear won’t disappear. They’ll simply get louder, more numerous, and more impactful to our daily lives.
The tools, news headlines, and ‘digital noise’ you’ll continue to hear won’t disappear; they’ll simply get louder
To recap:
- Leaks of tools and processes (Vault 7 and the Shadow Brokers) have put us and our devices at increased risk.
- OPSEC (Operational Security) can help safeguard and prevent many incidents by identifying and qualifying the strength of potential threats and vulnerabilities, and then acting accordingly.
- OPSEC can be practiced daily. Whether it’s at home reading Facebook and browsing online, or at work reading emails and interacting with other colleagues over the Internet, practice, practice, practice.
Here are some resources to become educated about OPSEC:

